VMware ESXi users: What to know about CVE-2021-21974
Vulnerability prioritization is a topic that we have covered in previous blogs. A common question that is asked of Cyber Asset Attack Surface Management (CAASM) platforms such as Noetic is, “what is my scope of risk (or asset susceptibility) to a critical vulnerability for a given operating system or software application?”.
Given the huge volume of vulnerabilities that exist in an enterprise environment, security teams must make decisions based on the best information they have—the severity and exploitability of the vulnerability, what potential impact it could have on the organization, how exposed is it to the internet and more.
VMware ESXiArgs Ransomware: What happened?
While we see this most often in the case of zero-day vulnerabilities, sometimes it is the result of a new wave of attacks focused on an older vulnerability that had not been effectively patched, this is what we are currently seeing with the VMware ESXi hypervisor flaw.
Hackers exploit CVE-2021-21974
This vulnerability, CVE-2021-21974, is present in VMware’s implementation of a service delivery protocol in ESXi called Open Service Location Protocol (OpenSLP). The vulnerability gives unauthenticated attackers the ability to remotely execute malicious code on affected systems. This vulnerability was initially disclosed by VMware in February 2021, and a patch for it was released at the same time.
However, despite the available patch, 12% of VMware ESXi servers remained unpatched. In turn, the ESXi vulnerability has seen widespread use by attackers and in early February, the French Computer Emergency Response Team (CERT-FR) flagged a significant global ransomware campaign based on the exploit, known as “ESXiArgs.”
This ransomware outbreak was so severe, affecting thousands of servers worldwide, that on February 8, CISA and the FBI released a recovery script to help organizations recover their files and patch the exploit. A new version of the malware has since been published that bypasses the script, and research from Censys shows a continuing growth in new ESXiArgs infections.
Using CAASM tools to help provide visibility into exploitable vulnerabilities.
CAASM tools like the Noetic platform can play an important role in helping security teams to understand both the location and exploitability of critical vulnerabilities such as the ESXi exploit. The Noetic platform aggregates and correlates asset and vulnerability data from multiple sources including cloud management, EDR, CMDB, and application security. This aggregated dataset, showing not only asset technical data, but also cyber relationships and attack paths, provides unique insights that enable prioritization based on business need and cyber risk.
Two examples of how Noetic can improve coverage for vulnerabilities such as CVE-2021-21974 are:
- Identify vulnerability scanning coverage gaps: Vulnerability scanning technologies are effective at enumerating flaws by CVE, but they are only as effective as their coverage of the estate. Noetic can identify coverage limitations that exist within web or agent-based vulnerability scanners by analyzing the ‘negative space’ between AWS machines, or network ranges in comparison to the vulnerability scanner. This will commonly identify a 20–30% coverage gap, which can be easily closed by updating the scanning range and triggering an updated network scan.
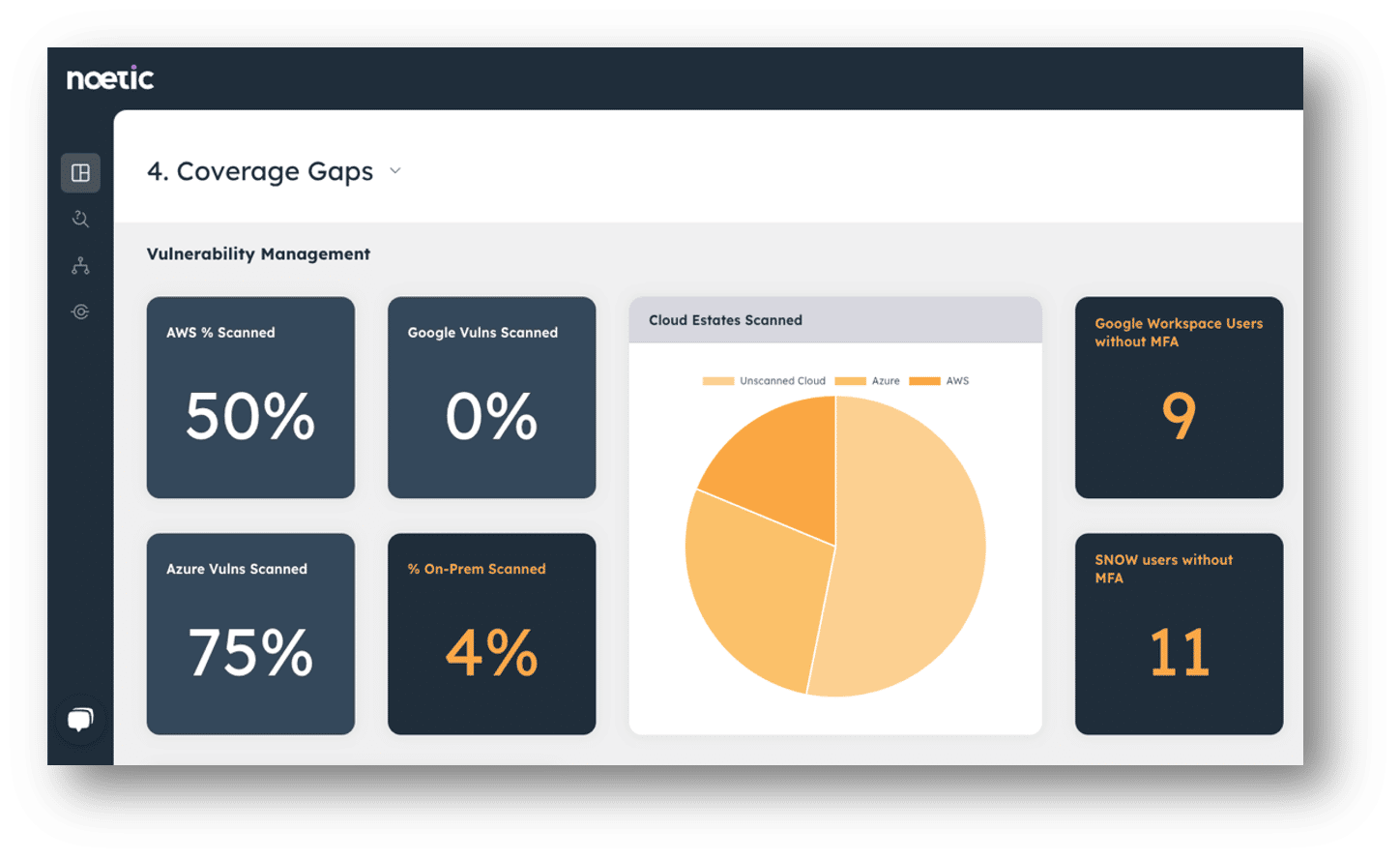
- Prioritize vulnerabilities by asset criticality or exposure: By correlating vulnerability data with other asset information, Noetic can help security teams to identify servers that may be particularly susceptible to attack, or that present a meaningful risk to the business if they are inaccessible through ransomware. Noetic achieves this by mapping vulnerabilities, machines, networks, users, datasets, and more so that the relationships between them can be easily understood and queried.
An example of this could be the query below, which delivers a list of exploitable machines that support business critical applications, a clear priority for patching and remediation.
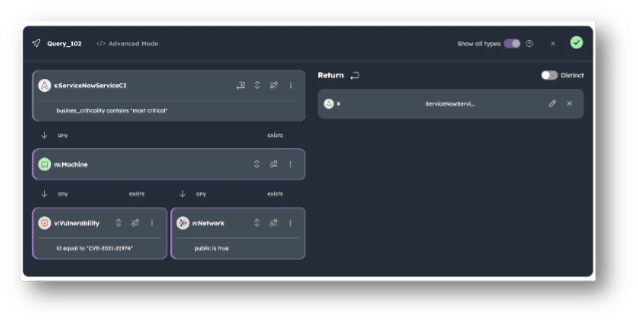
This example brings back a curated list of machines, and the relevant service & owner information for:
- Machines with the CVE-2021-21974
- Machines hosting a “most critical” service according to ServiceNow CMDB
- Machines in a network marked as “public”
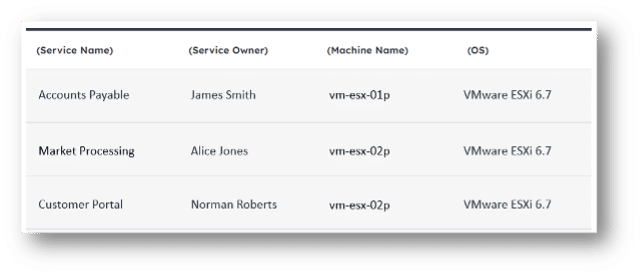
With this information, security now has a very specific list of high-priority machines to work together with colleagues in DevOps and IT to patch. In Noetic, this could drive the automated creation of a ticket in Jira or ServiceNow, or simply an email or Slack message to kick off the process.
As security teams work to identify and remediate the ESXi vulnerabilities inside their organizations, they need to know where to start. Noetic gives them that context, working with their existing patch and vulnerability management stack to help prioritize based on overall risk to the business.
To learn more about Noetic’s market-leading CAASM solution and its different use cases, register for an upcoming live demo.
