5 Ways to Leverage CAASM Throughout the M&A Lifecycle
Mergers and acquisitions (M&A) are pivotal moments in today’s fast-paced business environment, marking significant transitions and growth opportunities for organizations. According to research from PwC, there were 27,003 M&A transactions completed worldwide in the first half of 2023. In the dynamic landscape of M&A activity–where companies are constantly evolving and reshaping their strategies–ensuring a robust cybersecurity foundation throughout the M&A lifecycle is critical.
The Importance of Cybersecurity in M&A
One of the often underestimated yet fundamentally crucial aspects of this process is cybersecurity asset management. In fact, a staggering 65% of IT and business decision makers have expressed regrets over M&A deals due to cybersecurity concerns. Therefore, it should come as no surprise that 81% agree that they are putting more focus on a target’s cybersecurity posture than in the past (Forescout).
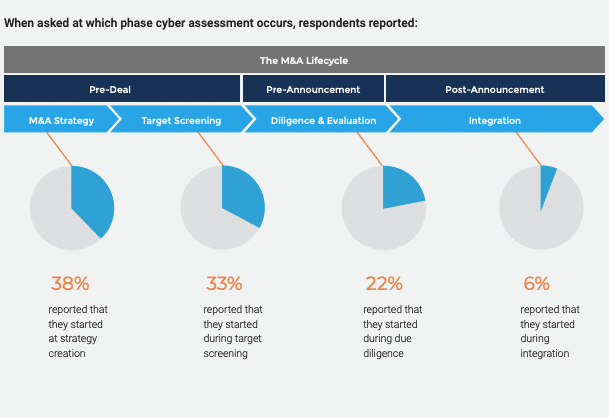
Source: Forescout, The Role of Cybersecurity in Mergers and Acquisitions Diligence
Pre-Deal
Cybersecurity issues within the target company can have significant financial implications for the acquiring organization. If the target has suffered previous data breaches or is non-compliant with required cybersecurity regulations, it may lead to costly legal battles, fines, and the need for extensive remediation efforts.
The target screening process in the M&A lifecycle is a crucial phase where potential acquiring companies assess the desirability and suitability of a target company for acquisition. Integrating cybersecurity considerations during this stage enables strategic decision-making by ensuring a comprehensive understanding of the risks and opportunities associated with the potential merger or acquisition.
However, despite the benefits of considering cybersecurity in these beginning stages, only 36% of IT & business decision makers agree their team is given time to review the company’s cybersecurity standards, processes and protocols before their company acquires another company.
Pre-Announcement
M&A deals are not just about acquiring assets and talent; they also involve inheriting risks. However alarmingly, over half (53%) of business leaders find unknown devices during the integration of a new acquisition. For the acquiring company, it’s essential to have a thorough grasp of the target company’s security and risk posture because understanding the risks associated with the target’s digital assets, systems, and data helps in developing strategies to mitigate those risks effectively.
Post Announcement
A comprehensive understanding of the target’s cybersecurity measures ensures that operations remain uninterrupted post-acquisition. Assessing cybersecurity readiness helps in planning for any necessary adjustments to maintain business continuity and avoid disruptions that could impact customers, employees, and partners.
The Role of CAASM in the M&A Lifecycle
From beginning stages to post-merger, cyber asset attack surface management (CAASM) solutions equips organizations with the intelligence they need better, more informed decisions throughout every step.
- Scoping & Risk Assessment
CAASM enables a systematic evaluation of the target company’s posture by mining, aggregating, and correlating the data from their existing tools and technologies. This gives the acquiring organization the chance to develop contingency plans and ensure business continuity prior, during and after the transition.
- Due Diligence
CAASM has proven to be instrumental in making informed decisions, providing the necessary insights to evaluate existing systems, assess technological health, and estimate the costs associated with upgrading or securing the technology landscape.
- Data Privacy & Compliance
Understanding how the target company manages sensitive data and complies with industry-specific regulations is vital. CAASM assists in this by offering a detailed view of the target’s data management and compliance protocols. Ensuring compliance with data privacy laws and other regulatory requirements is critical to prevent legal complications and potential fines post-acquisition. CAASM ensures that the merged entity continues to adhere to relevant laws and regulations, mitigating risks associated with non-compliance.
- Integration Planning
Effective integration planning is essential for a seamless M&A transaction. The comprehensive insight provided by a CAASM platform facilitates smoother integration, minimizing disruptions to business operations, and enables the consolidation of cyber assets such as networks, applications, and databases—optimizing resources, reducing duplication, and enhancing operational efficiency and cost-effectiveness.
Additionally, Noetic’s Unified Model is designed to provide simple insights from aggregated data from different security tools. It harmonizes data from different formats and sources into a unified and coherent format, allowing security and risk leaders to analyze risk continuously—regardless of the variety of tools, services, and spreadsheets they’re currently operating from.
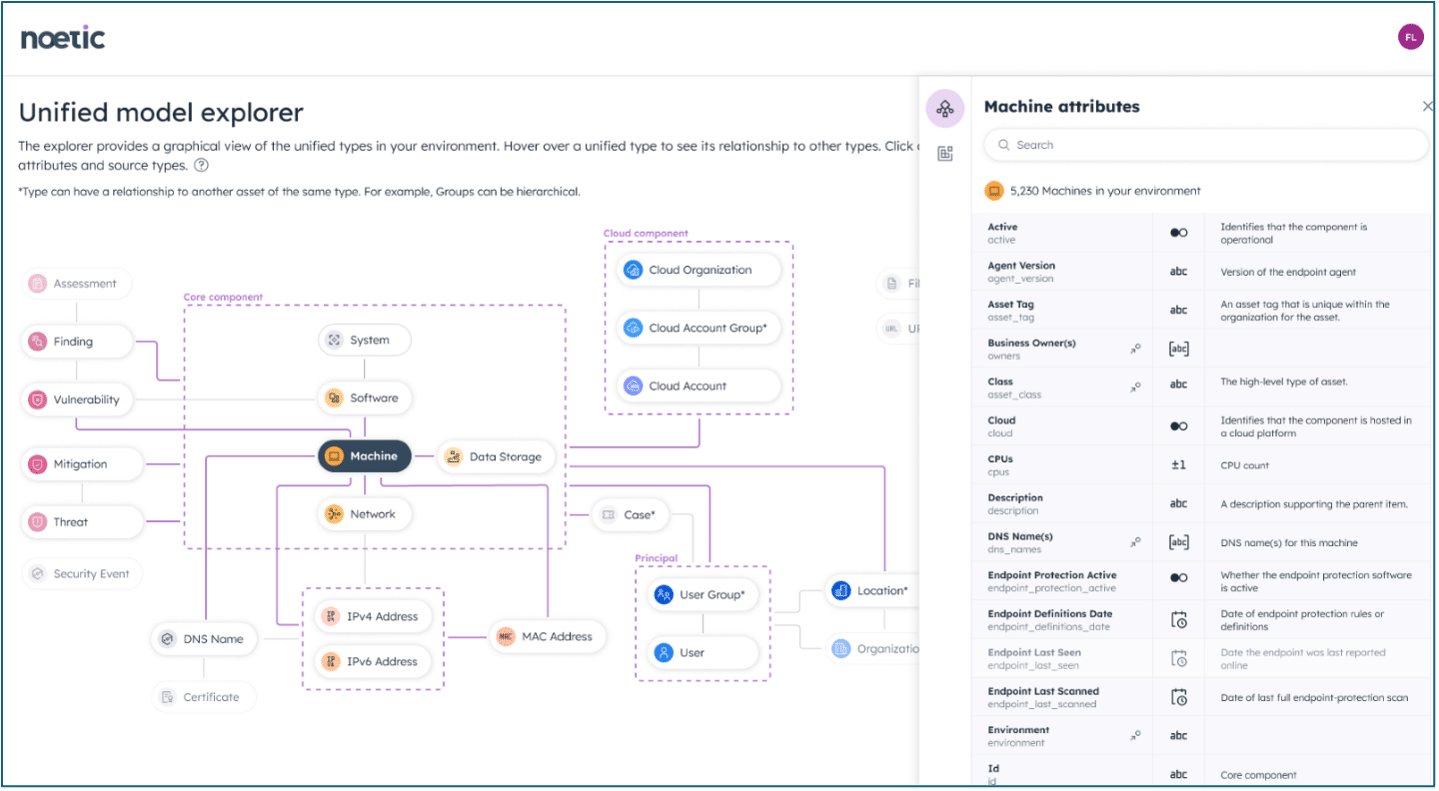
Learn more about the Unified Model Explorer.
- Continuous Monitoring
Once the ink has dried, and the merger or acquisition is complete, the work is far from over—and this is where CAASM’s role of being a consistent, holistic view of risk continues. A CAASM solution ensures that the merged organizations remain proactive in monitoring its cybersecurity landscape for emerging risks and vulnerabilities. It aids in implementing continuous monitoring mechanisms, enabling the organization to stay updated with industry trends and threat intelligence. This proactive approach allows for timely adaptation and reinforcement of security measures, maintaining a robust cybersecurity posture in the ever-changing threat landscape.
In today’s digital age, cybersecurity is a top concern in any M&A activity. Neglecting cybersecurity considerations during this process can lead to potential consequences, including data breaches, financial losses, and damage to your organization’s reputation. To avoid these risks, organizations should prioritize cyber asset attack surface management (CAASM) at every stage of the M&A lifecycle, from pre-announcement strategy and due diligence to integration planning and post-merger operations.
Discover the immediate benefits of adopting Noetic for M&A in the HardenStance Cyber Security Innovators report that details the beginning of our journey with the security team at Gamma Telecommunications.
