Threat and Vulnerability Management Solutions
See the full picture.
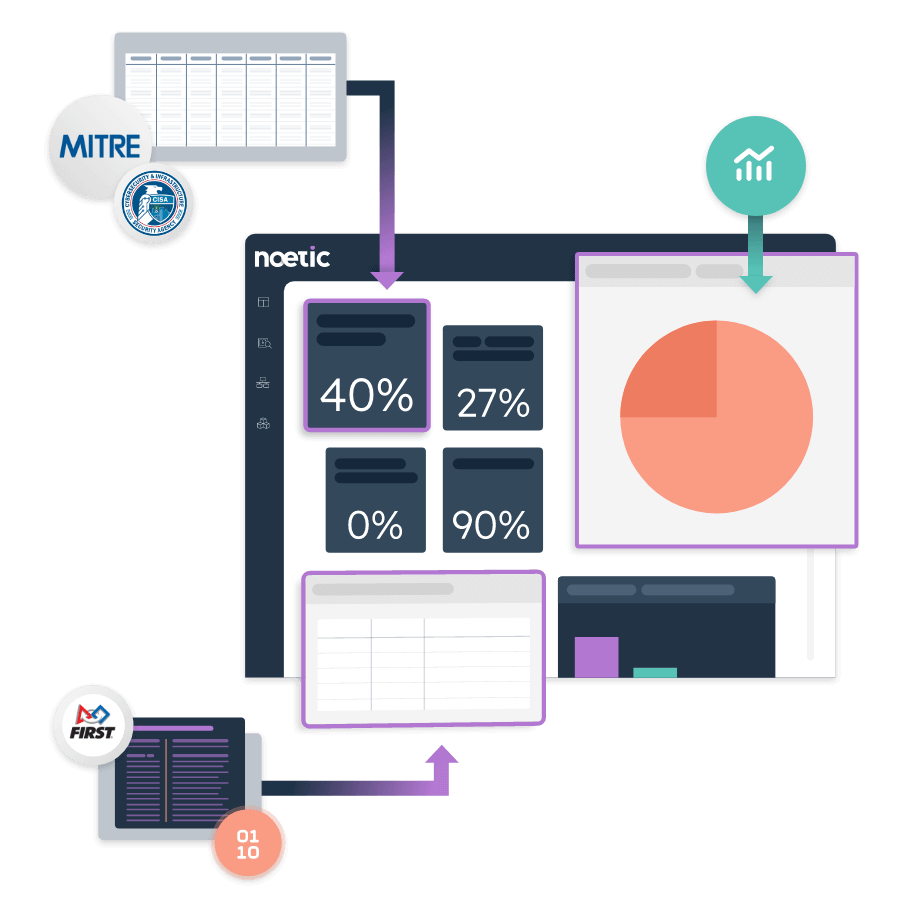
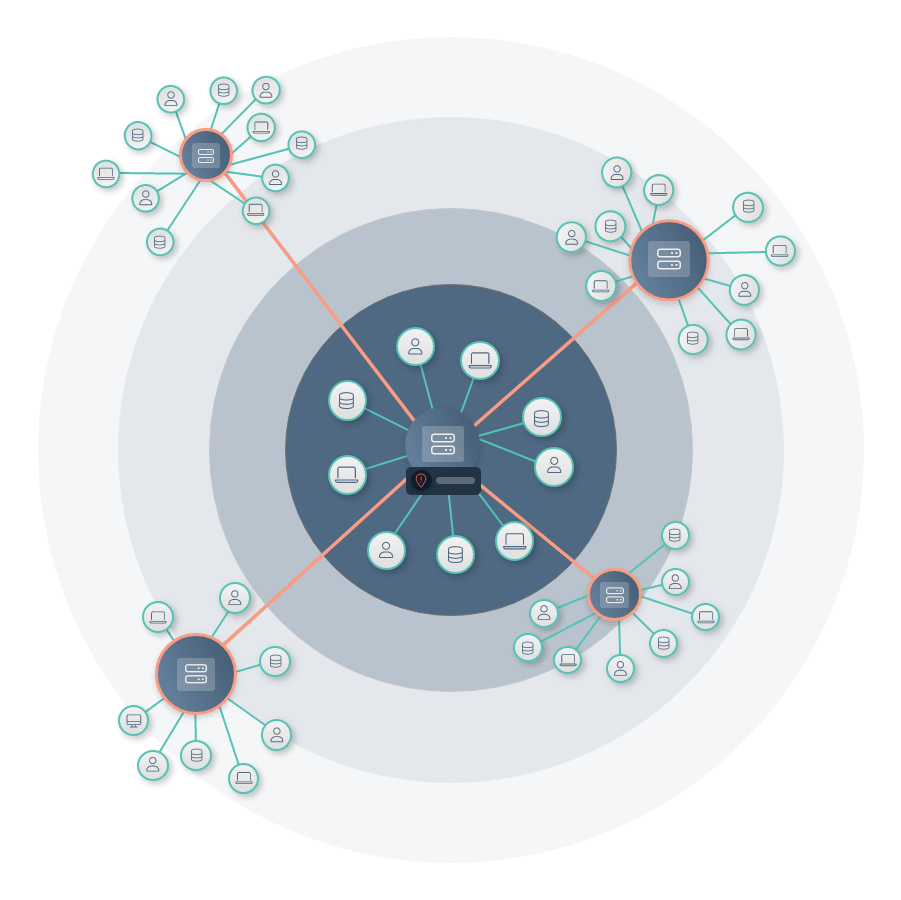
Focus on what matters most.
Of the millions of vulnerabilities that exist within a typical enterprise network, most teams only have the bandwidth to patch 10% of them per month. Prioritize the protection of your organization’s most valuable assets with Noetic.