Using Noetic for IT Operations
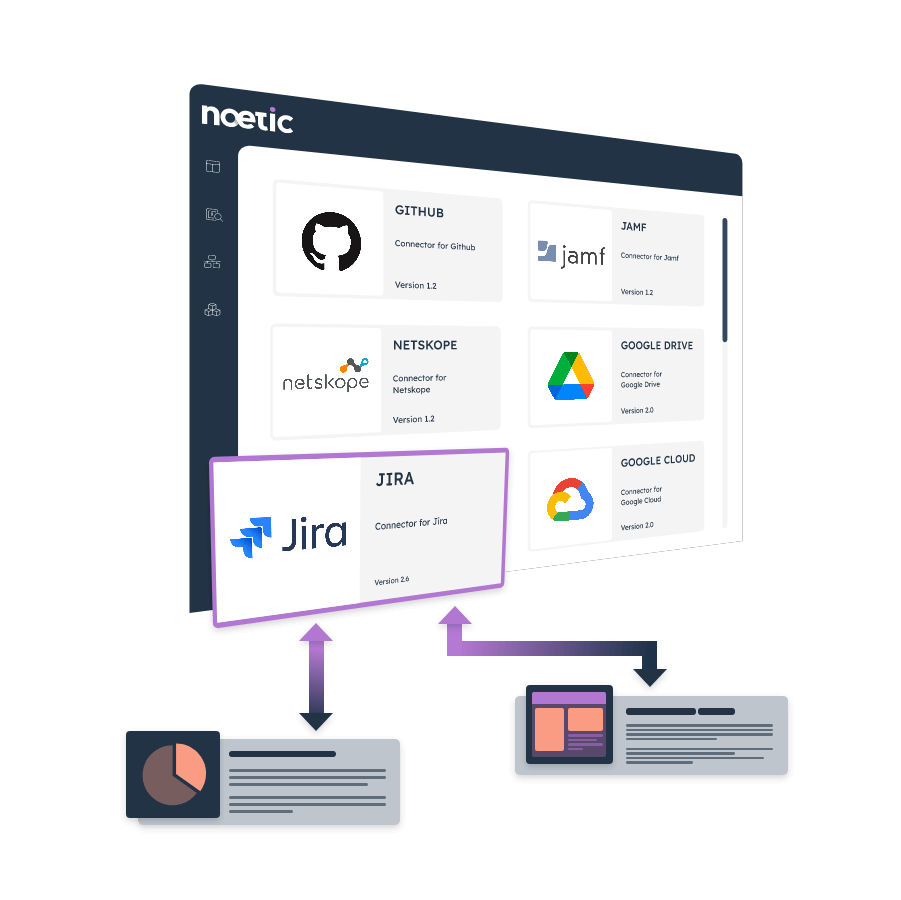
Looking to modernize IT Asset Management? Noetic can help.
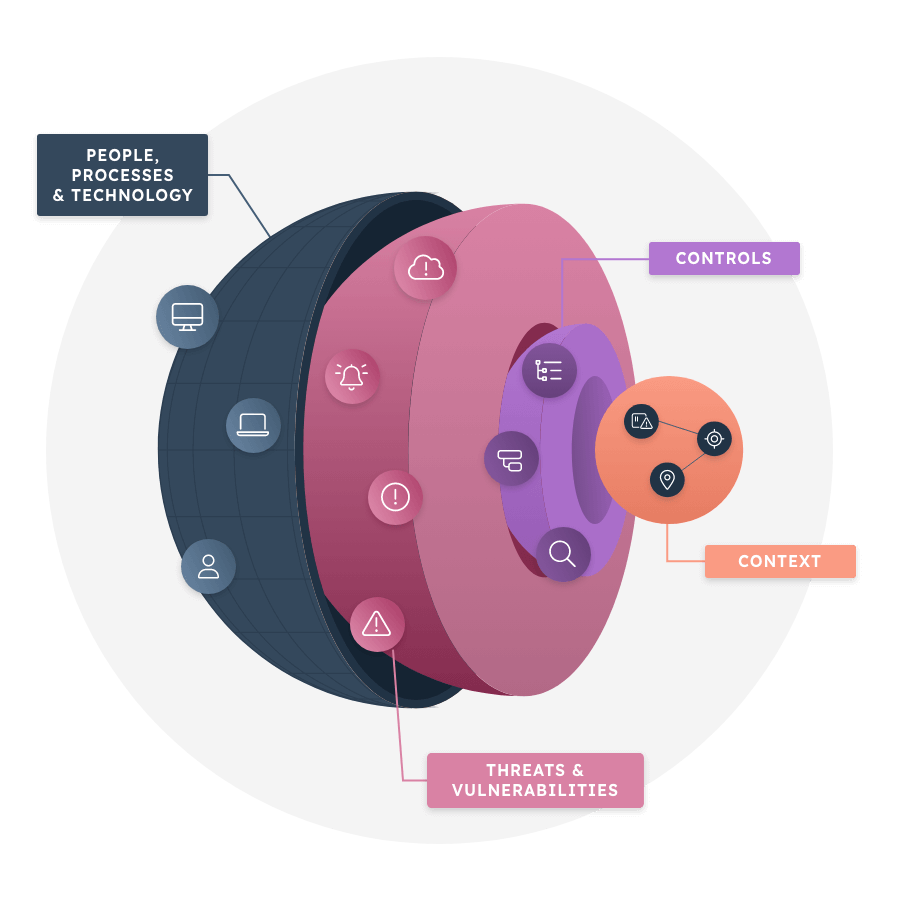
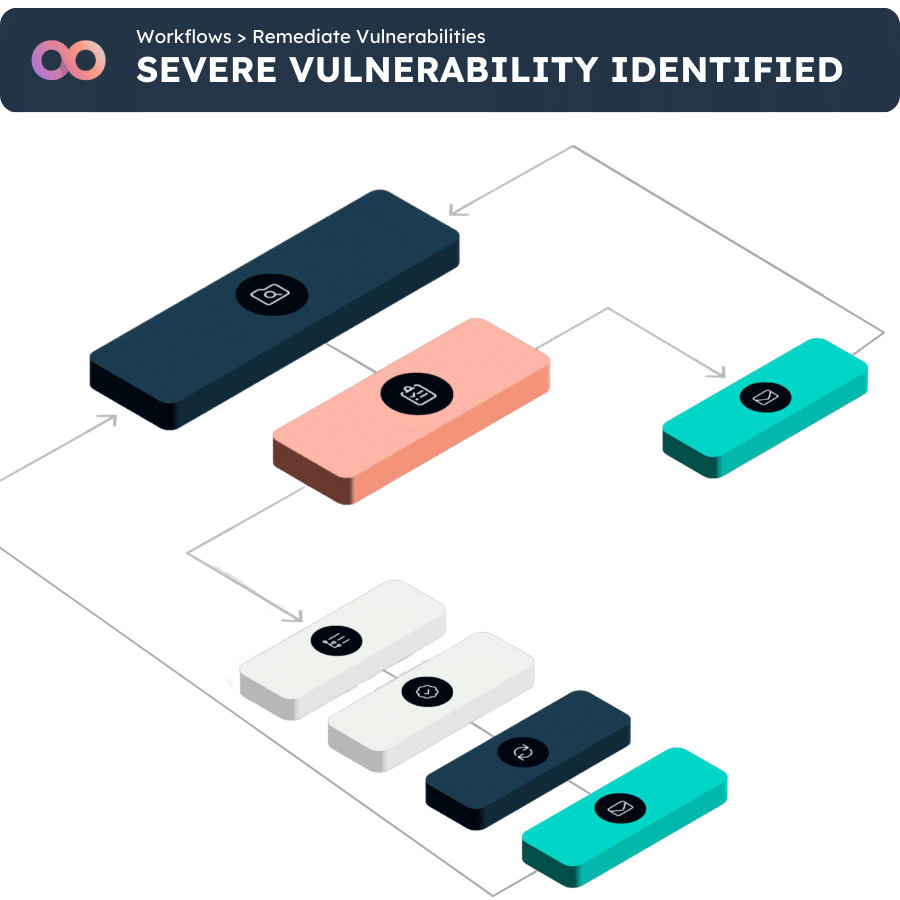
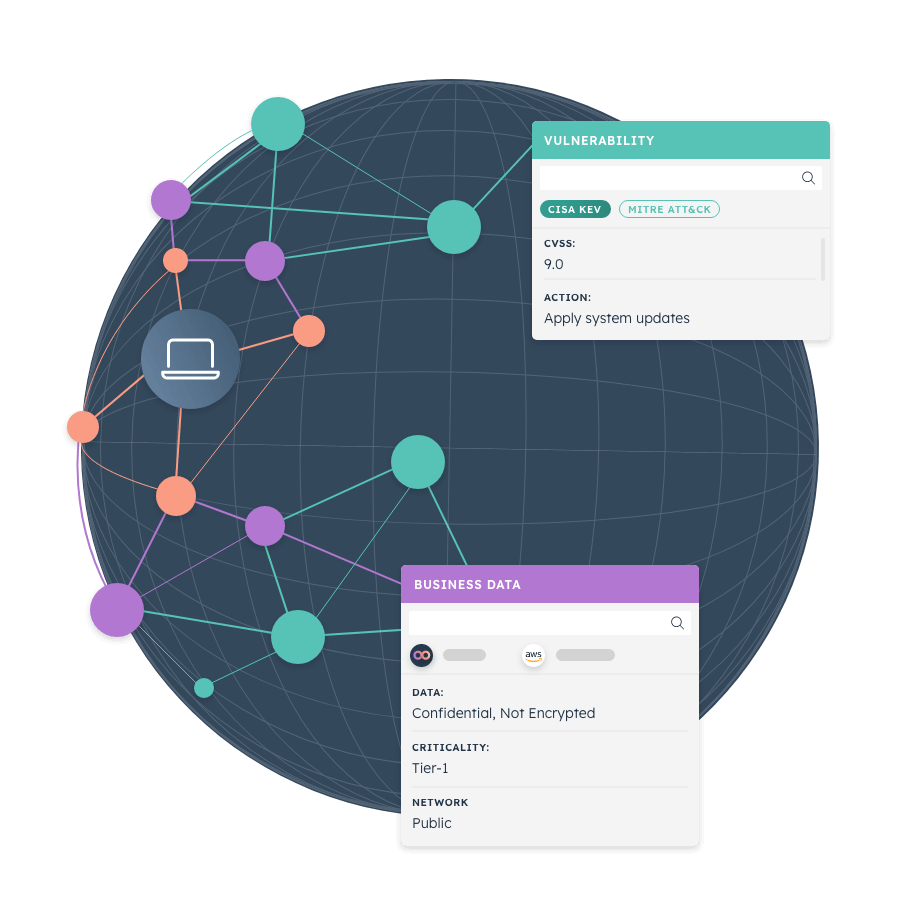
A modern approach to IT asset management needs to take full account of not just laptops and servers, but also new types of assets like containers, code snippets, virtual machines, users and vulnerabilities in the same way.