Unified Model Explorer: A Deep Dive into Cyber Assets & Relationships
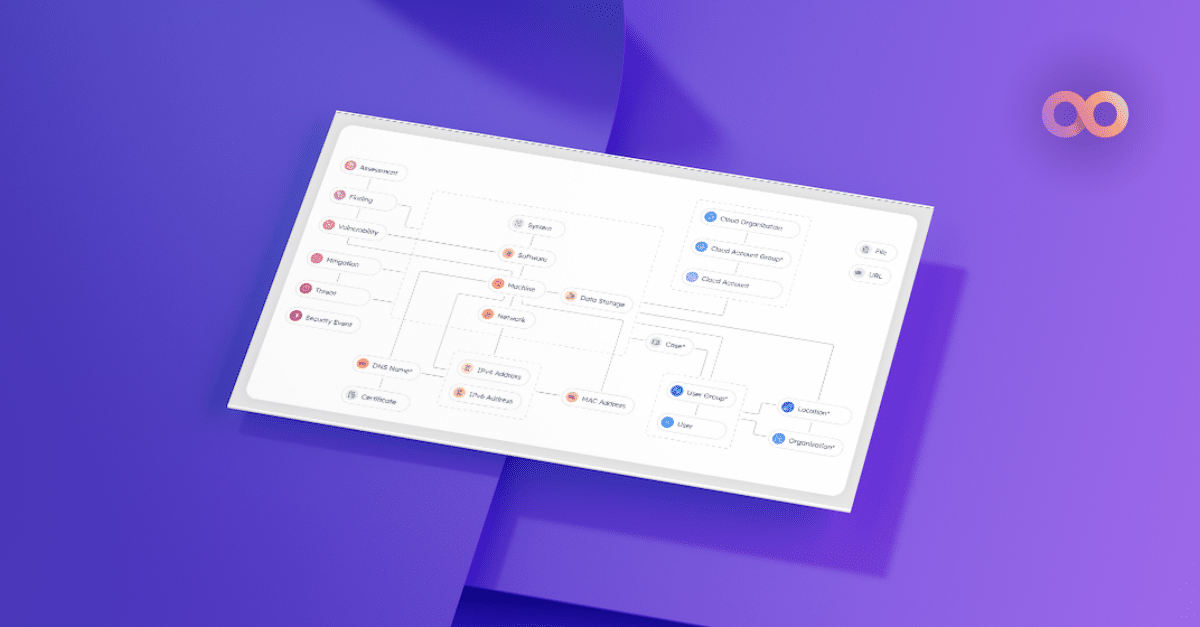
Last week, we introduced the new Noetic Unified Model Explorer. Now, we’re eager to guide you through its capabilities. Read on to gain a comprehensive understanding of its application and learn how it’s transforming the way security teams navigate and comprehend cyber asset relationships.
A key advantage of the Noetic Platform is its ability to leverage an extensible, innovative graph model to represent a broad collection of different cyber asset types (servers, workstations, users, networks, business applications, enterprise cloud accounts, etc.) and vulnerabilities, as well as the relationships between them. This helps our customers to better understand the full context of every exposure and security weakness across their cyber estate.
To explore the correlated data, and these cyber relationships, Noetic users have three options. First, they can use Data Insights, our new filterable, spreadsheet-like interface. Second, they can use our Query Builder to construct more advanced custom searches. And finally, users can write their own queries using Cypher, an open-source, industry standard Graph query language. This range of options supports different use cases, from simple coverage gaps, through to complex attack path mapping across multiple networks and locations.
However, to write an effective data query—in any language: SQL, Cypher, etc.—you need to understand the structure, or model, of the relevant security data. In this case, it would be the Noetic Unified Cyber Asset Model (or more simply, the Unified Model).
This is the purpose of the new Unified Model Explorer, which is a graphical, interactive tool that helps users to quickly understand different asset types and the relationships between them. By clicking on an asset type in the graph, it highlights the relevant direct relationships and provides a complete list of ‘unified properties’ for that type.
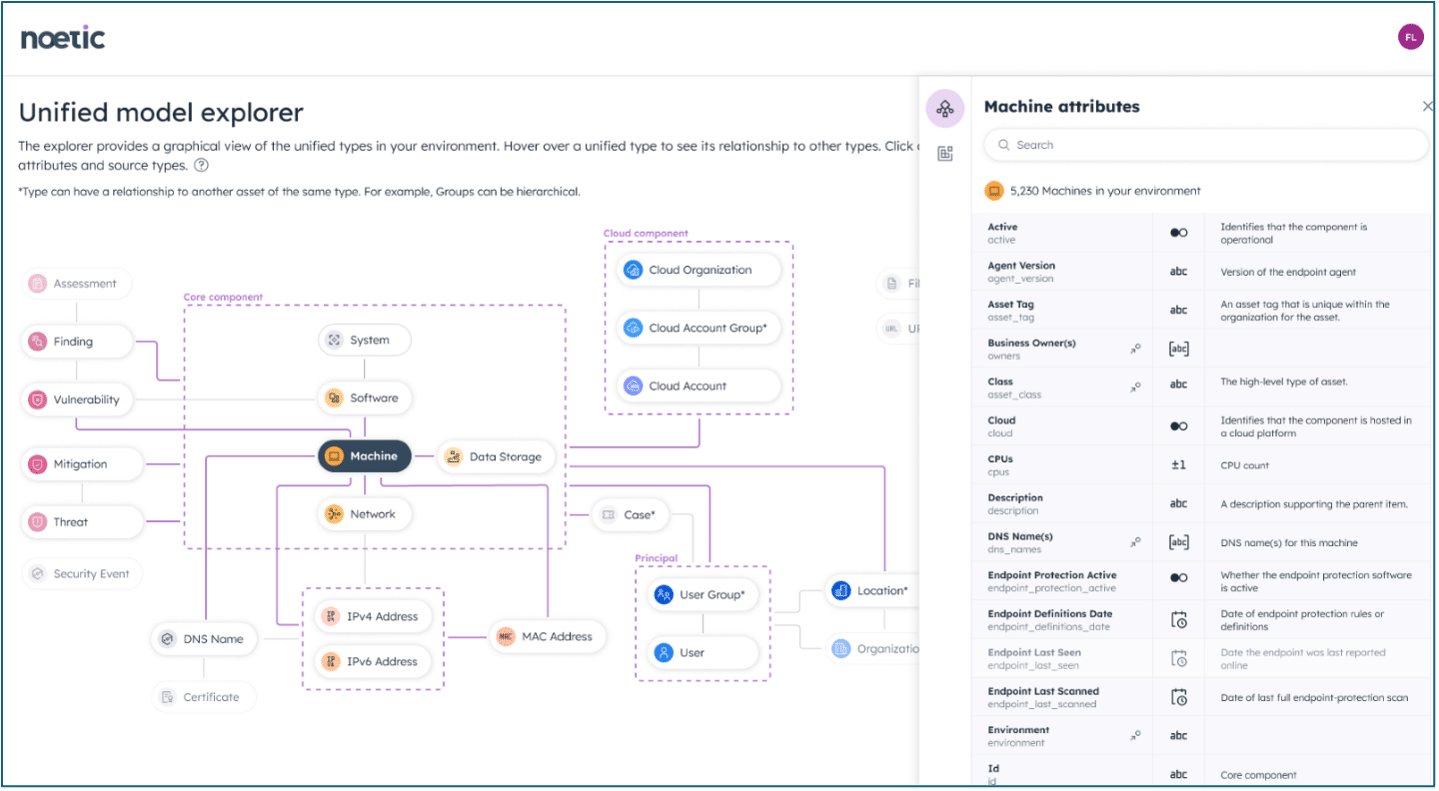
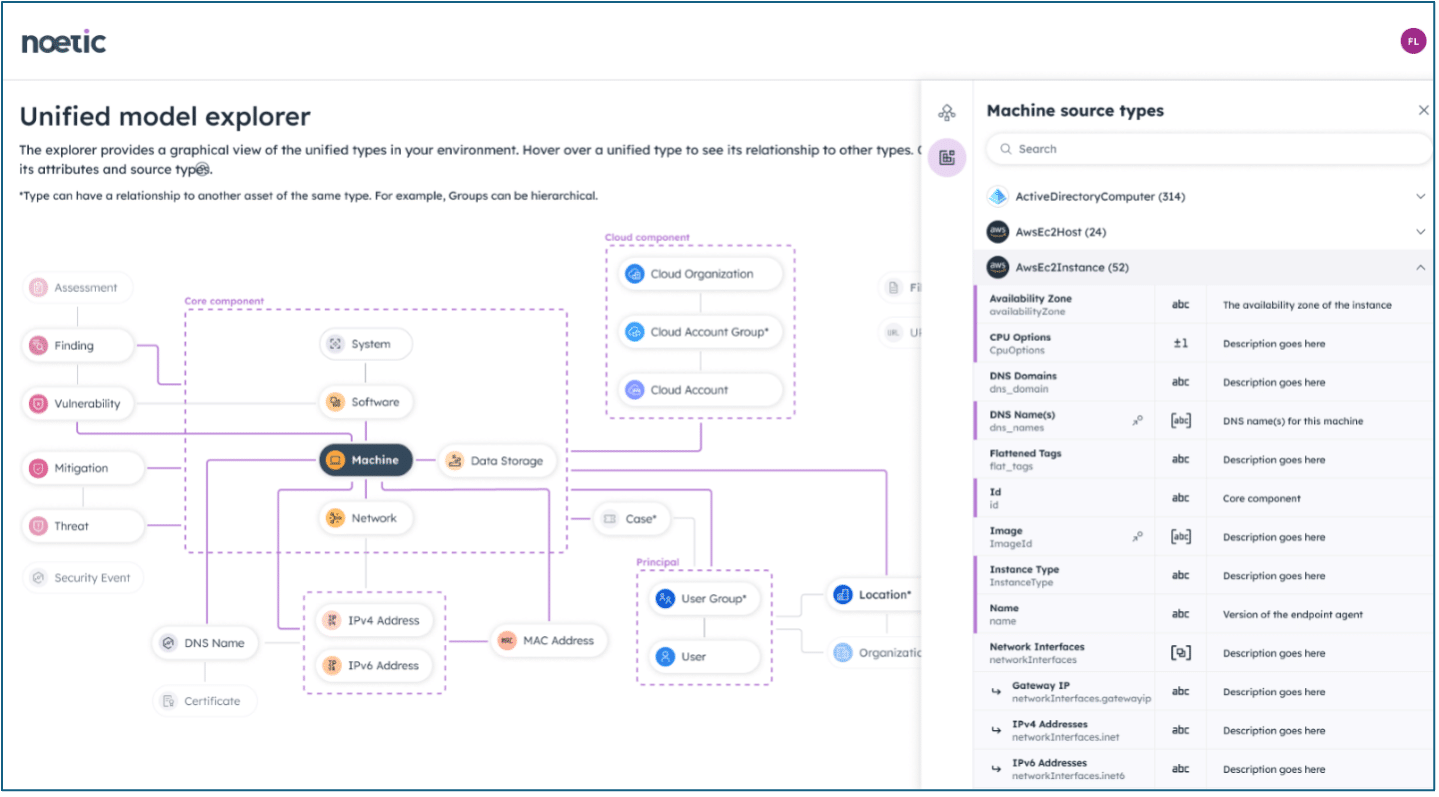
Another important feature is the way that Noetic ingests asset data from external tools. Unlike some other CAASM solutions, Noetic retains the full history of all of the source data as it aggregates and correlates multiple sources as part of the unification process..
This means that users can query very tool-specific data from a diverse range of systems such as AWS EC2, SentinelOne Singularity, or Tenable Vulnerability Management. To help facilitate this, Unified Model Explorer also provides detailed information about each of the source data types a customer has configured for their environment.
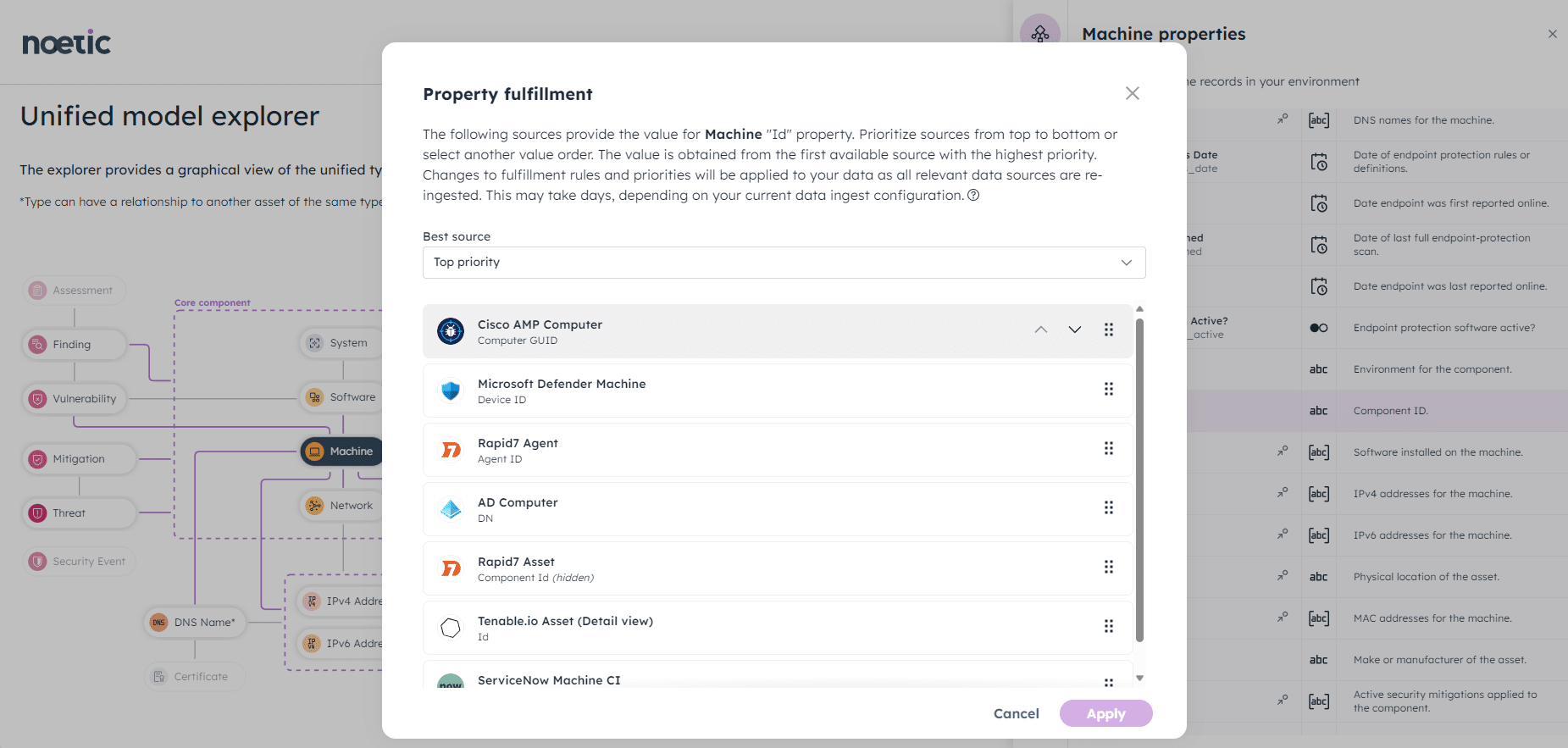
However, the Model Explorer is not just intended to be a reference source to simplify the process of writing queries in the Noetic platform, it is also designed to improve the fidelity and accuracy of the platform by enabling users to easily tune how the Unified Model is populated from the different data sources being ingested.
For example, an organization’s Configuration Management Database (CMDB), such as ServiceNow, might be an excellent source of information for some properties of a ‘machine’ (e.g. servers & workstations)–such as the business applications it supports, but provides poor or outdated data on others. Users with the appropriate level of privilege could then use the Unified Model Explorer to prioritize or de-prioritize the CMDB as a source for these properties.
The initial release of Noetic’s Unified Model Explorer is rolling out to customers over the coming week. If you are keen to understand more about its capabilities, please reach out to your customer success manager.
If you’re not currently a Noetic customer but would like to better understand our approach to cyber asset management, and how our unique data model gives our customers deep insights into their security hygiene and posture management, check out this demo of the Unified Model Explorer below
