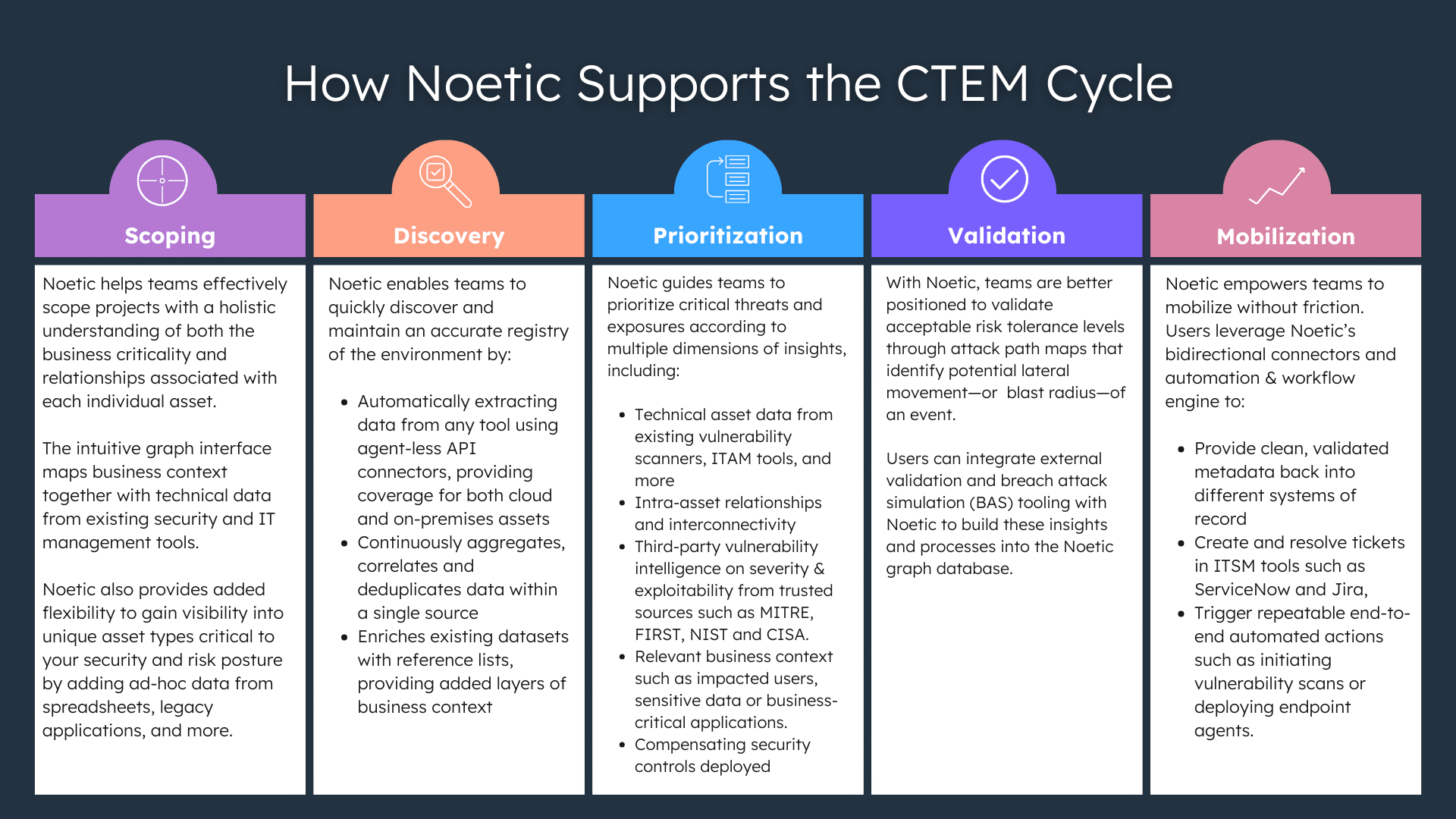
A Guide to Continuous Threat Exposure Management (CTEM)
In an era where traditional vulnerability management programs fall short in addressing the persistent and sophisticated nature of cyber threats, Continuous Threat Exposure Management (CTEM) emerges as a comprehensive solution. This guide is your roadmap to understanding and implementing CTEM. From establishing a foundational framework to uncovering the myriad advantages of adoption, we’ll explore the intricate steps and tools to embrace a modern exposure management framework.