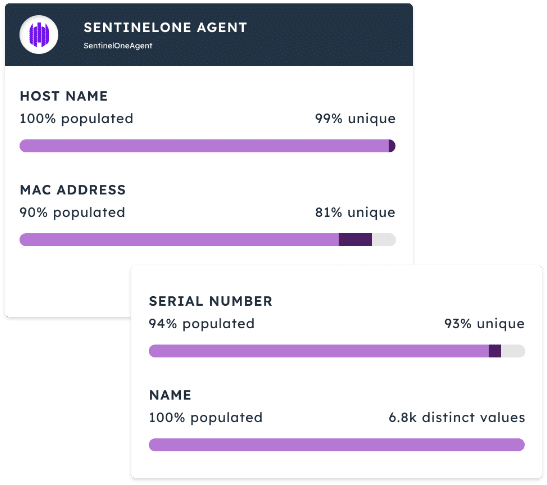
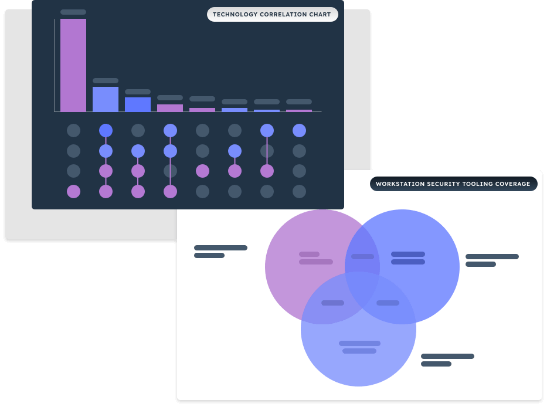
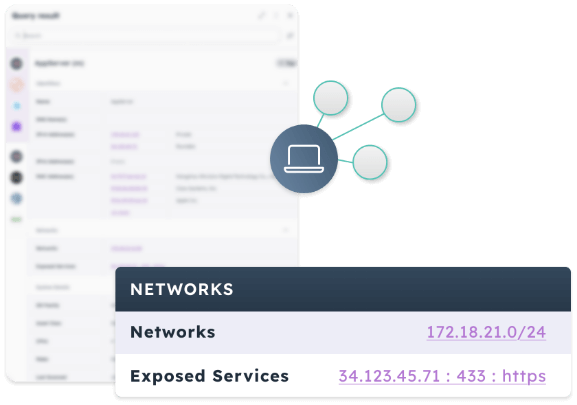
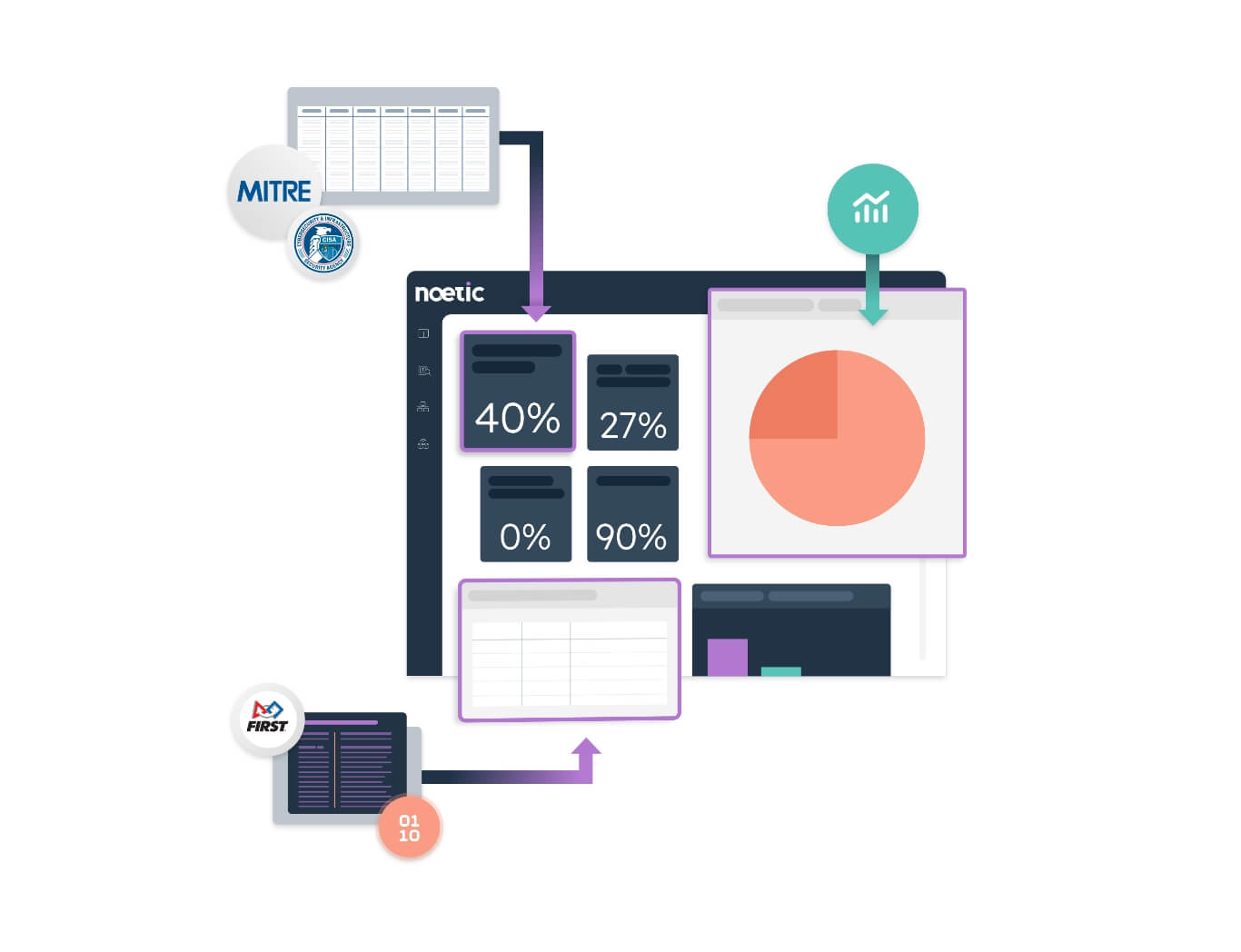
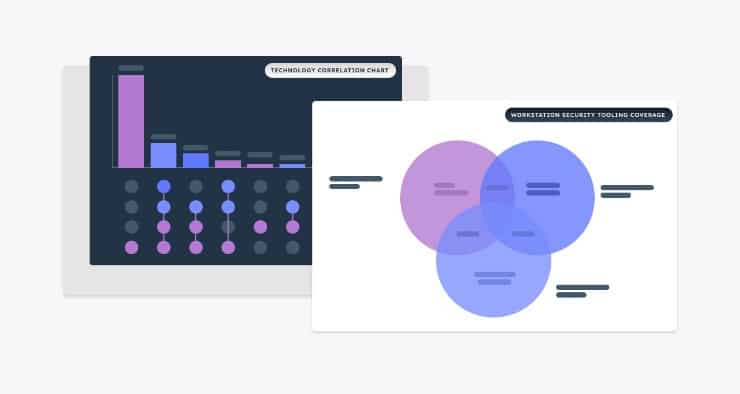
The Noetic Cyber Asset and Exposure Management platform is a cloud native solution that enables security teams to gain control of their attack surface and reduce their cyber risk. By integrating with existing security, networking and IT management tools, the Noetic platform builds a 360-degree view of the entire cyber estate, mapping all assets, their security posture and the relationship to all other assets in the environment.
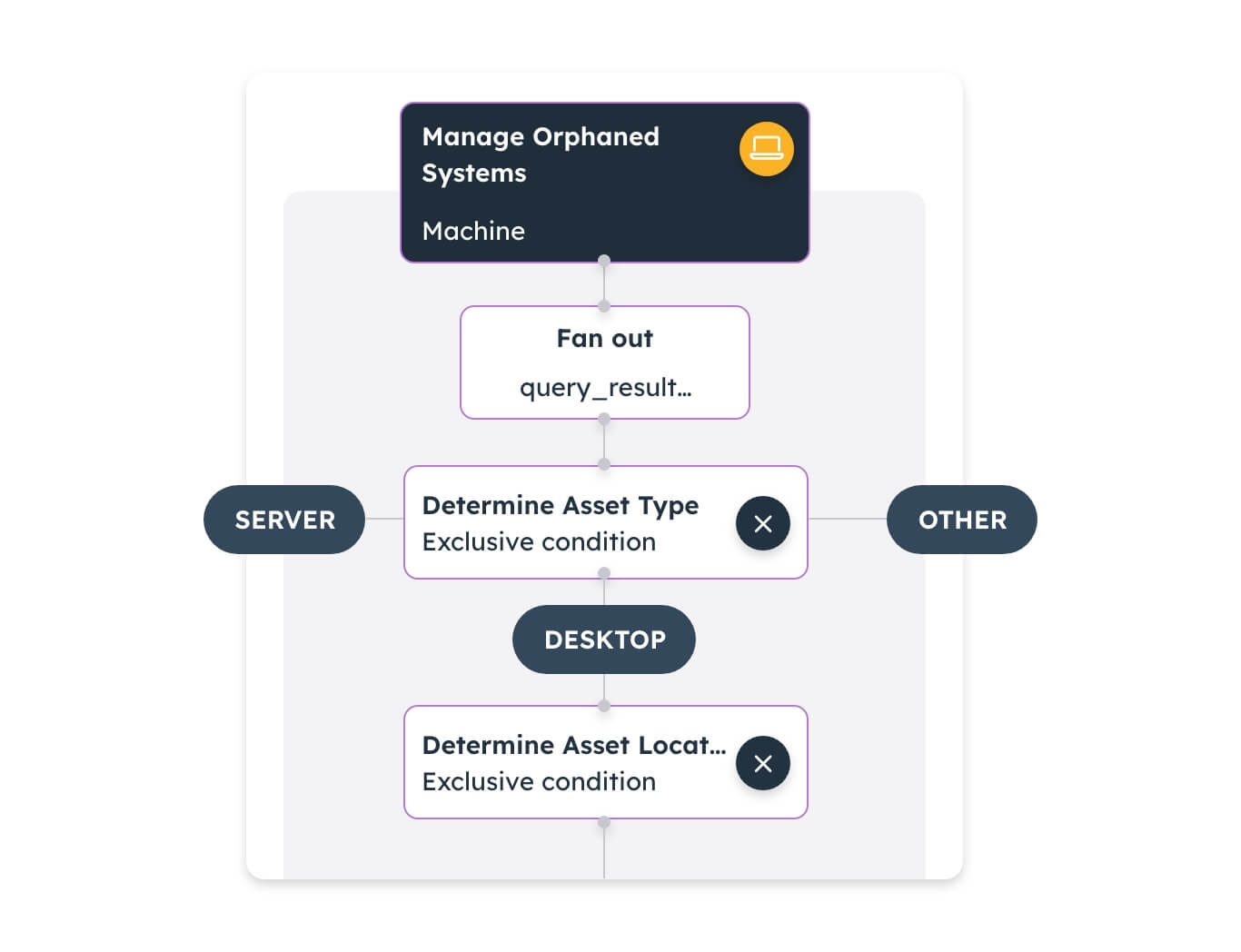
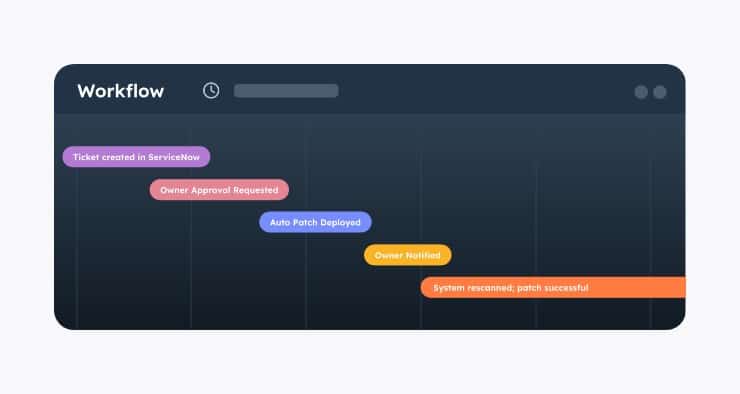
Built to drive prioritization and action, the Noetic platform provides customizable dashboards and reporting, and a fully integrated automation and workflow engine to drive remediation of coverage gaps and unmanaged exposures.