Noetic for Cyber Insurance Applications and Renewals
Understand insurability.
Influence coverage.
Better negotiate premiums.
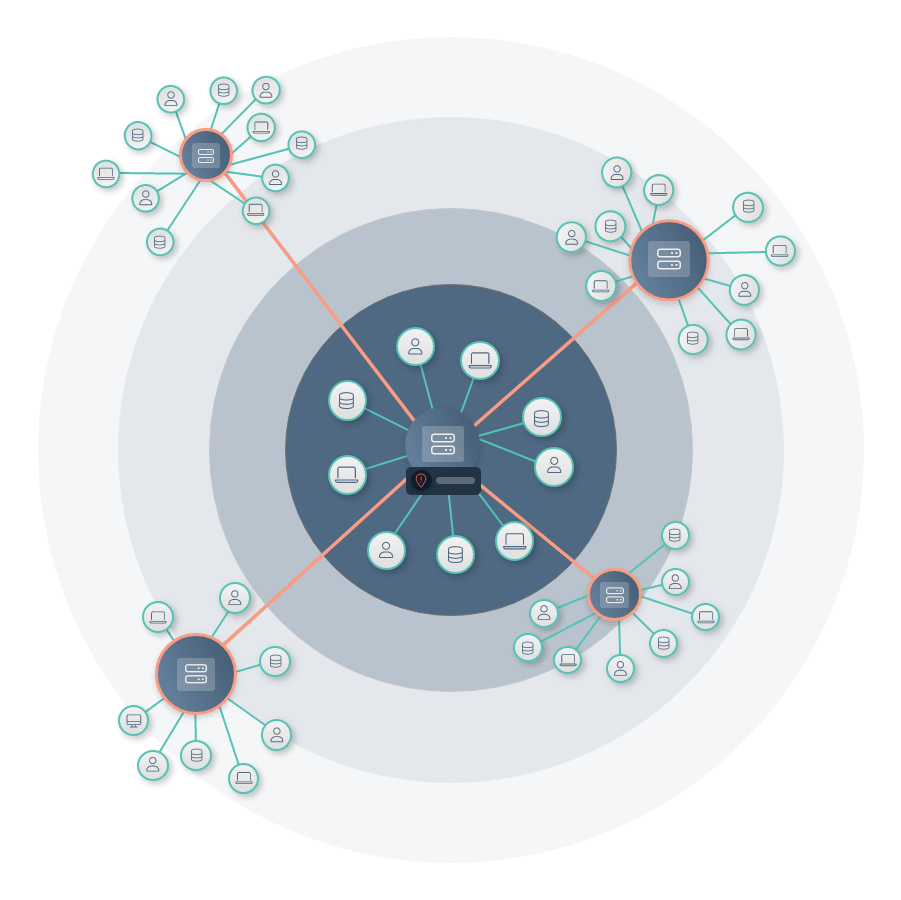
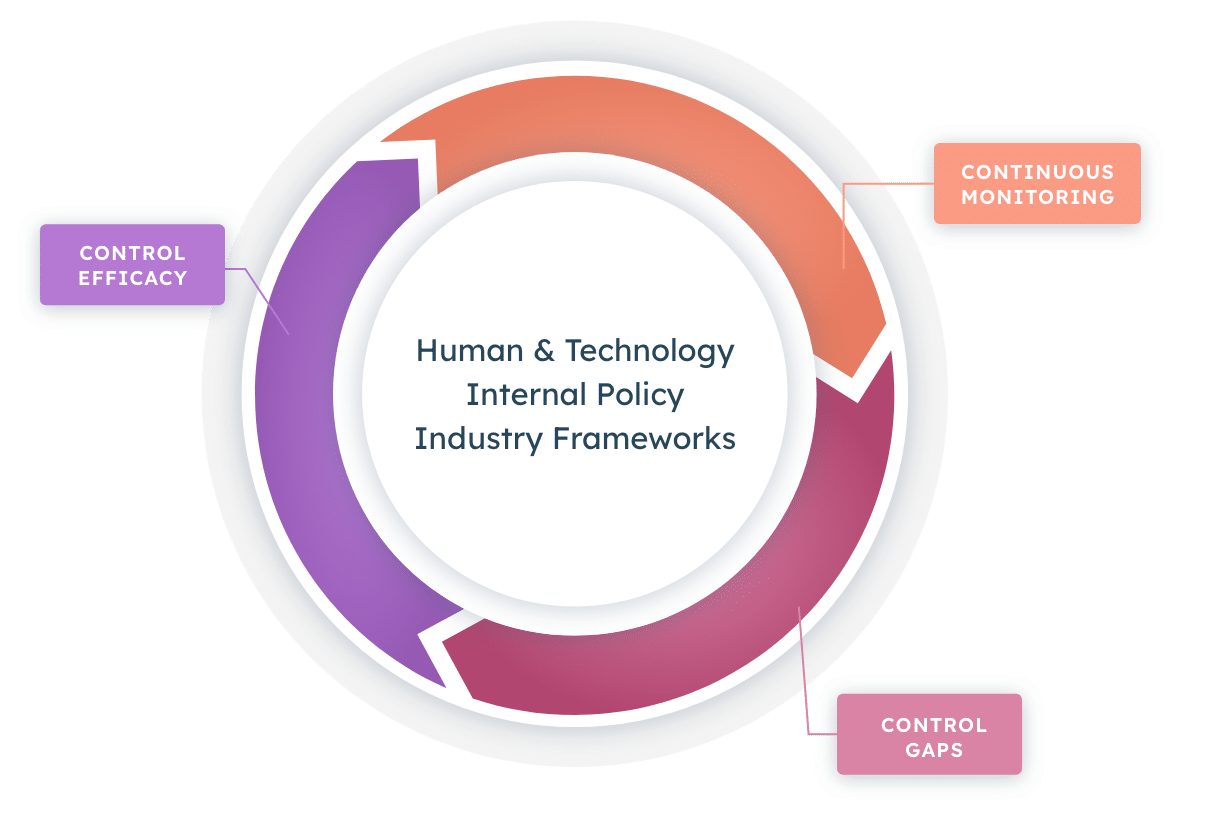
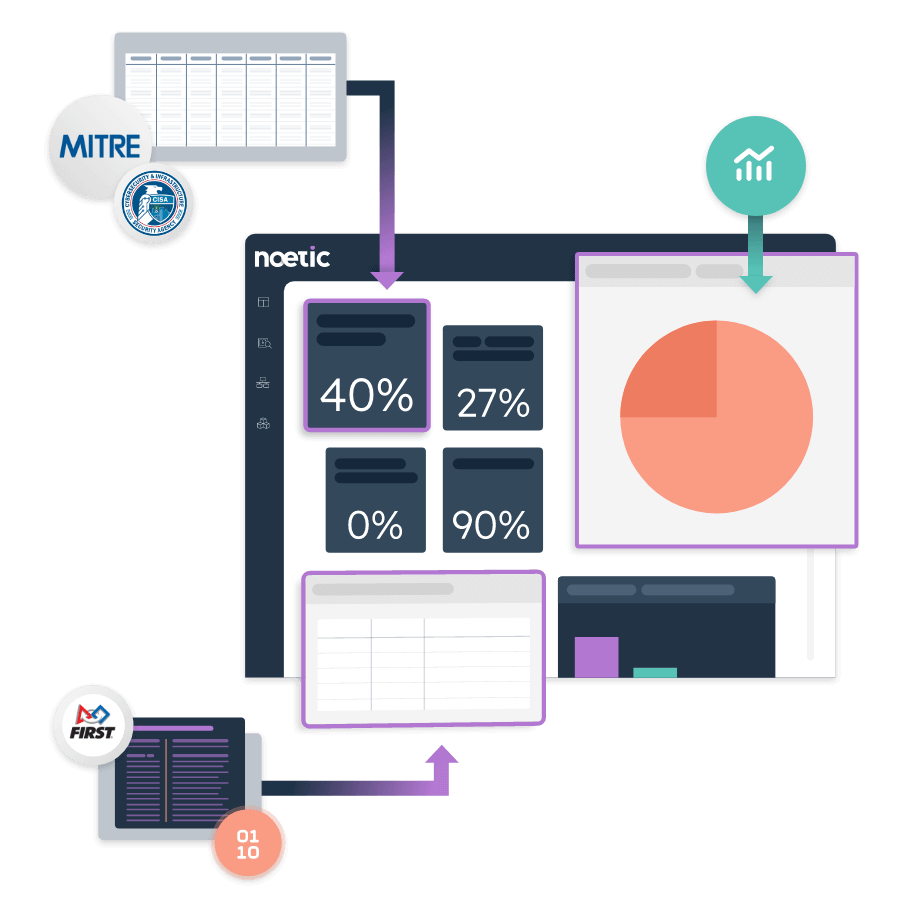
Cyber incidents are the #1 business threat globally, and the demand for cyber liability coverage has never been higher. As such, cyber insurance providers are doubling down on the basic security qualifications for applications and renewals.