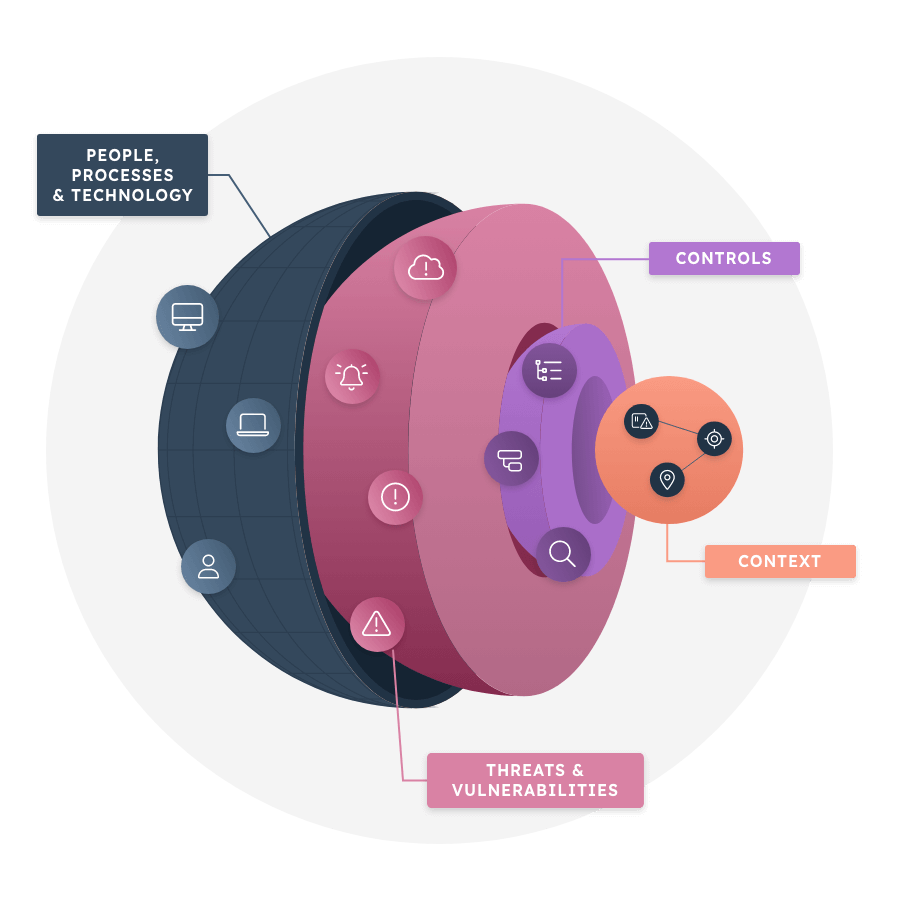
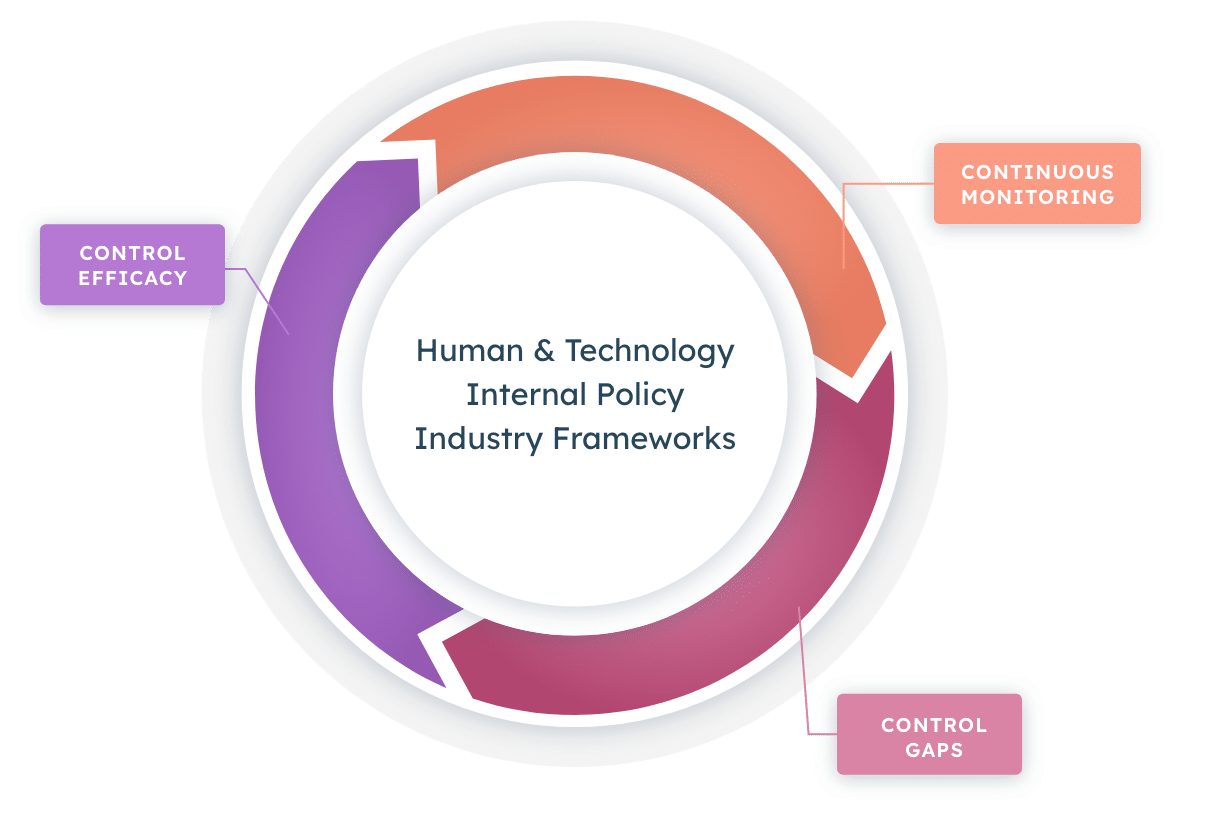
Noetic for Mergers and Acquisitions
Despite the biggest threat in cybersecurity being the unknown, less than 10% of organizations audit potential partners during the M&A due diligence process.
Whether you’ve recently acquired a company, or planning to make a future investment, Noetic can help.