Cyber Asset Attack Surface Management for Security Operations
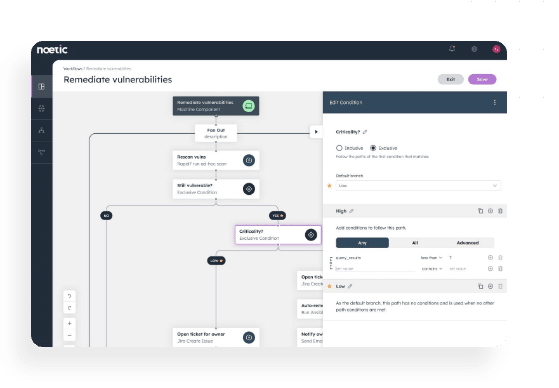
Accelerate incident response.
Prevent future threats.
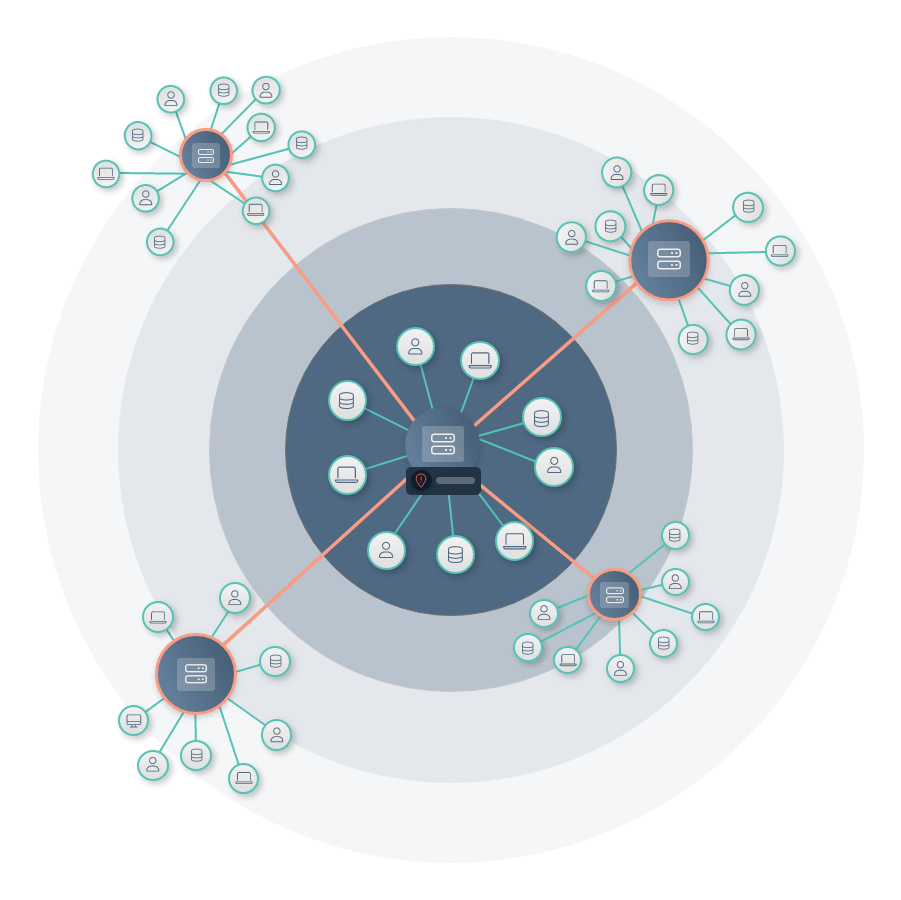
Security operations teams are under more pressure than ever. They need to make fast, accurate decisions based on complete information.
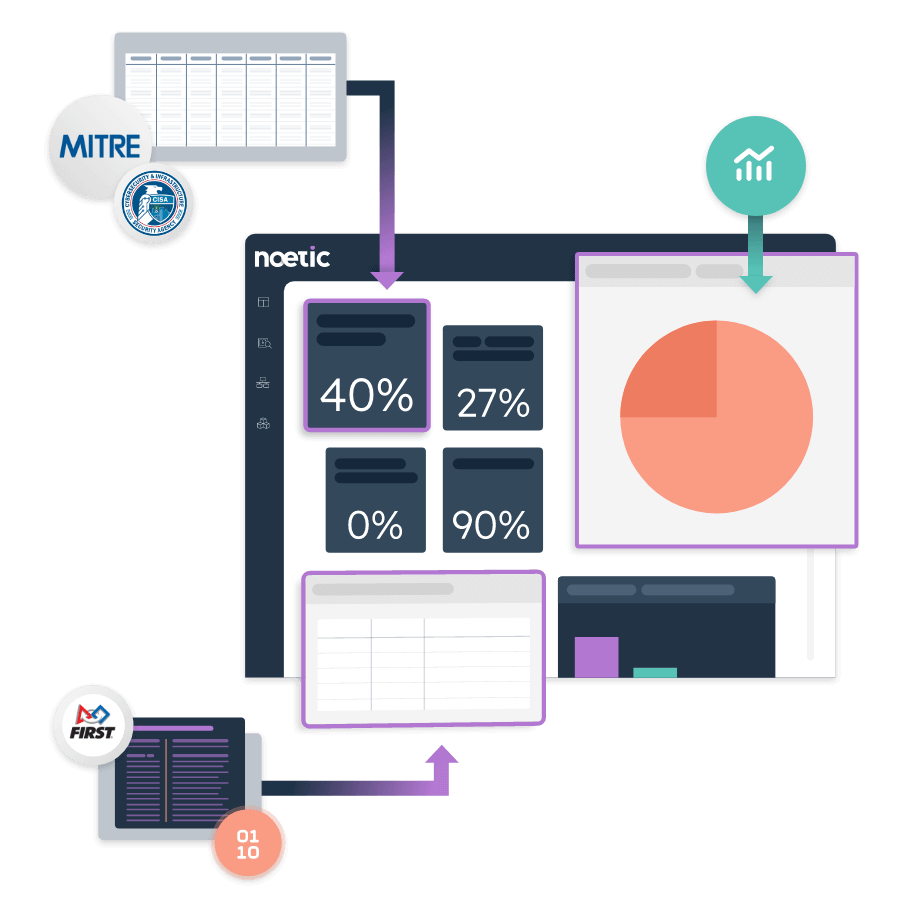
Enter: A comprehensive cyber asset attack surface management solution by Noetic.