Noetic Cyber Asset Attack Surface Management
You can’t protect what you can’t see. Discover the power of visibility with Noetic.
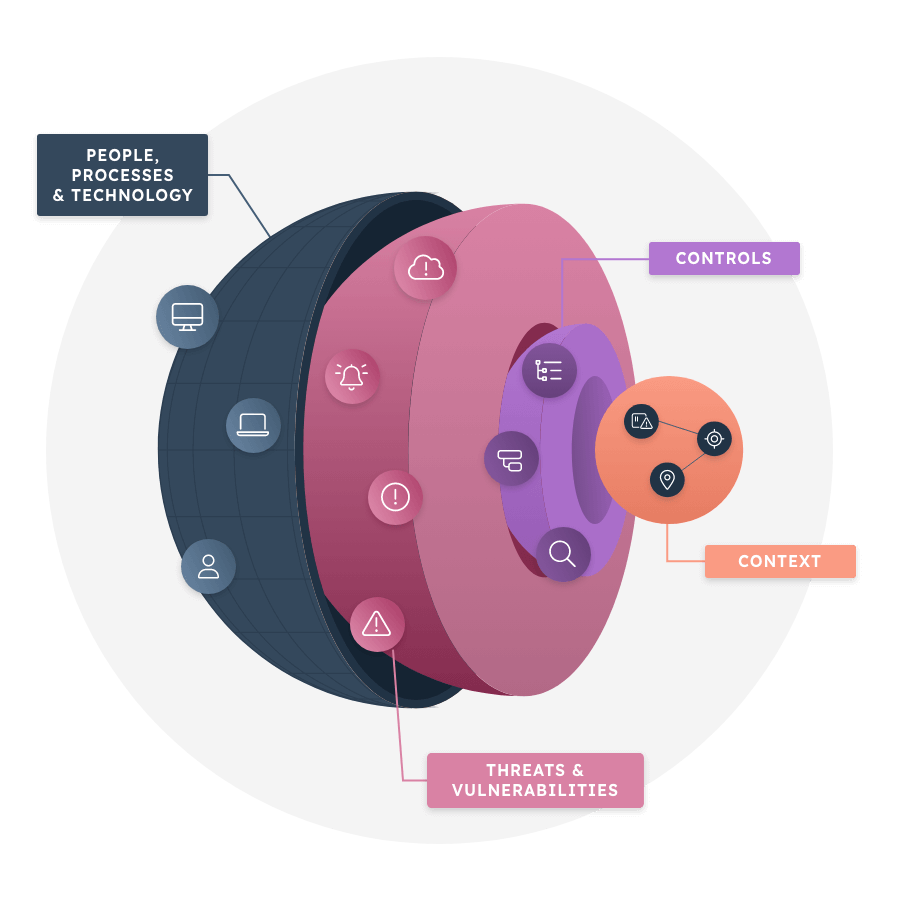
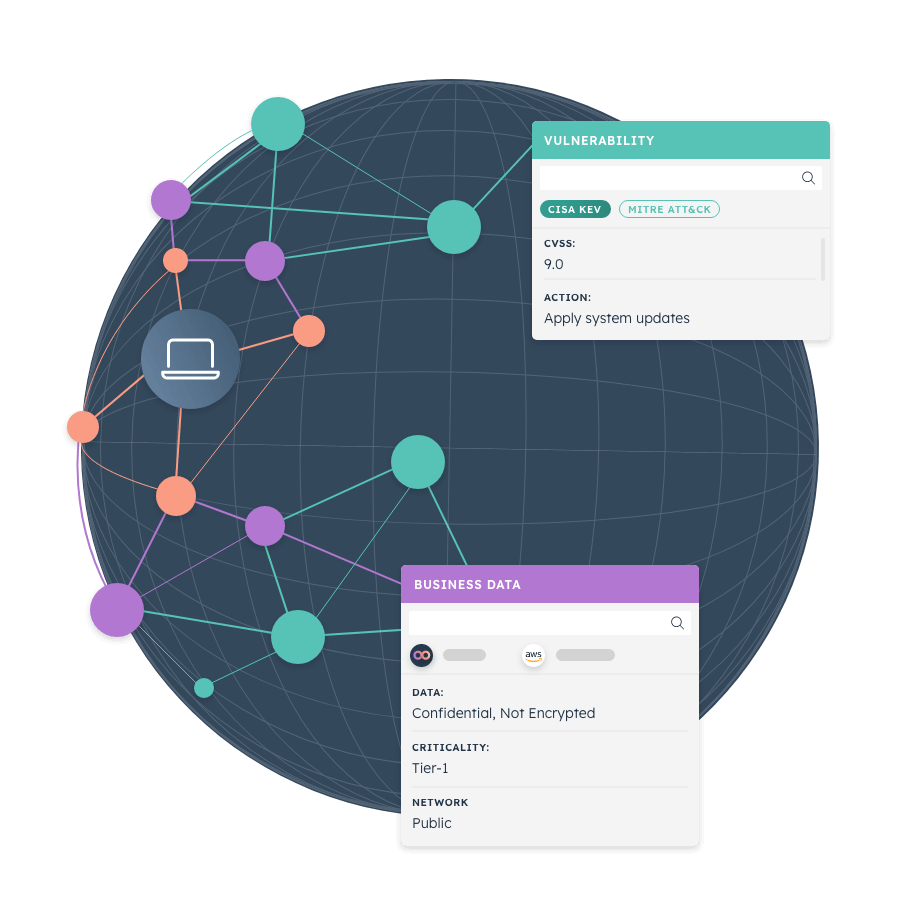
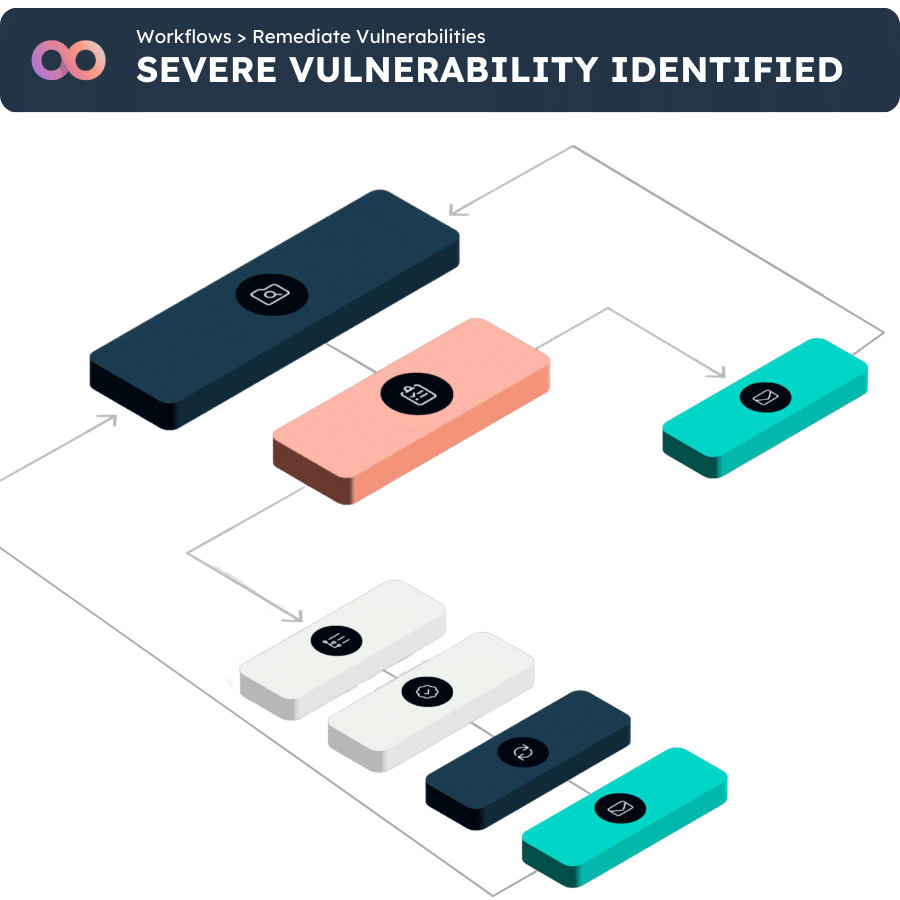
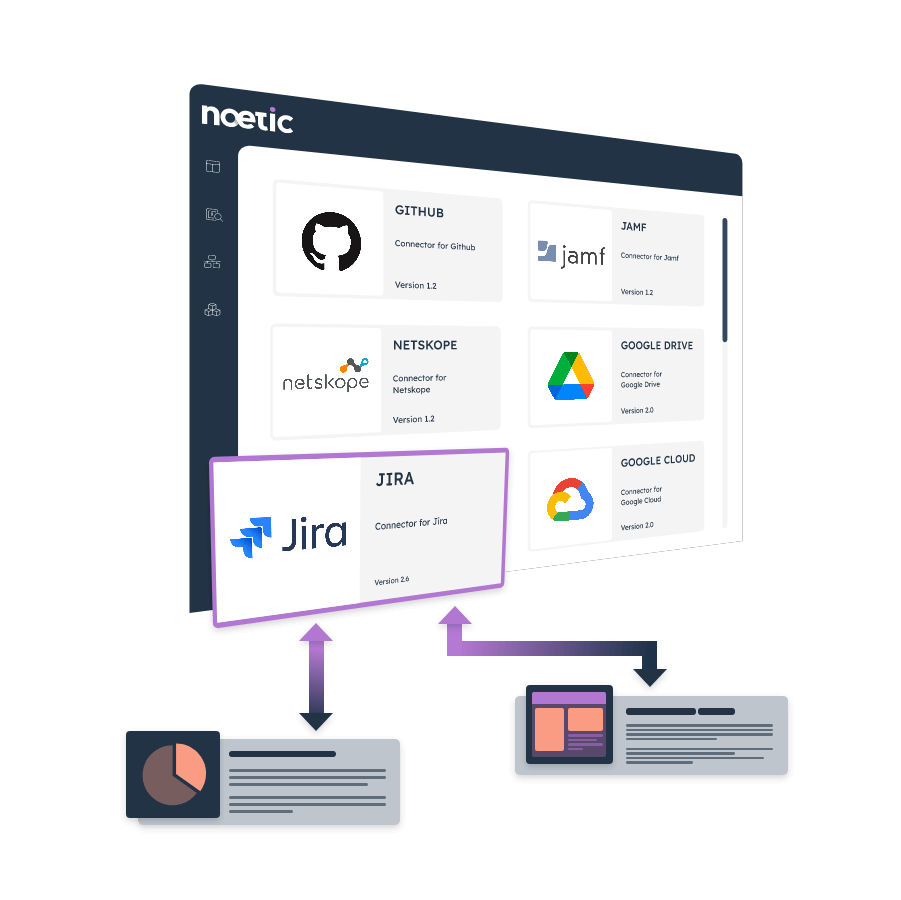
Creating and maintaining a comprehensive an up-to-date cyber asset inventory is a cornerstone for any cybersecurity team. However, doing this is anything but simple. That’s where our leading Cyber Asset Attack Surface Management (CAASM) platform comes in.