Noetic for Critical Infrastructure Cybersecurity
Understand your attack surface better than the adversary.
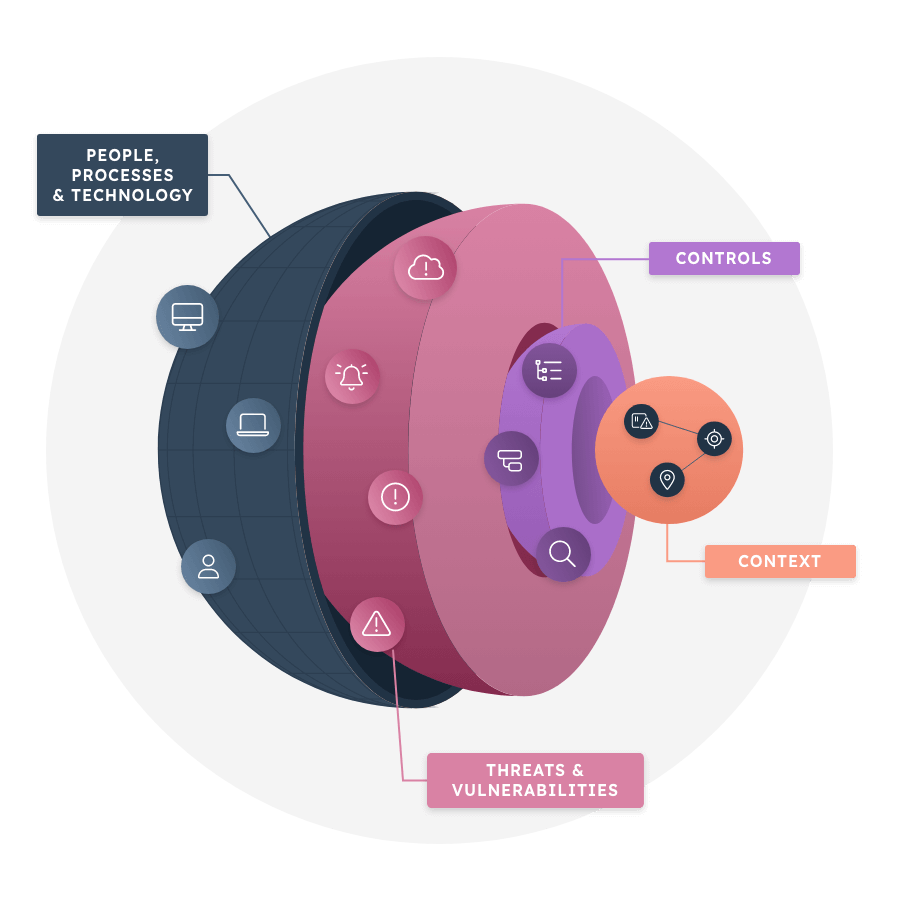
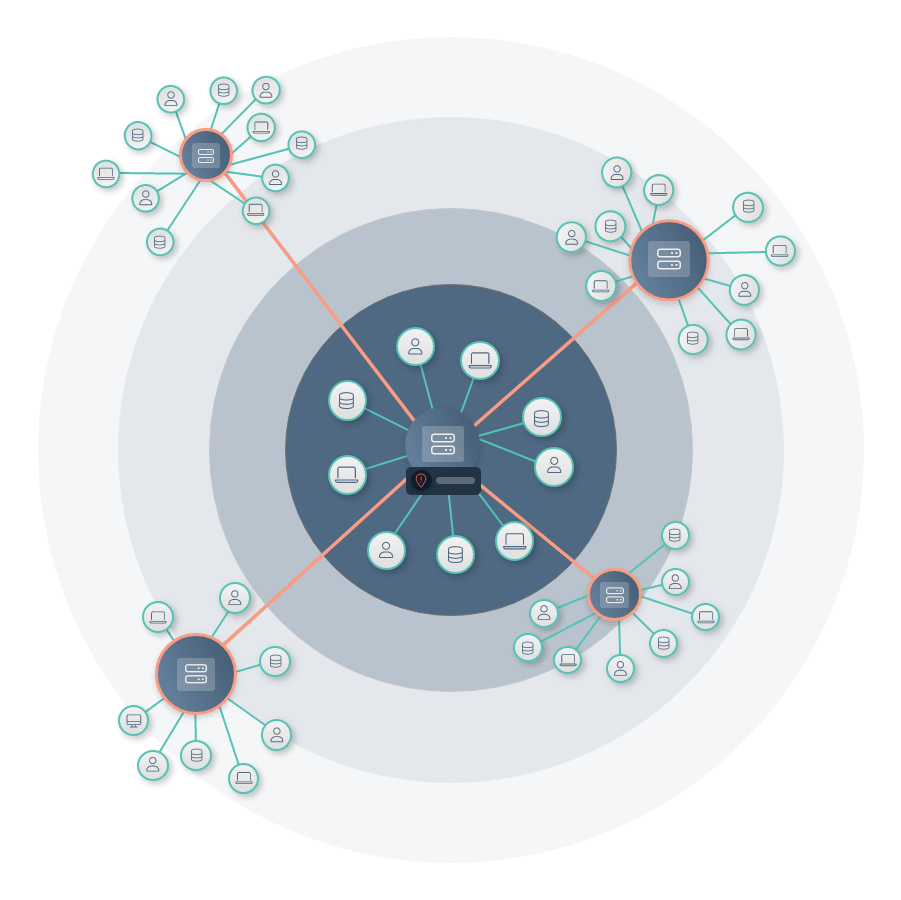
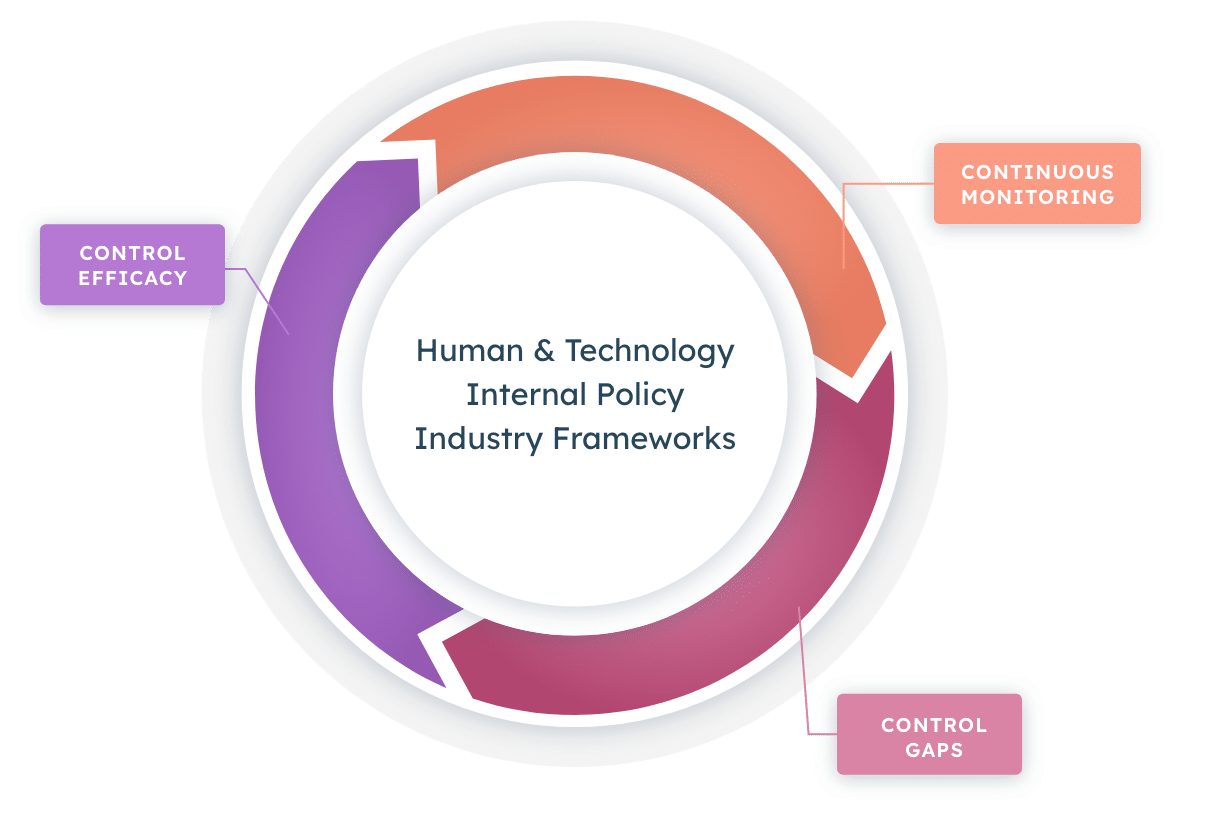
To keep global business operating as usual, security and risk teams in charge of protecting critical infrastructure must understand exactly what they’re defending. That’s where Noetic comes in.