Cyber Asset Management
Solutions for CISOs
Reduce today‘s risk.
Fuel tomorrow’s growth.
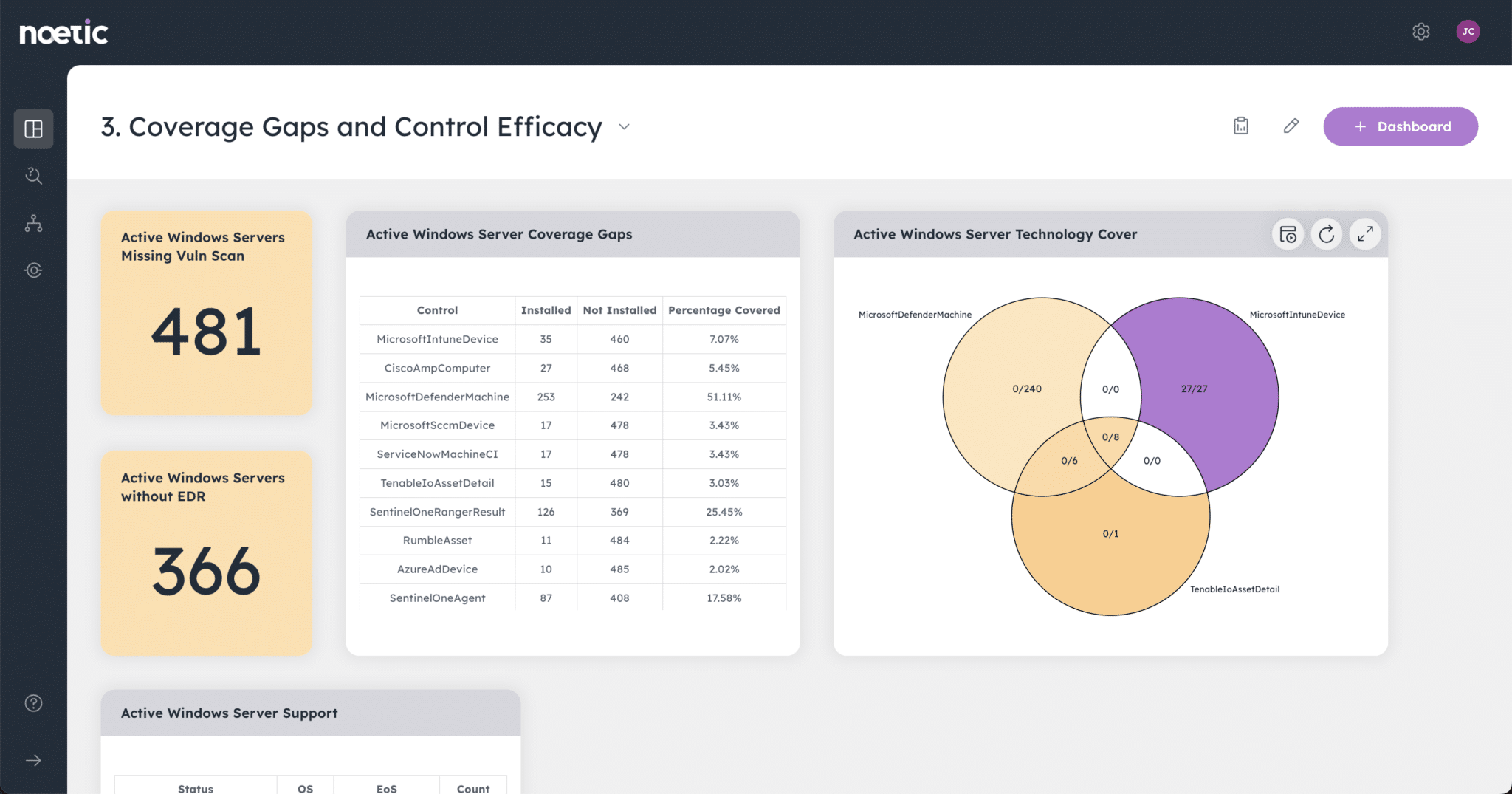
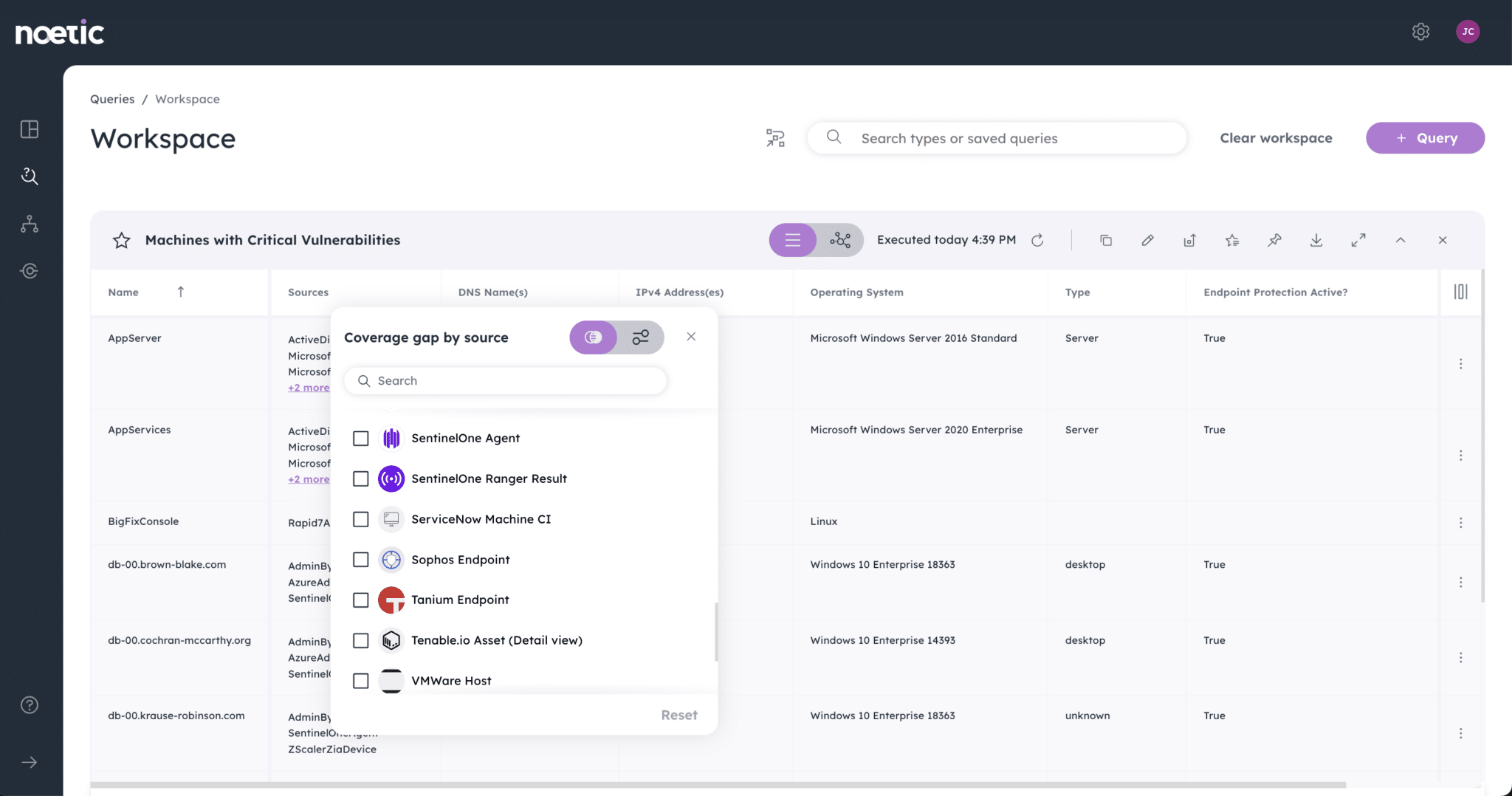
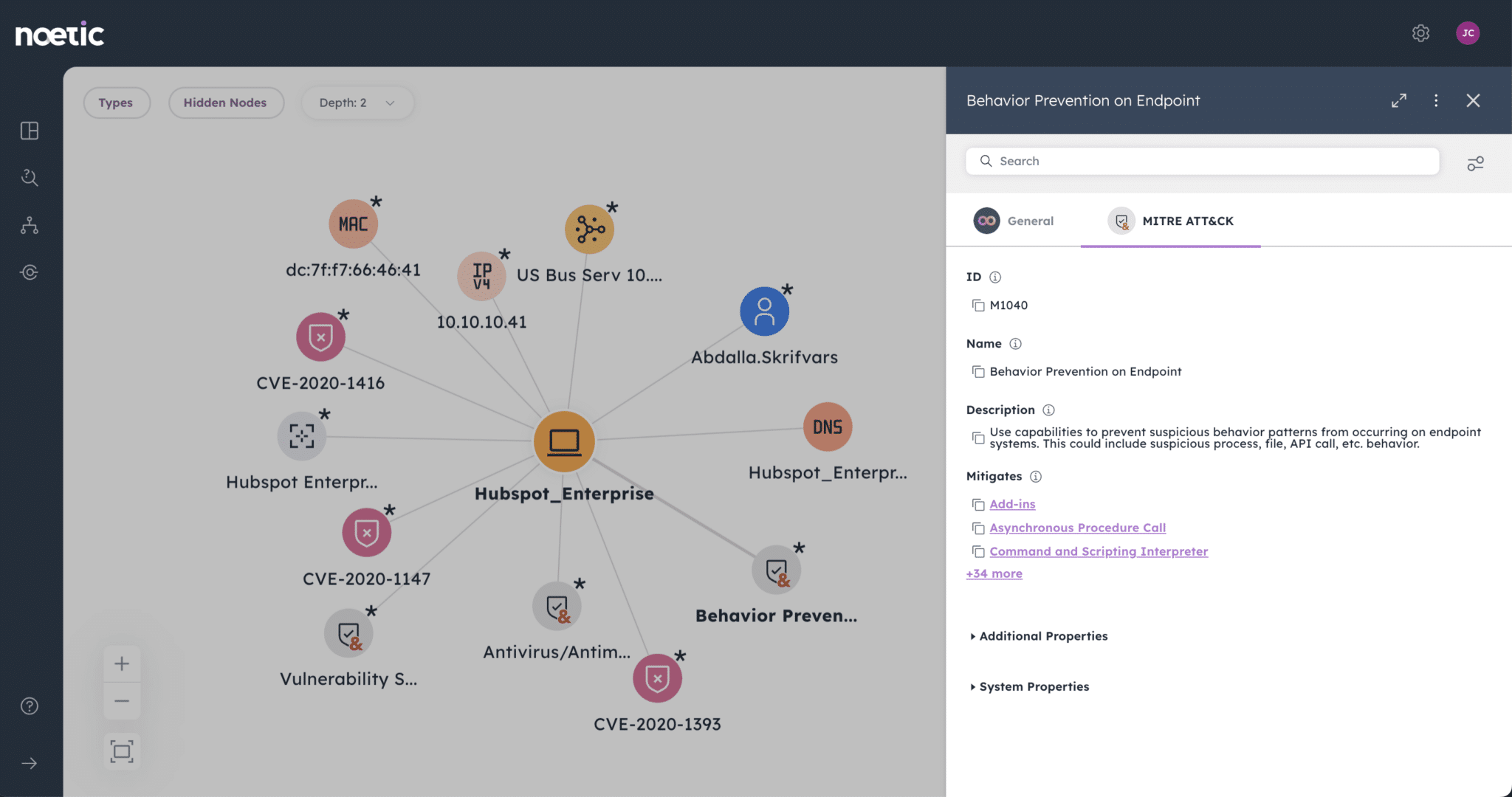
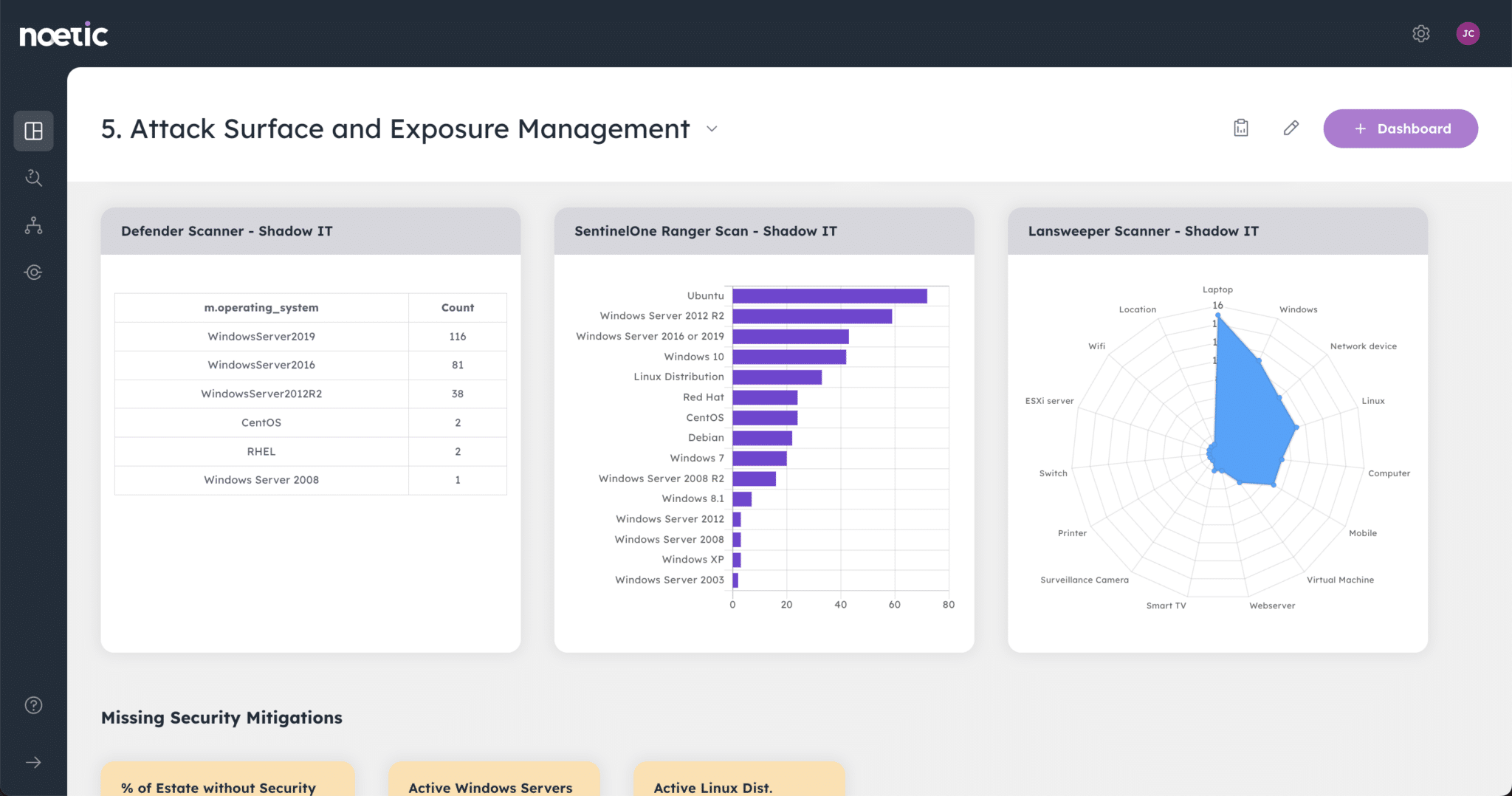
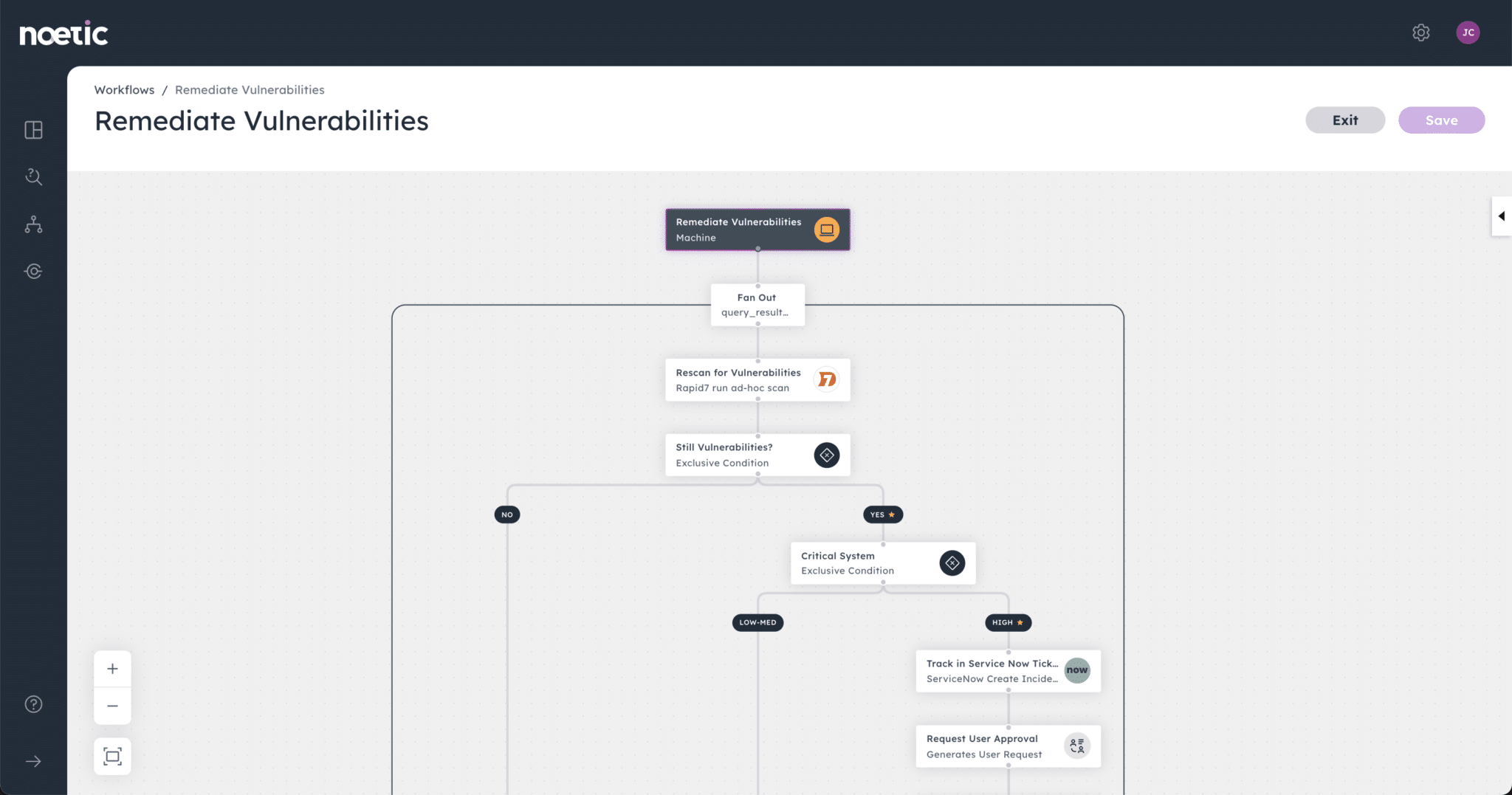
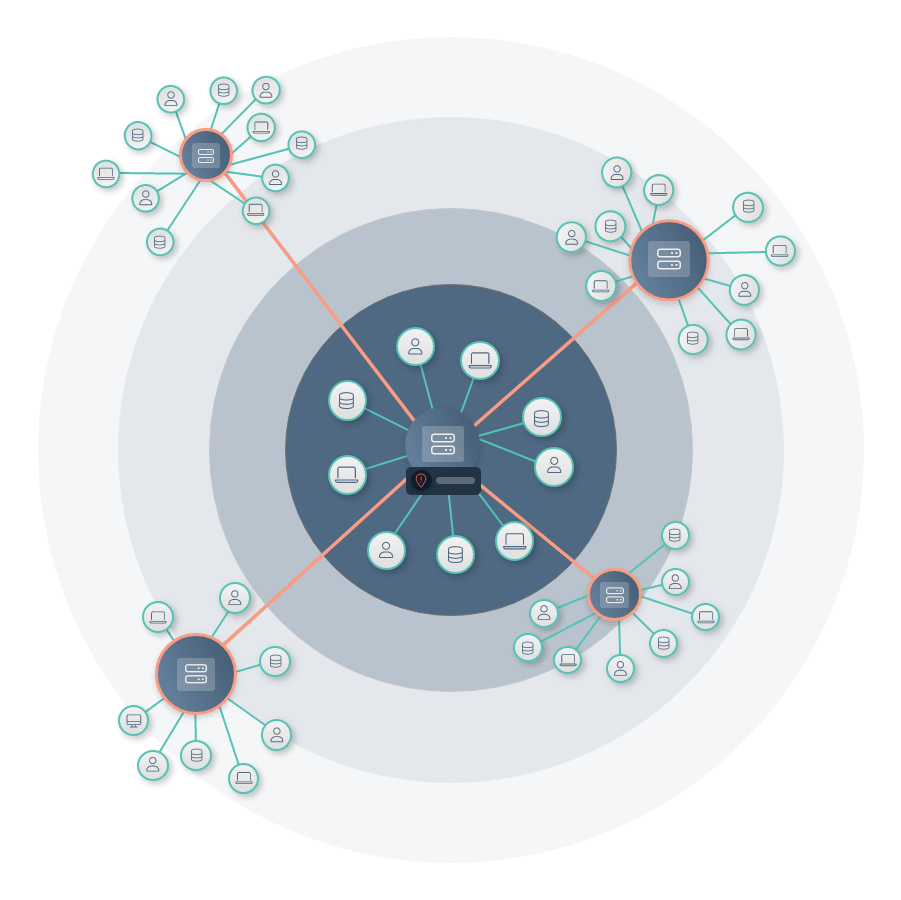
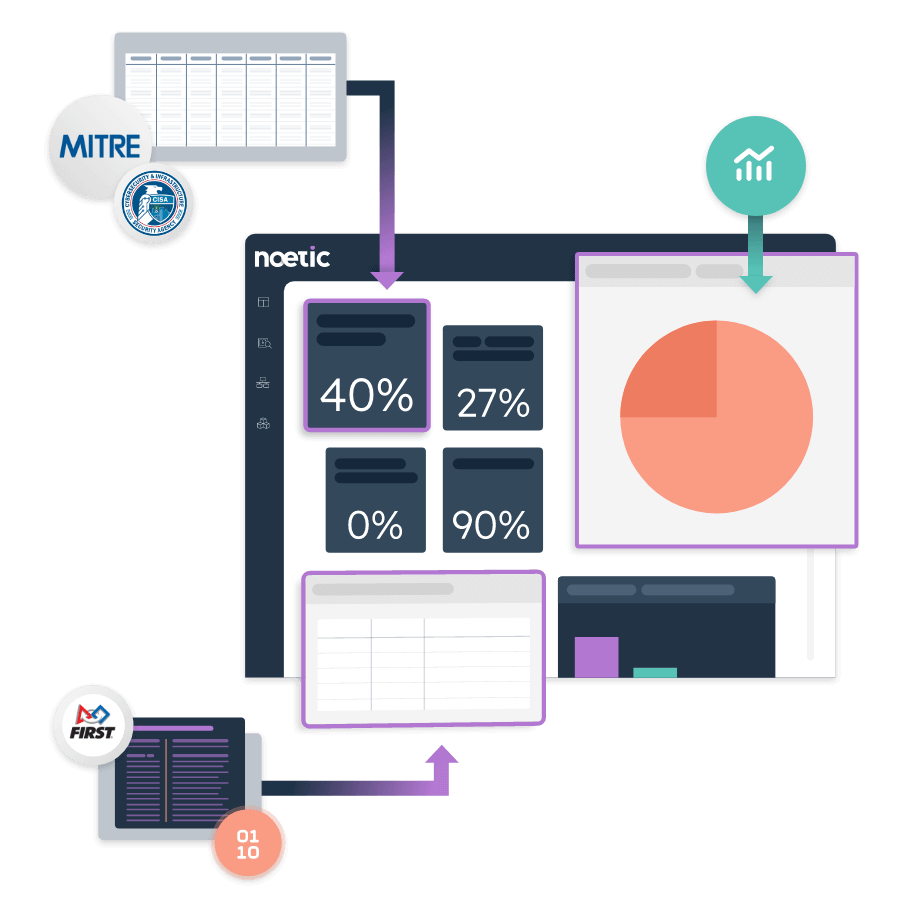
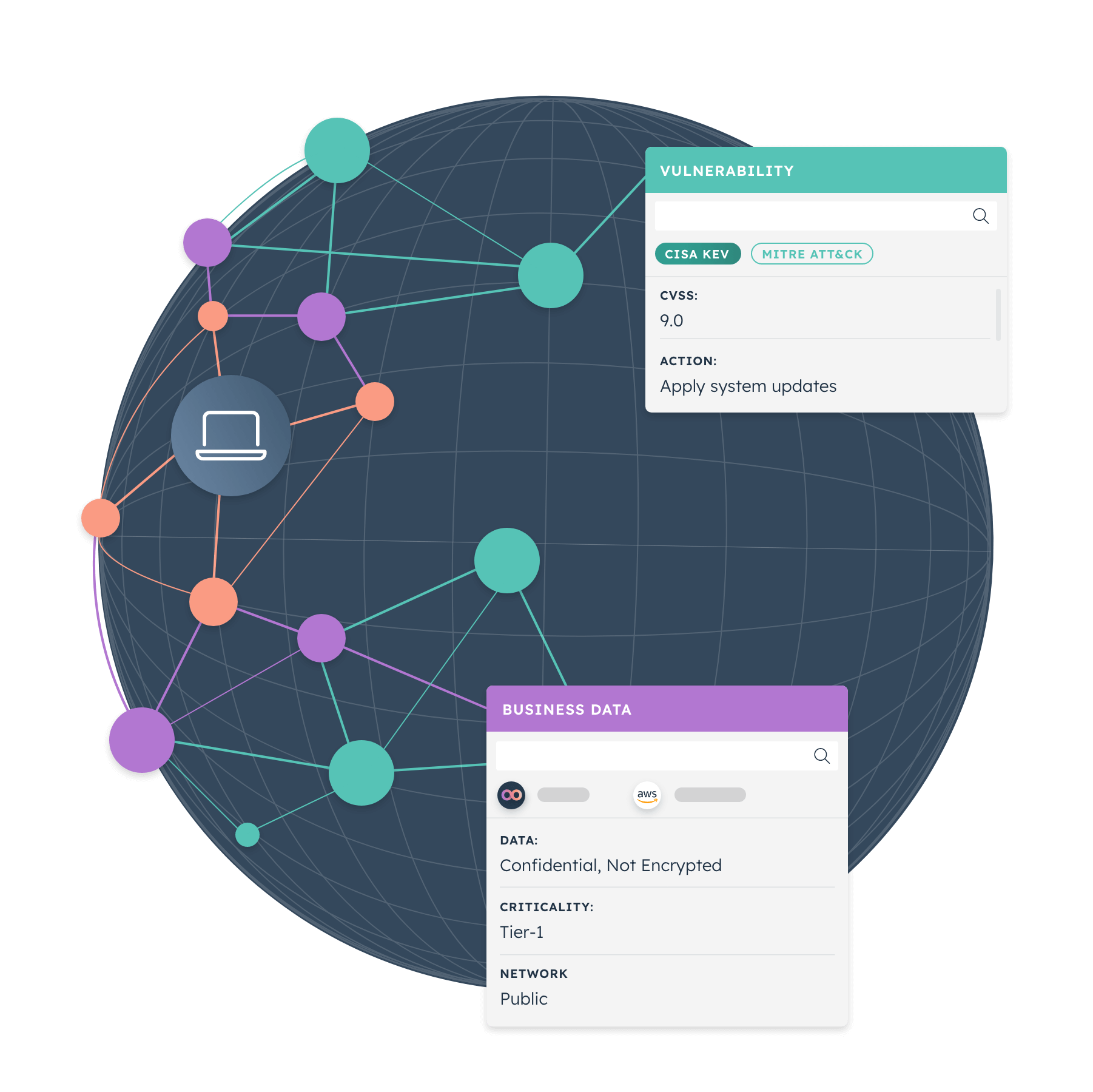
Though the role of the Chief Information Security Officer has evolved, today’s security leaders still face the same old challenges. Break out of the response cycle with dynamic cyber risk intelligence powered by Noetic.