The growing importance of Attack Surface Management
The recent Gartner® report highlights the need to increase visibility and prioritize security hygiene
Gartner recently released a new report on ‘Innovation Insight for Attack Surface Management’ (ASM), covering the growing need faced by security teams to manage an expanding attack surface. This is a subject that Gartner has addressed more frequently in 2022, stating in the recent ‘Top Trends in Cybersecurity 2022’ report that security and risk management leaders should ‘anticipate the continuous expansion of the enterprise attack surface, and increase investment in processes and tools…’
We see the continued expansion of the enterprise attack surface as a reflection of the change in modern digital infrastructure. Organizations are running systems on multiple cloud environments, as well as traditional on-premises. The growth of containerization, SaaS applications and the hybrid workforce have all led to an expansion, and the development of new attack surfaces to identify and protect.
ASM the first pillar of Exposure Management
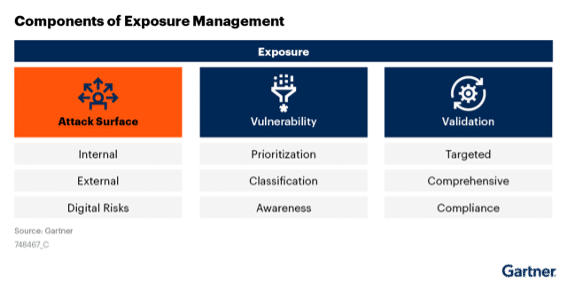
In the Gartner report, Attack Surface Management (ASM) is the first pillar in a set of wider capabilities referred to as ‘Exposure Management’, which also covers Vulnerability and Validation. ASM breaks down into three main capabilities – ‘internal’, represented by cyber asset attack surface management (CAASM), ‘external’ – external attack surface management (EASM), and ‘digital risks’ – digital risk protection services (DRPS).
Gartner describes the ASM pillar as addressing the question ‘What does my organization look like from an attacker’s point of view and how should it find and prioritize the issues attackers will see first.”
At Noetic, this is a common discussion with our customers. Given the current cybersecurity workload, it just isn’t possible for security teams to do everything. They need to prioritize, but the question is how? To focus on the right priorities, security needs to understand the cyber risk created by exploitable vulnerabilities, unsecured endpoints and common misconfigurations, but this needs to be aligned with business criticality. Resources like CISA’s known exploited vulnerabilities catalog are extremely valuable in helping to triage security workload and focus on the key risks to the business. Noetic’s approach to CAASM maps that along with other asset and business context to help deliver that prioritized list of issues to address.
CAASM, as defined in the report by Gartner ‘enables organizations to see all assets (internal and external) through API integrations with existing tools, query against the consolidated data, identify the scope of vulnerabilities and gaps in security controls, and remediate issues.’ The advantage of this approach is that it leverages the assets you already have. Noetic integrates with existing security, IT management and DevOps tools to identify unknown assets and map them into a graph database based on their cyber relationships.
Another key value provided by CAASM as identified by Gartner is the ability to remediate issues. Automation is at the heart of a modern CAASM solution and Noetic provides a comprehensive automation workflow engine that allows security teams to address common security control gaps.
Once a workflow has been configured, such as triggering the deployment of a missing EDR agent to a physical or virtual machine, then this workflow can be automated for any future scenario. If we can identify and automate common cyber hygiene use cases, then we can reduce the manual burden on the security team.
Key Benefits to adopting Attack Surface Assessment (ASA) capabilities
In the report, Gartner distinguishes between Attack Surface Management (ASM) as the ‘combination of people, processes, technologies and services deployed to continuously discover, inventory and manage an organization’s assets’ as opposed to Attack Surface Assessment, which is the ‘set of tools and services that may be used to achieve ASM’.
Gartner identifies several benefits that organizations might achieve through the adoption of ASA tools and services, which include:
- Improving asset visibility
- Understanding potential attack paths
- Quicker audit compliance reporting
- Actionable intelligence and meaningful metrics
These are tangible benefits in helping security leaders with important insights, prioritization and a reduction in team workload. At Noetic we also see CAASM and ASA tools helping to align security, IT and GRC teams by providing a unified view of assets, cyber risk and business applications. This creates better organizational alignment and focus on delivering key cyber objectives. Another critical benefit is the concept of ‘actionable intelligence’. This is where automation is critical. Security leaders need CAASM & ASA tools to solve problems, not just highlight them, visibility cannot be enough.
Getting Started with Attack Surface Management
Gartner estimates that by 2026 ‘20% of companies will have more than 95% visibility of all their assets, which will be prioritized by risk and control coverage by implementing cyber asset attack surface management functionality, up from less than 1% in 2022.’ This is a market, therefore, that is at the early stage of adoption today, but can serve as the foundation for an effective cybersecurity program.
Noetic is honored to be recognized as Representative Vendor for ASA by Gartner in this report. Our focus is on providing our customers with unparalleled visibility and asset intelligence for their whole cyber estate, with the tools to automatically remediate common security use cases and control drift. This aligns very well with Gartner’s definition and vision for CAASM.
To read more Gartner recommendations on how organizations can manage their growing attack surface, go here for complimentary access to this report.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner, Innovation Insight for Attack Surface Management, Published 24 March 2022, by Mitchell Schneider, John Watts, Pete Shoard
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from https://www.gartner.com/reprints/?id=1-29W0W4XB&ct=220427&st=sb
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
