Improving security posture by eliminating endpoint security coverage gaps

Cybersecurity Asset Management use cases #1: Endpoint Security
This blog is the first in an ongoing series where we will look at the common use cases for cybersecurity asset management today. Good asset management is a foundational component of an organization’s cybersecurity strategy and supports a wide range of use cases, according to the UK’s National Cybersecurity Centre (NCSC), ‘if you want to apply security controls, knowing what assets you have in your environment is fundamental.’ This blog looks at the important role cybersecurity asset management can play in endpoint hygiene and security best practices.
In August, a withering US Senate report revealed multiple cybersecurity failings across government. Among these, it claimed that the Department of Transportation had no record of over 14,000 of its IT assets. Unfortunately, these stories are increasingly common, across all verticals. The visibility gaps they describe offer threat actors a wealth of opportunities to breach their victims. Addressing these blind spots is critical to minimizing enterprise cyber risk. But how can security teams do so when their existing tooling offers only static and siloed visibility?
The answer is to gain comprehensive, contextual insight via existing third-party security investments and use this data to map the critical relationships between IT assets and the business. With this approach, organizations can spot and fix issues faster before threat actors have a chance to exploit them. It’s all about super-charging cyber-hygiene with continuous cybersecurity asset management.
An endpoint explosion
Even before the pandemic, enterprise endpoint volumes were exploding with virtual machines, containers, and cloud infrastructure. The advent of mass remote working has added a whole new fleet of potentially unmanaged devices to many organizations. This is the new reality of endpoint management today. The sheer complexity and volume of this distributed computing environment makes manual operation impossible. Not only are many remote working devices potentially undocumented, but virtual assets are ephemeral and temporary in nature, and therefore harder to track—stretching under-resourced IT and security teams to the limit.
All of this creates an unknown and unseen attack surface with plenty of coverage gaps for threat actors to aim at—which they’re doing with increasing frequency. A report last year revealed that internet-connected computers alone experience 1.5 attacks per minute.
It’s part of the reason Endpoint Detection & Response (EDR) and Extended Detection & Response (XDR) has become so important to enterprise security.
The work of threat actors is made easier because most organizations can’t gain a comprehensive and continuous view of all their assets. Cloud systems, Configuration Management Databases (CMDB), vulnerability scanners and EDR tooling offer different perspectives, but not the whole picture. An EDR or XDR platform can’t tell you anything about the endpoints it’s not installed on, for example.
It’s no surprise that 71% of global IT leaders admit to finding new endpoints in their environment on a weekly basis. Yet the stakes couldn’t be higher. Just a single unpatched server or misconfigured endpoint could lead to a crippling ransomware outage or serious data breach. Just ask Kaseya, Equifax, Marriott, and many more corporate victims over recent years. Over a quarter (27%) of respondents to a 2019 study said they’d experienced a breach as a result of an unpatched bug, for example.
A better way
The question is how can organizations close these critical coverage gaps and automatically remediate in line with policy? Gaining 100% visibility into assets is the first crucial step, and the best way of doing that is to build a multi-dimensional map of all assets, their current state, and the cyber relationships between them using the insights provided from multiple existing enterprise tools. Noetic does this via agent-less connectors that integrate with the published APIs of public clouds, vulnerability scanners, CMDBs, EDR tools and more. We then generate holistic insight by looking for three things:
- New assets that show up in the environment, e.g., a new VM
- Assets that disappear, e.g., a laptop that’s been decommissioned
- Anything indicating a new cyber relationship between two or more assets
The third bullet is perhaps the most important, because it’s with information about these relationships that we can build up a more accurate picture of enterprise cyber risk. We then build temporal graphs of a customer’s environment according to the three change categories defined above. Why? Because, as Microsoft’s John Lambert noted several years ago: “defenders think in lists, attackers think in graphs.”
What he meant was that attackers often use graphs to probe for vulnerabilities and map the potential paths between assets, until they find a way to move laterally and reach their target. The same methodology can be used by defenders to understand where to prioritize remediation efforts. A virtual machine in a development environment which has no sensitive data residing on it is not likely to be a priority for patching. Whereas an internet-facing asset supporting a business-critical application would be.
Managing risk on the endpoint
This approach enables IT and security teams to take a risk-based approach to endpoint security which focuses limited resources on the most critical issues. Consider the following endpoint scenarios:
- Endpoint policy enforcement – Set up a continuous query that searches for machines without an endpoint agent. (A “machine” is a concept in the model that could be generated from cloud data, vulnerability management tools, EDR, CMDB, Active Directory or other tools.) Once Noetic has identified these machines, it either enrolls them in the EDR management console to push the software client down, notifies the asset owner that they need to install the software, or potentially isolates the machine from the network if it’s a high-risk device. All these different paths could be configured via the automation workflow engine.
- Mobile Device Management – Alongside virtual and physical endpoints, Noetic also covers unmanaged mobile, IoT and other devices which can’t support traditional endpoint agents. Policy here could restrict access or impose additional controls, like multi-factor authentication (MFA) for mobile.
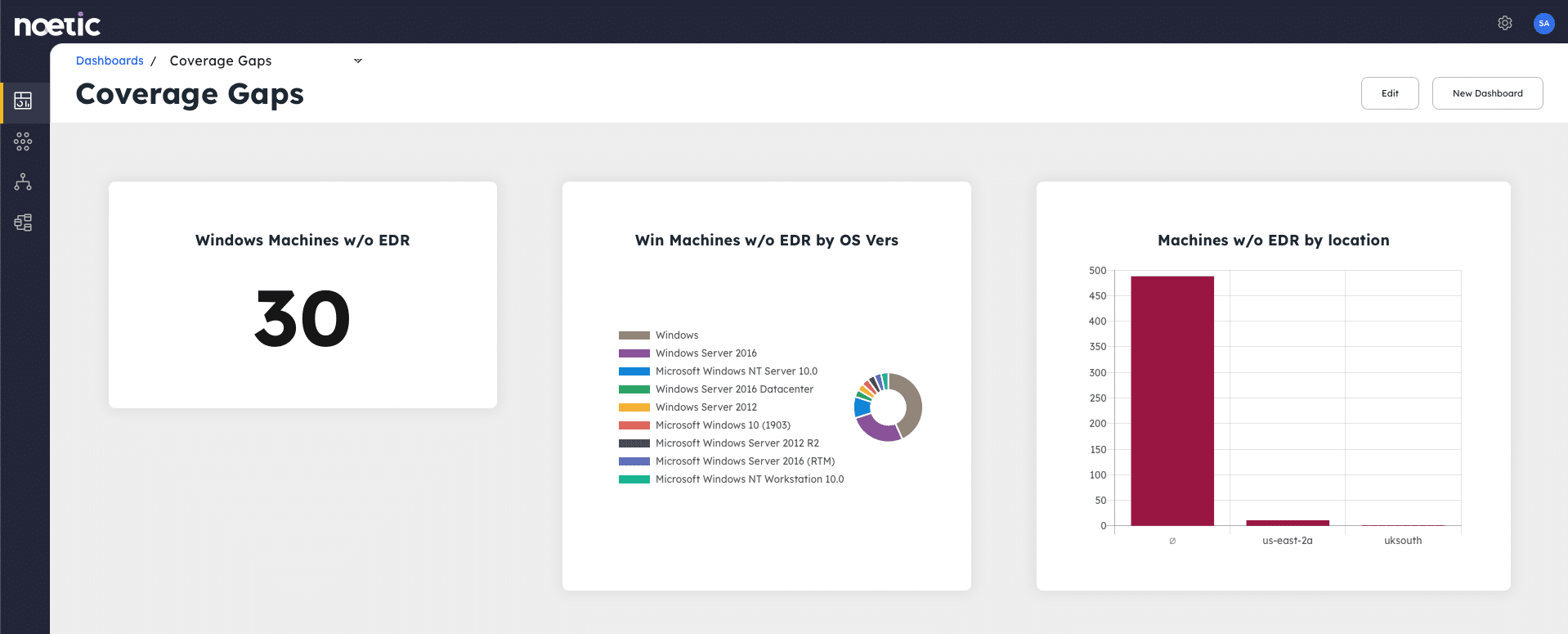
Closing any endpoint security gaps and continuously enhancing cyber-hygiene in line with policy offers organizations the best opportunity to minimize cyber risk. That’s the way to optimize resilience even as the threat landscape and corporate attack surface continue to evolve at pace.
We recently announced a partnership with SentinelOne, which is a great example of how Noetic can leverage endpoint and cloud telemetry to deliver better insights.
If you’re interested in understanding more about how Noetic adds value to your EDR investment, check out this video from our Director of Sales Engineering, Chris Neely, as he walks through the endpoint security use case
