In the Loop with Noetic’s Continuous Cyber Asset Management and Controls platform

I’m delighted to finally be able to share the results of my team’s hard work over the past 18 months, as today sees the launch of Noetic Cyber and the availability of our Continuous Cyber Asset Management & Controls platform.
We will be posting more soon about the different capabilities of the platform, but for this first blog I wanted to provide a high-level overview of the core features and the customer needs it has been designed to meet.
As Paul says in his blog, we have worked with many CISOs and design partners to ensure that we had a clear understanding of the challenges that security teams are having with cyber asset management today, and to validate the approach that we’ve taken is one that would meet their requirements and deliver significant value. The technology we’re introducing today is in part a product of those conversations, and we greatly appreciate the time and thoughtfulness of our advisors and design partners.
Our starting point for our solution was that static security processes were not sufficient for today’s dynamic IT environment, as Microsoft’s John Lambert said back in 2015 “defenders think in lists, attackers think in graphs” and unfortunately too often this is still the case. Security teams need real-time visibility into their ever-changing digital infrastructure, but with the relevant context to help them prioritize. They don’t need a list of assets, they need a map of the relationship between assets, organized in a way that provides important cyber insights and highlights the most critical risks.
Our experience working together at Resilient Systems also guided our approach to building out orchestration and automation. We understand the value automation provides in streamlining security processes, and reducing the manual burden on overworked security analysts, but also its limitations. Automation works best closest to high-fidelity data, this provides a solid basis for consistent, repeatable processes. If security teams have this building block in place, then they can make better decisions based on a true, accurate understanding of their security posture, and automate its ongoing refinement.
We also knew that we had to extract value from the existing technology footprint. By leveraging API access to already-deployed security and IT management tooling, we would be able to build on their insights, without creating more complexity.
The Noetic solution is designed to deliver that ‘single source of truth’ for all assets and entities in the organization and to make that outcome driven. We think of it as providing two distinct ‘loops’ that drive action.
The first loop is focused on visibility – teams need to understand ‘what assets are we protecting?’ To do that they need they need ‘full-stack’ visibility, a bottoms-up understanding of technical information about devices, networks, vulnerabilities, but they also need to understand the business context, so ‘top-down’ visibility provides insights into application criticality, process, and ownership. Using the OpenAPI standard, we leverage your existing tools to continuously discover, aggregate, and correlate the information and insights into a single, unified view, building an always accurate registry of your environment. That consolidated view allows users to build a time-based graph which also records the important relationships between assets and other entities.
By building this graph-based map of all assets, entities, and the relationship between them, we can continuously discover coverage gaps as the environment drifts based on the consolidated insights and relationships held in the graph. The tightly integrated orchestration and automation engine is then able to automatically react to these coverage gaps.
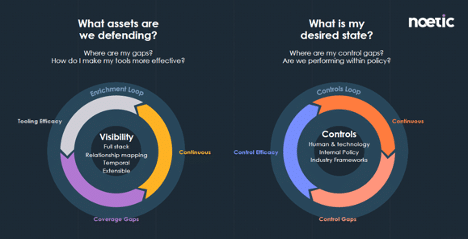
The second loop is similar, but more focused on the ‘desired state’, as opposed to the reality. Here we are looking at Continuous Controls Monitoring (CCM), the capability to automate the assessment and evidence collection of your organizations control effectiveness and compliance status. This could be based on a predetermined internal control, or a common industry framework such as ISO27001, CIS or NIST CSF.
In both loops, we are gathering information on the state of assets and entities and building a correlated entity model that allows us to continuously discover and remediate security coverage gaps, policy violations and common misconfigurations in both cloud and on-premises environments. In future blogs, we will look at common use cases, and dig a little deeper into how the technology works, but in the meantime, I would encourage you to register here if you’re interested in finding out more about the technology.
