Incident Response needs context and visibility, Cybersecurity Asset Management can help

Cybersecurity asset management is most commonly associated with “left of boom” activities. That is, preventative measures which can help the organization to proactively mitigate the risk of a breach or serious security incident before it occurs. It’s about driving enhanced cyber hygiene through continuous visibility into critical assets and potential security gaps. But the truth is this same visibility can also add crucial context for security operations (SecOps) and Incident Response teams operating “right of boom”.
The key is how to maximize this visibility, by leveraging modern public APIs to access security and business data from across the enterprise, identifying and mining key information to help make better security decisions.
Under pressure and over-stretched
We all know threat volumes are growing, as the tools and know-how to launch relatively sophisticated multi-stage attacks are democratized via the cybercrime underground. As corporate cyber-attack surfaces grow thanks to pre- and post-pandemic digital investments, there are ample opportunities for threat actors to find gaps in protection. Among the most common are unpatched endpoints and misconfigured systems.
There were over 18,000 CVEs published in 2020 alone, amounting to 50 per day. That’s a major challenge for defenders. Separately, it’s estimated that over seven billion records leaked or breached in 2019 were due to misconfigured cloud and other systems.
On the other side of the “boom”, SecOps teams continue to struggle. Alert overload is a common issue, causing many security analysts to feel overwhelmed at work. That’s bad news for SecOps teams already stretched to the limit. But even with the best SIEM, SOAR and XDR tools in place to help triage alerts for investigation, teams can face delays and roadblocks when trying to drill down for more detail. That can impair investigations, slow incident response, and sap productivity. To gain the full visibility they need into incidents, responders must go to multiple sources of data, and even then, may find it challenging to stitch it all together.
Cybersecurity Asset Management to the rescue
This is where cybersecurity asset management can provide significant value, both in accelerating the incident response (IR) process and facilitating threat hunting. SIEM and other detection tools will tell your analyst that something’s wrong, but they typically don’t provide enough contextual information for SecOps teams to know which is the most important suspected incident. The right kind of asset management platform will give you that context, allowing investigators to drill down by machine, user, network, and IP to determine the “blast radius” of attacks, or impacted users, and help to stop the bleeding.
It could uncover anything from a machine on a critical path of a key application, or a user who has access rights they shouldn’t. It’s all about reducing unknown unknowns, accelerating triage, and helping understand what the immediate risk is to the business, which detection and response tools typically won’t cover. With this information, alerts can be escalated or deprioritized accordingly. By providing IR teams with insights based on business criticality, we can ensure that they focus on the incidents that could be the most impactful to the business.
The Noetic difference
Noetic offers exactly this kind of visibility. Our agent-less connectors use published APIs to continuously analyze data from your existing security and IT management tools to record new assets, any recently disappeared assets, and the complex cyber relationships between these assets. We plot this information using a highly intuitive graph database which allows us to think like an attacker, looking for lateral relationships between machines, networks, users, vulnerabilities and more.
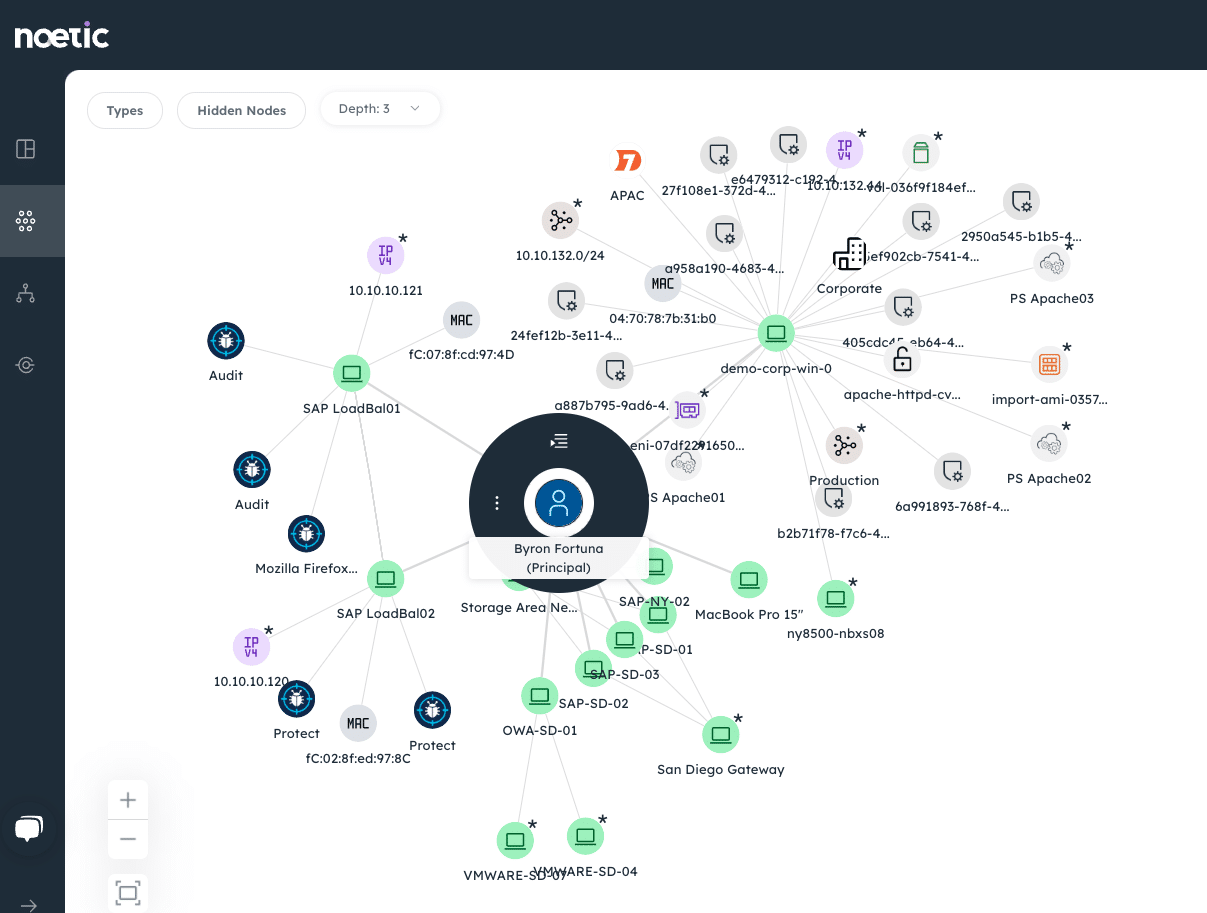
The goal is to understand more about your own environment than the attacker does, if we have good ‘cyber cartography, then we can accurately plan a response. If SecOps teams can better understand the connections between the assets they know and the cyber impact on related systems, then they are better able to assess the risk and prioritize their response.
Noetic’s value isn’t just in the way it displays data but the breadth of data it leverages. We use feeds from across the enterprise to provide unparalleled visibility. These sources could include cloud management tools; endpoint security agents; network-level information from Active Directory and DNS services; Kubernetes and container systems; CMDBs; vulnerability management solutions; identity & access management (IAM) systems and more.
Success in threat detection and response is measured in how quickly teams can identify, block, and remediate attacks. By providing instant access to this information, the productivity of the SOC can be significantly increased. Any common enrichment process can also be automated and scheduled, so the information is continuously available to the security analysts, updated as the environment changes.
Context and insight are critical to SOC teams to help them triage suspected incidents and isolate compromised machines. The asset intelligence that Noetic provides is key to helping them to detect and remediate threats. Check out our website to find out more about the Noetic platform or register for a product demo.
