Noetic provides a proactive approach to cyber asset and controls management, empowering security teams to see, understand, fix and improve their security posture and enterprise ecosystem.
© Copyright 2023 Noetic
Watch our rapid-fire, three-minute demo to learn how easy our solution is for managing your threats and vulnerabilities.

Platform Features
Gain visibility into all your entities and visualize your cyber environment to truly understand business impact

Get real-time and historical data to triage alerts and make the right decisions at the right time

Automate security controls across any entity to quickly identify gaps and blind spots and automate remediation

Proactively improve security posture and adopt internal or industry frameworks to ensure systems are continuously improving through automated, continuous assessment

Noetic integrates with native apps, customer developed apps and 3rd party security and IT management tools through standardized, extensible APIs

With simple setup and agent-less connectors into existing tools, the Noetic platform can quickly provide actionable insights

Sophisticated analytics empowers you with a deep understanding of the progression of your cyber environment over time

Gain visibility into all your entities and visualize your cyber environment to truly understand business impact

Get real-time and historical data to triage alerts and make the right decisions at the right time

Automate security controls across any entity to quickly identify gaps and blind spots and automate remediation

Proactively improve security posture and adopt internal or industry frameworks to ensure systems are continuously improving through automated, continuous assessment

Noetic integrates with native apps, customer developed apps and 3rd party security and IT management tools through standardized, extensible APIs

With simple setup and agent-less connectors into existing tools, the Noetic platform can quickly provide actionable insights

Sophisticated analytics empowers you with a deep understanding of the progression of your cyber environment over time
Download the complimentary Gartner® report: ‘Innovation Insight for Attack Surface Management’ for recommendations on how organizations can manage their growing attack surface.
Join us in Las Vegas to discover how Noetic closes the loop in cyber asset management.
Join us for a 30-minute walkthrough of Noetic’s continuous cyber asset management & controls platform, and see how security teams can increase asset visibility, defend against growing attack surfaces, and better understand their security posture


Noetic supercharges asset discovery and makes it easy to visualize and analyze the relationships between all your assets and entities, delivering actionable visibility to enterprises when it matters most.
Connect to information across your entire estate – from discovery tools such as Rumble, security applications including EDR and vulnerability scanners, IT systems management centers and CMDB, cloud platform, container and virtual machine (VM) infrastructure, identity and access management infrastructure, SDLC tools and more – to build a continuously-updated single source of truth, delivered through a graph database.
Security teams can use this correlated graph to quickly identify and assess coverage gaps, understand and address any data quality issues, and prioritize action. Make the most of your current tools while enhancing network visibility and delivering time to value.
Noetic easily connects with and enhances current endpoint security tools, providing enterprises with next-level visibility into their security posture. Endpoint Detection and Response (EDR) tools are effective at dealing with threats, but they can only protect the systems they are deployed on.
Connect easily with endpoint security tools such as SentinelOne, CrowdStrike and Windows Defender ATP to quickly identify and assess protection coverage across multiple tools, understand relationships to critical users and systems, analyze vulnerabilities and misconfigurations, and provide comprehensive and actionable insight to help teams continuously secure endpoints and maintain a resilient security ecosystem.
Noetic improves vulnerability management capabilities by providing a consistent view of your continually changing security environment, empowering teams to make decisions based on complete, real-time insight.
Noetic easily imports results from existing tools such as Rapid7, Tenable and Qualys, enabling security teams to identify gaps in completeness or timeliness, prioritize work based on a comprehensive understanding of asset ownership and context, and build automation around scanning and remediation.
Integration with common Patch Management tools such as BigFix or Microsoft SCCM means that Noetic can deliver end to end automation workflows that understand where the high-risk vulnerabilities are on business critical systems, and ensure that the remediation process is complete.
As a result, security teams know where to focus attention and can drive continuous security posture improvement.
Noetic helps bring your entire IT estate together, optimizing current IT investments and delivering immediate value by exposing security gaps and shadow IT problems.
If you have a CMDB, Noetic can rapidly correlate its catalog with data from security tools and alerts, providing insight into data quality or coverage gaps, and enabling security decisions to make use of all available business context. Noetic can also easily connect to IT infrastructure such as Microsoft System Center Configuration Manager (SCCM), BigFix, as well as ticketing systems such as Jira and ServiceNow.
As a result, your security team can improve productivity, make data-driven decisions, and proactively improve your security posture.
Noetic champions flexibility with a focus on making it simple to embrace cloud and container infrastructure. Noetic’s pre-built connectors for common cloud uses cases can build a catalog of your AWS, Azure, Google, Kubernetes or VMWare resources – providing an accurate and continuously-updated baseline for the “as-built” estate.
By delivering a single view of cloud, container, and the traditional IT estate, the Noetic platform provides unique visibility to coverage gaps and misconfigurations. This helps improve security team efficiency from day one and enhance overall competitiveness by enabling organizations with the ability to understand and manage risk across modern rapidly changing environments.
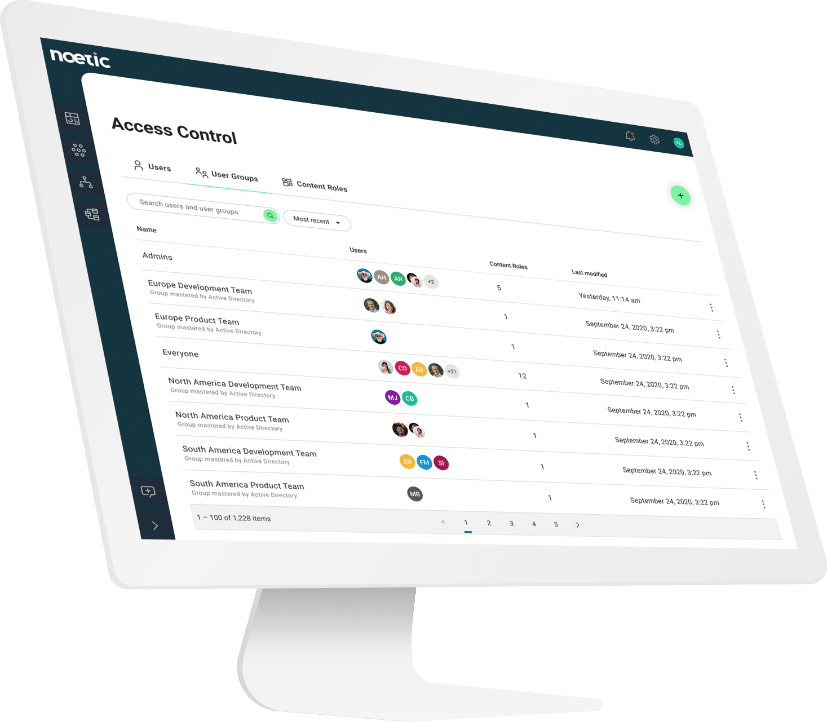
Appropriate access control and user behavior monitoring are critical elements of an organization’s security posture. Noetic connects to identity and access management (IAM) systems such as Active Directory, Okta, AWS IAM and others, to build a consolidated graph describing people, accounts, roles, permissions, and user activity in relation to the assets and resources that you are protecting.
Armed with current and comprehensive information, you can rapidly understand and address privilege boundaries, analyze the “blast radius” of misconfigured or compromised accounts or assets, and report on compliance.
Noetic supercharges asset discovery and makes it easy to visualize and analyze the relationships between all your assets and entities, delivering actionable visibility to enterprises when it matters most.
Connect to information across your entire estate – from discovery tools such as Rumble, security applications including EDR and vulnerability scanners, IT systems management centers and CMDB, cloud platform, container and virtual machine (VM) infrastructure, identity and access management infrastructure, SDLC tools and more – to build a continuously-updated single source of truth, delivered through a graph database.
Security teams can use this correlated graph to quickly identify and assess coverage gaps, understand and address any data quality issues, and prioritize action. Make the most of your current tools while enhancing network visibility and delivering time to value.
Noetic easily connects with and enhances current endpoint security tools, providing enterprises with next-level visibility into their security posture. Endpoint Detection and Response (EDR) tools are effective at dealing with threats, but they can only protect the systems they are deployed on.
Connect easily with endpoint security tools such as SentinelOne, CrowdStrike and Windows Defender ATP to quickly identify and assess protection coverage across multiple tools, understand relationships to critical users and systems, analyze vulnerabilities and misconfigurations, and provide comprehensive and actionable insight to help teams continuously secure endpoints and maintain a resilient security ecosystem.
Noetic improves vulnerability management capabilities by providing a consistent view of your continually changing security environment, empowering teams to make decisions based on complete, real-time insight.
Noetic easily imports results from existing tools such as Rapid7, Tenable and Qualys, enabling security teams to identify gaps in completeness or timeliness, prioritize work based on a comprehensive understanding of asset ownership and context, and build automation around scanning and remediation.
Integration with common Patch Management tools such as BigFix or Microsoft SCCM means that Noetic can deliver end to end automation workflows that understand where the high-risk vulnerabilities are on business critical systems, and ensure that the remediation process is complete.
As a result, security teams know where to focus attention and can drive continuous security posture improvement.
Noetic helps bring your entire IT estate together, optimizing current IT investments and delivering immediate value by exposing security gaps and shadow IT problems.
If you have a CMDB, Noetic can rapidly correlate its catalog with data from security tools and alerts, providing insight into data quality or coverage gaps, and enabling security decisions to make use of all available business context. Noetic can also easily connect to IT infrastructure such as Microsoft System Center Configuration Manager (SCCM), BigFix, as well as ticketing systems such as Jira and ServiceNow.
As a result, your security team can improve productivity, make data-driven decisions, and proactively improve your security posture.
Noetic champions flexibility with a focus on making it simple to embrace cloud and container infrastructure. Noetic’s pre-built connectors for common cloud uses cases can build a catalog of your AWS, Azure, Google, Kubernetes or VMWare resources – providing an accurate and continuously-updated baseline for the “as-built” estate.
By delivering a single view of cloud, container, and the traditional IT estate, the Noetic platform provides unique visibility to coverage gaps and misconfigurations. This helps improve security team efficiency from day one and enhance overall competitiveness by enabling organizations with the ability to understand and manage risk across modern rapidly changing environments.
Appropriate access control and user behavior monitoring are critical elements of an organization’s security posture. Noetic connects to identity and access management (IAM) systems such as Active Directory, Okta, AWS IAM and others, to build a consolidated graph describing people, accounts, roles, permissions, and user activity in relation to the assets and resources that you are protecting.
Armed with current and comprehensive information, you can rapidly understand and address privilege boundaries, analyze the “blast radius” of misconfigured or compromised accounts or assets, and report on compliance.
“In order for my team to be effective, they need to have a clear picture of what they’re trying to protect, and what that means to the business. What impresses me about the Noetic approach is the visibility and context it provides us, without adding integration effort and more complexity to my technology stack.”
“Meeting modern compliance management requirements are a complex and manual process for our Risk and Security team. Noetic proactively identifies compliance drift, and leverages automation to help manage it, allowing us to work smarter not harder. By combining first class automation with skilled human oversight, we can make our organization even more secure.”
“Having a clear understanding of what you need to protect is a critical part of a wider cybersecurity strategy. What’s significant about the Noetic approach is that it not only provides that visibility of technology, but links it to the business context of why it matters, and the ability to orchestrate and automate actions to manage the risks that are identified.”
“Noetic is a true market disruptor, offering an innovative way to fix the cyber asset visibility problem – a growing and persistent challenge in today’s threat landscape.”
“Good cyber asset management is foundational to addressing the inherent friction between the IT and security teams, as it provides both parties with an accurate view of assets to defend, potential security gaps and priorities to address. Noetic is able to help to bridge the gap between the CISO and the IT organization, with an innovative approach to cyber asset management that provides immediate value.”
Noetic provides a proactive approach to cyber asset and controls management, empowering security teams to see, understand, fix and improve their security posture and enterprise ecosystem.
© Copyright 2023 Noetic