What’s inside:
- Get a brief overview of CTEM and the benefits of adoption.
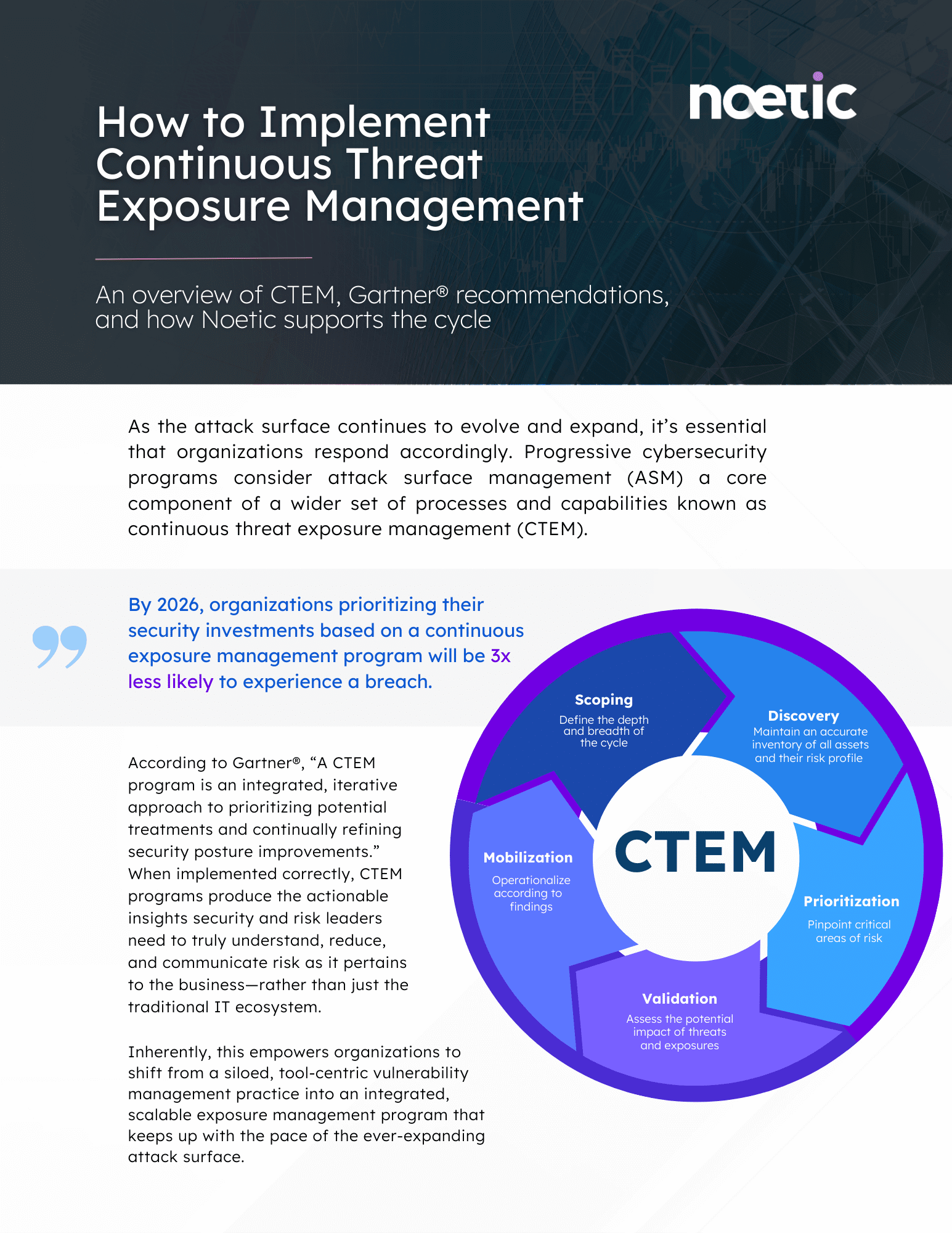
- Understand Gartner® recommendations for the 5 stages of the CTEM cycle: scoping, discovery, prioritization, validation and mobilization.
Noetic Cyber: Support throughout the CTEM cycle
Implementing a major security operations program as large-scale as continuous threat exposure management (CTEM) is an overwhelming task for any security and risk management team. By alleviating much of the burden associated with modern attack surface management, the Noetic platform enables organizations to confidently repair their broken threat and vulnerability management (TVM) system.
“CTEM is not a tool, it’s a program. In their effort to build a multifunction platform, security leaders should not get trapped into the vendor’s platform narrative, replacing the necessity to address all the assigned objectives of a CTEM program, with their approach of building a multifunction platform.”
The more you put in, the more you get out of the Noetic platform.
No single tool will ever provide the intelligence necessary to truly reduce risk on its own. While most security tools promise a “quick fix”, siloed lists only contribute to the noise.
Noetic promises a different approach. By leveraging the tools and datasets teams are already using, the platform extracts, correlates, and aggregates layers of insight to highlight critical areas of risk as it applies to each organization.
Prioritization powered by Noetic.
Get started today.
With dozens of pre-built connectors with agentless API integration, there’s no need to wait to start your CTEM journey with Noetic. Enter your information below for a 1:1 sales consultation with the Noetic Cyber team.
Gartner®, Implement a Continuous Threat Exposure Management (CTEM) Program. Jeremy D’Hoinne, Pete Shoard, Mitchell Schneider. July 2022.
Gartner® does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER® is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.