The State of Vulnerability Management in 2024
From the sheer volume of Common Vulnerabilities and Exposures (CVEs) published globally to the rise of generative AI in cyberattacks, we’ve gathered figures to describe the state of threat and vulnerability management in 2024. Join us as we dissect the data, explore emerging trends, and glean essential insights into the state of vulnerability management in the year ahead.
15 Statistics that Make the Case for Exposure Management
- Over 29,000 Common Vulnerabilities and Exposures (CVEs) were published worldwide in 2023, a 15% year-over increase. (Statista)
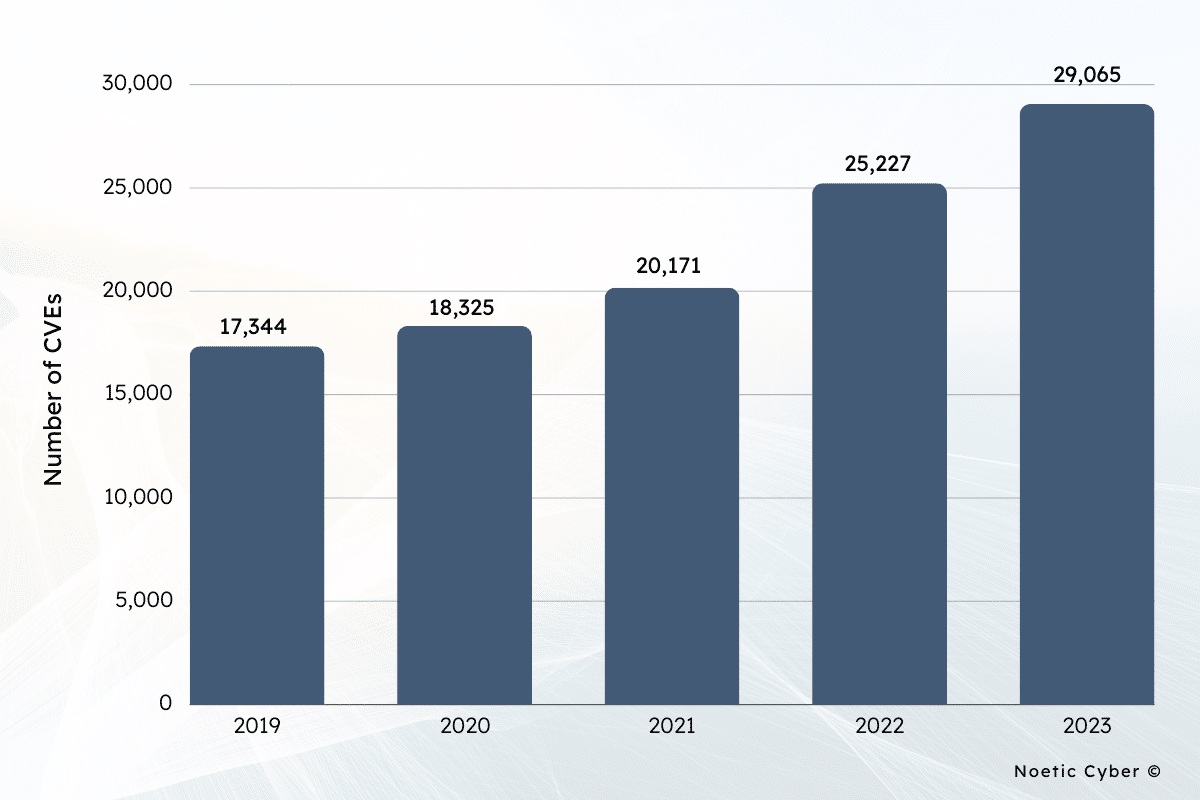
- Of the CVEs published in 2023, 7,786 (27%) had potential exploits, while a mere 159 (less than 0.5%) had weaponized exploit code available. (DarkReading)
The ever-growing number of Common Vulnerabilities and Exposures (CVEs) published globally shows the challenges faced by organizations in securing their digital landscapes. And despite the seemingly small percentage, the potential impact of even a handful of weaponized exploits can be severe, leading to data breaches, system compromises, and other security incidents. This emphasizes the critical importance of addressing and rectifying a broken threat and vulnerability management system.
Dynamic infrastructures necessitate a modern approach.
- Cloud attacks are the top concern for business and tech executives. (PwC)
- Over 45% of organizations’ high-risk, cloud-hosted exposures in each month were observed on new services that hadn’t been present on their organization’s attack surface in the month prior. (InfoSec Magazine)
- Cloud-related CVEs increased 194% between June 2022 and June 2023. (IBM)
- 85% of cybersecurity professionals attribute the increase in cyberattacks to the use of generative AI by bad actors (CFO)
Cloud environments are highly dynamic, with organizations frequently adopting new services and technologies to meet their evolving business needs. The rapid pace of deployment and ephemeral nature of cloud computing means that vulnerabilities emerge just as fast. Similarly, the use of AI by cybercriminals introduces a higher level of complexity and adaptability to their tactics, challenging traditional cybersecurity measures.
This necessitates a continual evolution in defense strategies to effectively counter the dynamic and technologically advanced landscape of cyber threats.
Traditional vulnerability and patch management protocols are missing the mark.
- Nearly half (49%) of IT and security professionals believe their company’s current patch management protocols fail to mitigate risk effectively, and most (71%) of IT and security professionals see patching as overly complex, cumbersome, and time-consuming. (VentureBeat)
- Most (71%) of IT and security professionals see patching as overly complex, cumbersome, and time-consuming. (VentureBeat)
- More than one out of every three applications (38%) were still running vulnerable versions of Log4j as of December 2023. (Veracode)
Traditional patch management protocols are increasingly revealing their limitations in the face of today’s complex threat landscape. Coupled with the rapid pace of technological advancements, modern exposure management demands a departure from conventional methodologies.
Automation is a strategic enabler for security and risk management teams.
- The human element is still a driver in most security incidents and is a factor in 74% of total breaches. (Verizon)
- 89% of cyber transformers rely heavily on automation. (Accenture)
These figures underscore the critical need for organizations to address not only technological vulnerabilities, but also human-centric aspects to fortify their defenses. Delaying the adoption of automation leaves organizations more vulnerable to evolving threats, emphasizing the urgency for embracing automated solutions. It is not merely a technological enhancement but a strategic imperative for organizations seeking resilience and adaptability.
Incident response (IR) teams are losing the race against the clock.
- Only one-third of companies that experienced a data breach discovered the incident through their own security teams, highlighting a need for better threat detection. (IBM)
- The average Mean Time to Remediate (MTTR) critical vulnerabilities was 65 days. (Edgescan)
In the fast-paced and constantly evolving cyber landscape, time is of the essence. when it comes to mitigating risk. Organizations must grasp the urgency of deploying rapid, risk-based remediation processes to address the most critical vulnerabilities promptly and minimize the adversary’s window.
It is evident that organizations must adapt their current vulnerability management processes to address the complexities of the digital ecosystem and provide a proactive defense against emerging threats and the potential risk to the business
Continuous Threat Exposure Management (CTEM) is a game-changer.
- A Gartner Peer Survey revealed 60% of respondents are either actively pursuing or considering a CTEM program.
- According to Gartner®, “By 2026, organizations prioritizing their security investments, based on a continuous threat exposure management program, will realize a two-third reduction in breaches.”
A notable shift is signaled, with organizations increasingly acknowledging and adopting Continuous Threat Exposure Management (CTEM) program as a cornerstone of their security initiatives. As the data suggests, embracing CTEM not only reflects a proactive response to identifying and managing high-risk vulnerabilities and exposures, but also promises substantial reductions in the frequency and impact of breaches, positioning it as a transformative force in the realm of cybersecurity.
Threat and vulnerability management programs in 2024 are marked by a compelling array of challenges and opportunities. The limitations of traditional patch management protocols and the growing significance of automation underscore the need for organizations to adopt a more agile, risk-based approach to vulnerability management. As incident response teams grapple with time constraints, the urgency of delivering contextual insights to help them triage suspected incidents becomes evident.
Explore more benefits of embracing CTEM in our eBook: in our exclusive eBook: How to Implement Continuous Threat Exposure Management (CTEM) with Noetic.
Change is on the Horizon
As we continue to navigate the complexities of the digital ecosystem, the data points towards a transformative horizon, with security leaders increasingly adopting CTEM as a strategic initiative. Security teams that look to modernize their approach to vulnerability management by embracing the CTEM process are working to improve their overall security posture, reduce the incidence and severity of data breaches while enhancing their team’s operational efficiency and effectiveness.
It is evident that organizations must adapt, embrace change, and prioritize agile, risk-based strategies to fortify their defenses in the dynamic cybersecurity landscape of 2024 and beyond.
Gartner®, Top Strategic Technology Trends for 2024: Continuous Threat Exposure Management, 2023. Jeremy D’Hoinne, Pete Shoard
