Cyber Transparency: Shining a Light on Security
Jamie Cowper, VP of Marketing had the opportunity to sit down with Richard Horne, a distinguished member of the Noetic Advisory Board. Together, they discussed the challenges confronting organizations in the ever-evolving landscape of cybersecurity. Drawing from his extensive experience advising boards and executive committees, Richard provided valuable insights into the indispensable role of cyber transparency.
Cultivating a culture of cyber transparency is no longer just a matter of compliance. From internal stakeholders to insurers and regulators, there’s a resounding call for organizations to shine a light on their security practices.
The Need for Greater Cyber Transparency
In a landscape defined by escalating regulatory pressures, stakeholder expectations, and insurance imperatives, maintaining transparency in cybersecurity practices has emerged as a cornerstone for fostering trust, accountability, and cyber resilience.
Evolving regulations such as those issued by the SEC and NIST are not only insisting that organizations take proactive measures to truly understand their cybersecurity risk; but they have also reinforced the importance of stakeholder oversight. These expectations have transcended mere compliance audits, permeating boardroom discussions where cybersecurity is now recognized as a top priority by 73% of board members.
Investors have also amplified their concerns, advocating for greater ongoing visibility into their organization’s security posture. In fact, 81% of IT and business decision makers say they are putting more of a focus on a target company’s cybersecurity posture now than they have in the past. These stakeholders are no longer content with surface-level assurances; instead, they demand a clear and comprehensive view of the measures in place to safeguard sensitive data and demonstrate stability of a business.
Simultaneously, the imperative for enhanced transparency in cybersecurity practices is further underscored by changing trends in cyber insurance. Over the past three years alone, cyber insurance claims have surged by 100%, accompanied by a staggering 200% increase in insurance payouts. Consequently, insurers are now demanding more granular, “pre-binding” contingencies, seeking evidence of ongoing progress in implementing effective controls over time.
The Five “C’s” of Transparent Cyber Risk Communication
Thus, mastering the art of transparent cyber risk communication becomes imperative. This journey towards clarity and openness hinges on embracing the five “C’s” of cyber transparency: comprehension, context, customization, conciseness, and consistency.
- Comprehensive
Rather than simply listing vulnerabilities or threats, effective communication of cyber risk requires organizations to adopt a holistic approach that includes not only technical aspects, but also provides transparency into the organization’s overall security posture. Additionally–wherever applicable–be sure to also offer practical recommendations for mitigating cyber risks, such as implementing specific security measures or technologies. Clearly articulate the steps that stakeholders can take to reduce their exposure to cyber threats.
“We’re seeing quite a bit of organizations trying to get more of a percolated, ground-up view of, ‘what’s our cyber risk?’, and starting with a lot of detail around assets, and you’re building up a view from there to a more comprehensive overview that gives them a defensible position.” –Richard Horne, Noetic Advisory Board Member
- Contextual
Help stakeholders understand the broader context of cyber risks by explaining the relevance of specific threats to your organization’s industry, business objectives, and regulatory environment. By illustrating how cyber threats can disrupt operations, damage reputation, or incur financial losses, stakeholders are motivated to allocate resources towards robust cybersecurity measures that support overarching business objectives.
Articulating cyber risks within the regulatory environment also clarifies the legal and compliance obligations that organizations must navigate. Communicating how specific threats relate to regulatory requirements not only emphasizes the legal imperative for cybersecurity but also reinforces the organization’s commitment to compliance and risk management.
- Customized
Communication methods and content must be suited to the needs and preferences of different stakeholders, including board members, investors, and insurers. Executives may require high-level summaries, while technical teams may benefit from more detailed information.
Let’s say, for example, the organization is coming up on its annual budget meeting, and the board is seeking information around which cybersecurity controls and mitigation strategies can yield the greatest return on investment in terms of risk reduction and resilience. At the same time, the cyber insurance policy is coming up on its renewal date, and the insurer is requesting evidence for twelve specific controls. While both reports require visibility into your controls monitoring and policy enforcement capabilities, each must be tailored to address the audience’s specific concerns and priorities.
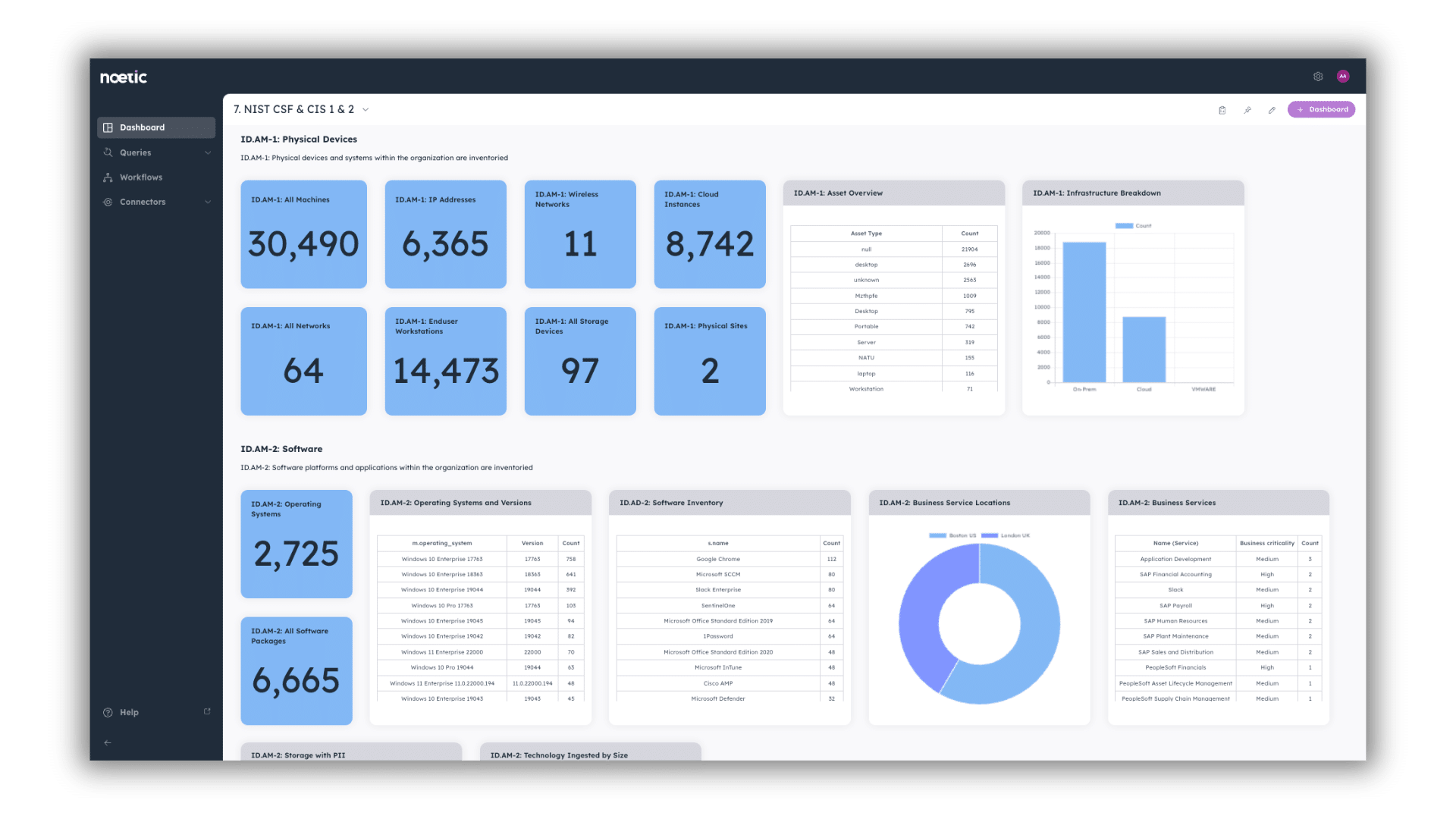
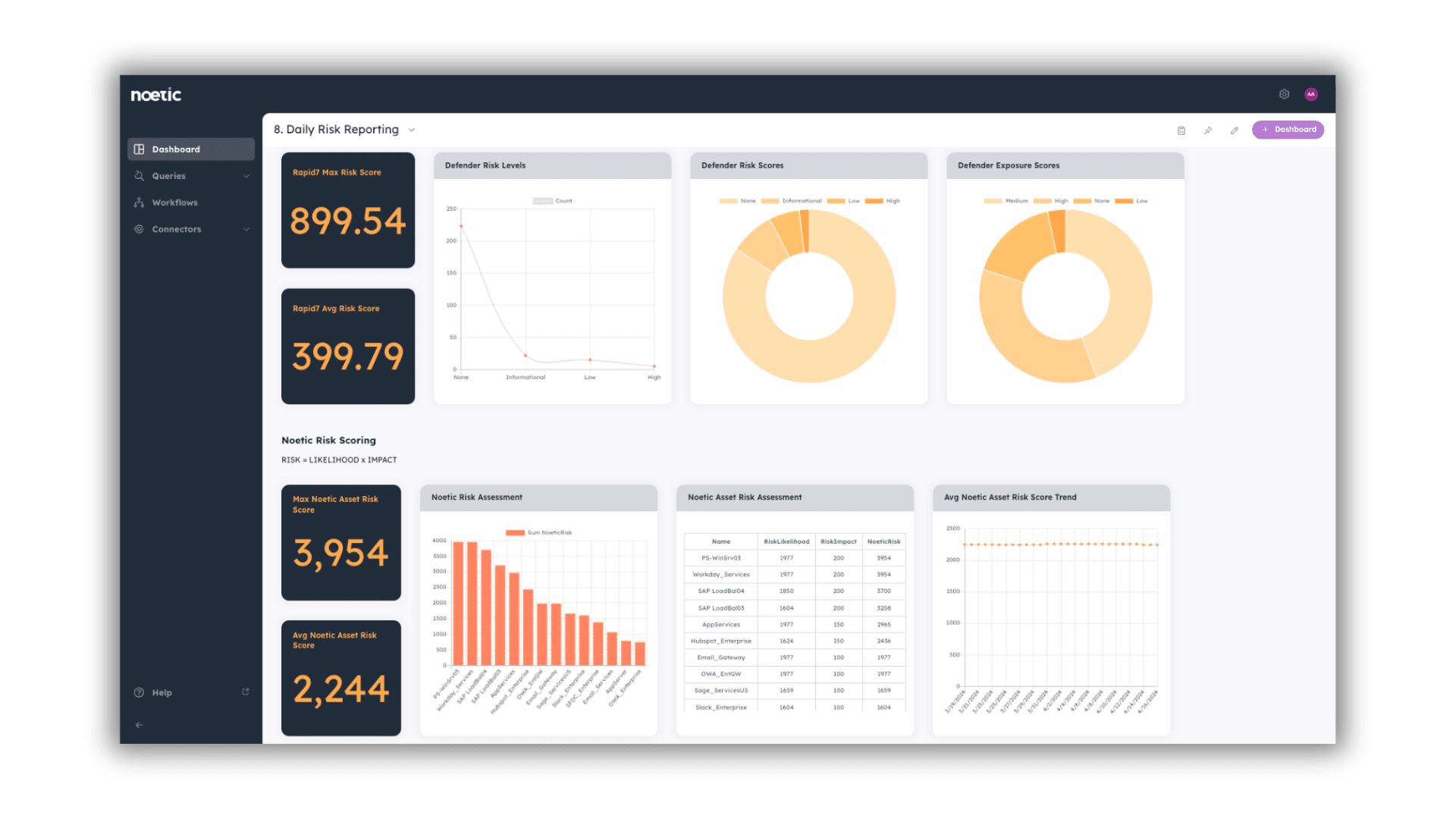
- Concise
It’s also important to be succinct in your communication, focusing on the most critical points and avoiding unnecessary details. Use bullet points or summaries to highlight key takeaways and make information easier to digest and overwhelming your audience with unnecessary details or technical jargon.
It can be especially helpful to incorporate visual aids such as charts, graphs, and infographics to illustrate key points and trends. Visual representations can help clarify complex information and make it easier for stakeholders to grasp.
- Consistent
Finally, regular updates and reminders serve to reinforce key messages and ensure that cybersecurity remains a top priority for stakeholders at all levels. Consistent communication helps to keep cyber risks top of mind for stakeholders, preventing complacency and reinforcing the importance of cybersecurity measures. Be sure to identify any opportunities for automation to avoid draining resources that are already spread thin.
As we continue to navigate the challenges and opportunities of the digital age, we should embrace transparency as a guiding principle in our collective efforts to secure the future.
By adopting a holistic approach, providing relevant context, tailoring communication to meet the needs of different audiences, being concise yet comprehensive, and maintaining consistent engagement, organizations can foster a culture of transparency that strengthens trust, enhances resilience, and safeguards against evolving cyber threats.
Check out the podcast for more insights from our full interview with Richard: Securing our Future, ep. 2: Resilience, Transparency and Transformation.
