Defining Assets in Cybersecurity Asset Management
The key to any successful cybersecurity program is first understanding what it is you are responsible for. However, building and maintaining an effective cyber asset management strategy is still problematic as many organizations struggle with how to define cybersecurity assets.
The historic definition of a cyber or IT asset is no longer relevant, as the complexity of modern infrastructures has transformed what was once the most basic concept in IT asset management into one of the most challenging. Though it may be difficult, it’s not impossible. When done correctly, a complete cyber asset inventory creates the foundation to improve security posture and reduce the attack surface. So, what is a cyber asset?
What is a cyber asset?
Originally, NIST defined an asset(s) as “the data, personnel, devices, systems, and facilities that enable the organization to achieve business purposes.” The UK’s National Cyber Security Centre defines asset as “anything that can be used to produce value for your organization.”
More recently, the CISA Binding Operational Directive (BOD) 23-01 implemented asset discovery requirements for any IP-addressable networked asset assigned to an and accessible via an IPv4 or IPv6 address—whether that’s on-premises, cloud, or otherwise.
But if an asset is anything that produces value to a person or organization, then a cyber asset is anything that contains cyber relevance. Yet, most cybersecurity asset management programs consist only of the hardware, software, firmware and other network assets that belong to the organization itself. As our world continues its digital transformation, the way in which we visualize our environments must follow suit.
Examples of assets in cybersecurity include:
- On-premises devices
- Cloud storage
- Software and applications
- Security controls
- VPNs
- Employees and User Identification Applications
- Networks
- Datasets
- Processes and policies
However, this is not a comprehensive list. Traditionally, IT asset management (ITAM) programs involve the discovery, assessment and maintenance of tangible, mostly physical assets. Based on this new-and-improved definition of asset, anything from an IP address to an IoT device should be included in your security hygiene and posture management best practices.
That means intangible assets–business units, data, etc.–are just as (if not more) critical to understanding and managing the organization’s security posture. Therefore, it’s no surprise the inability to identify all assets is one of the top challenges cybersecurity and IT teams continue to struggle with. It’s evident that entrusting “anything that produces value” to define your cybersecurity strategy isn’t enough direction when teams are already experiencing extreme burnout.
How to identify cybersecurity assets
Assets are unique, which makes the identification and inventory process even more of a challenge for today’s security personnel. The NIST Specification for Asset Identification is a great place to get started, as it provides guidance for identification based on each supported asset type, including a person, organization, system, software, database, network, service, data, computing device, circuit, or website.
Using this framework, organizations define the fields or properties that help identify an asset.
NIST Asset Identifiers
- Literal identifiers are given using a pre-defined set of attributes that must be processed correctly, such as a MAC address to identify a network device.
- Synthetic identifiers involve internal databases and/ or processes, such as employee identification numbers. Though the number of synthetic identifiers varies according to each asset type, each one must also be properly processed.
- Relationship identifiers refer specifically to the types of relationships described by a controlled vocabulary and are also considered “core” to asset identification.
- Extension identifiers are optional, outlying pieces of information that can be used to identify an asset.
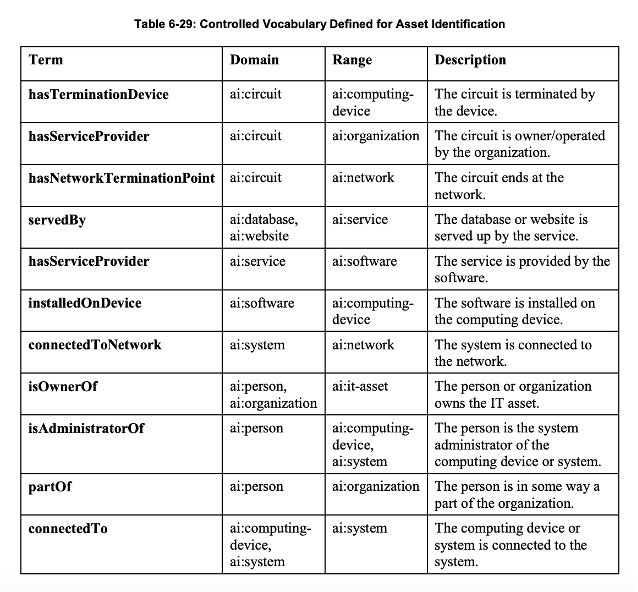
Although extension identifiers are not considered “core” in these specifications, it provides the opportunity for organizations to tailor their process so that it truly encompasses their entire cyber asset landscape.
Completing a cyber asset inventory
To begin on your asset inventory journey, the Cybersecurity & Infrastructure Security Agency (CISA) recommends first completing the following checklist:
| Input | Guidance |
|---|---|
| Prioritized list of services | A prioritized list that clearly identifies the highest valued services |
| Asset definitions | Assets are clearly defined for the organization so that the stakeholders responsible for identifying assets can consistently document them |
| An understanding and acknowledgement of an acceptable approach to asset management | Acknowledgement from management for the intended approach to asset management, including stakeholder expectations about acceptable risk tolerance for the identified critical assets and services |
| Externally imposed requirements for asset management | Regulatory requirements defining mandatory requirements for asset definition; also includes other needs such as service level agreement requirements |
| Risks | The list of categorized and prioritized risks |
| Assignment of responsibility for asset management | Job descriptions for roles that have responsibilities for asset management, for example, executive ownership, decisions, communication, testing and disruption risk management |
Source: CISA, 2016
It isn’t a mere coincidence that of the items listed above, ranking services in order of business criticality comes first. To help determine criticality, consider the following questions documented in CISA’s insider threat mitigation campaign for asset protection:
- If compromised, will it impact workforce or public safety?
- Was it identified as critical in a Business Impact Analysis?
- Is it vital to the organization’s primary mission?
- What is the risk tolerance?
- Will a compromise have a negative impact on the organizational brand or reputation?
- Will damage, compromise, or disruption result in an unacceptable financial loss?
This may seem impossible to properly execute at scale—especially as environments continue to change and new assets are constantly introduced.
However, organizations already have most of the tools and data in place to support fuel dynamic asset intelligence, they just need to connect the dots without having to rely on manual, error-prone asset management processes.
Ready to ditch the spreadsheets? See how Noetic helps teams overcome the challenge of data siloes to maintain a complete asset inventory.
