New CISA Directive 23-01 focuses on improving asset visibility & vulnerability detection
‘Continuous and comprehensive asset visibility’ key to effectively manage cybersecurity risk
CISA Directive 23-01 guides federal agencies to focus on asset discovery and vulnerability enumeration. Learn what security leaders can do now to prioritize visibility and vulnerability management.
The Cybersecurity and Infrastructure Security Agency (CISA) continues to drive higher standards in helping Federal agencies to manage cyber risk. This follows on from last year’s Binding Operational Directive (BOD) 22-01 which introduced the valuable Known Exploitable Vulnerabilities catalog and required Federal civilian agencies to identify and remediate these specific vulnerabilities within a certain timeframe.
This new BOD, 23-01 builds on that work and is intended to help civilian agencies to improve their operational visibility, a key building block of any successful cybersecurity program. The directive is focused on 2 critical initiatives:
- Asset Discovery – defined as an activity through which an organization identifies what network addressable IP-assets reside on their networks and identifies the associated IP addresses (hosts)
- Vulnerability Enumeration – This describes the identification and reporting of suspected vulnerabilities on assets. This is achieved through detecting host attributes, such as operating systems, applications etc. and matching them with data on known vulnerabilities.
CISA’s required outcomes for Asset and Vulnerability Visibility
CISA is offering to support agencies on their current baseline asset management capabilities and provide technical and program assistance and is not prescriptive in their technology recommendations. However, the Directive is specific about the desired outcomes that agencies will have to meet. These are:
- Maintain an up-to-date inventory of networked assets as defined in the scope of this directive;
- Identify software vulnerabilities, using privileged or client-based means where technically feasible;
- Track how often the agency enumerates its assets, what coverage of its assets it achieves, and how current its vulnerability signatures are; and
- Provide asset and vulnerability information to CISA’s Continuous Diagnostics and Mitigation (CDM) Federal Dashboard.
For all impacted Federal Civilian Executive Branch (FCEB) agencies, this means that by April 3, 2023, they will need to:
- Perform automated asset discovery at least every 7 days, including, at a minimum, the organization’s entire IPv4 space
- Be able to drive ‘on-demand’ asset discovery and vulnerability enumeration within 72 hours of a CISA request, and present the findings back to CISA within 7 days.
- Run an organization-wide vulnerability enumeration process every 14 days, including endpoints, networks devices and roaming devices, such as laptops. Vulnerability detection signatures should be no more than 24 hours old.
Additional guidance as to the specifics of this program are available in CISA’s implementation guidance, and there is the understanding that for some agencies, this process will be more complex.
A 2021 US Senate report on the state of cybersecurity in Federal agencies highlighted common asset and vulnerability management challenges and, while only Federal agencies are required to comply with this Directive, it provides a roadmap for other organizations on the potential direction of regulatory compliance, as noted by Erik Nost and Jess Burn at Forrester in their blog on CISA’s latest move.
How can Noetic help organizations with Asset Discovery and Vulnerability Enumeration?
Noetic’s approach to cyber asset attack surface management (CAASM) aligns very well with CISA’s new Directive. Our ability to continuously identify assets and map their cyber relationships in our graph database means that we understand how assets, vulnerabilities, networks and datasets are connected and can present this information to security teams in a way that clearly understandable and actionable.
Our perspective is that cyber asset management and vulnerability prioritization should be tighlty integrated processes, as you need to understand both asset criticality and likelihood of exposure, as well as vulnerability severity and exploitability, in order to run a successful cybersecurity program.
Noetic’s approach to Asset Discovery
The Noetic platform leverages existing security, IT management and DevOps tools through agentless API connectors to build a map of all assets across the organization – cloud and on-premises. The asset data is continuously updated, aggregated and correlated into our graph database to provide security teams with a 360-degree view of all assets, the cyber relationships between them and their current security posture.
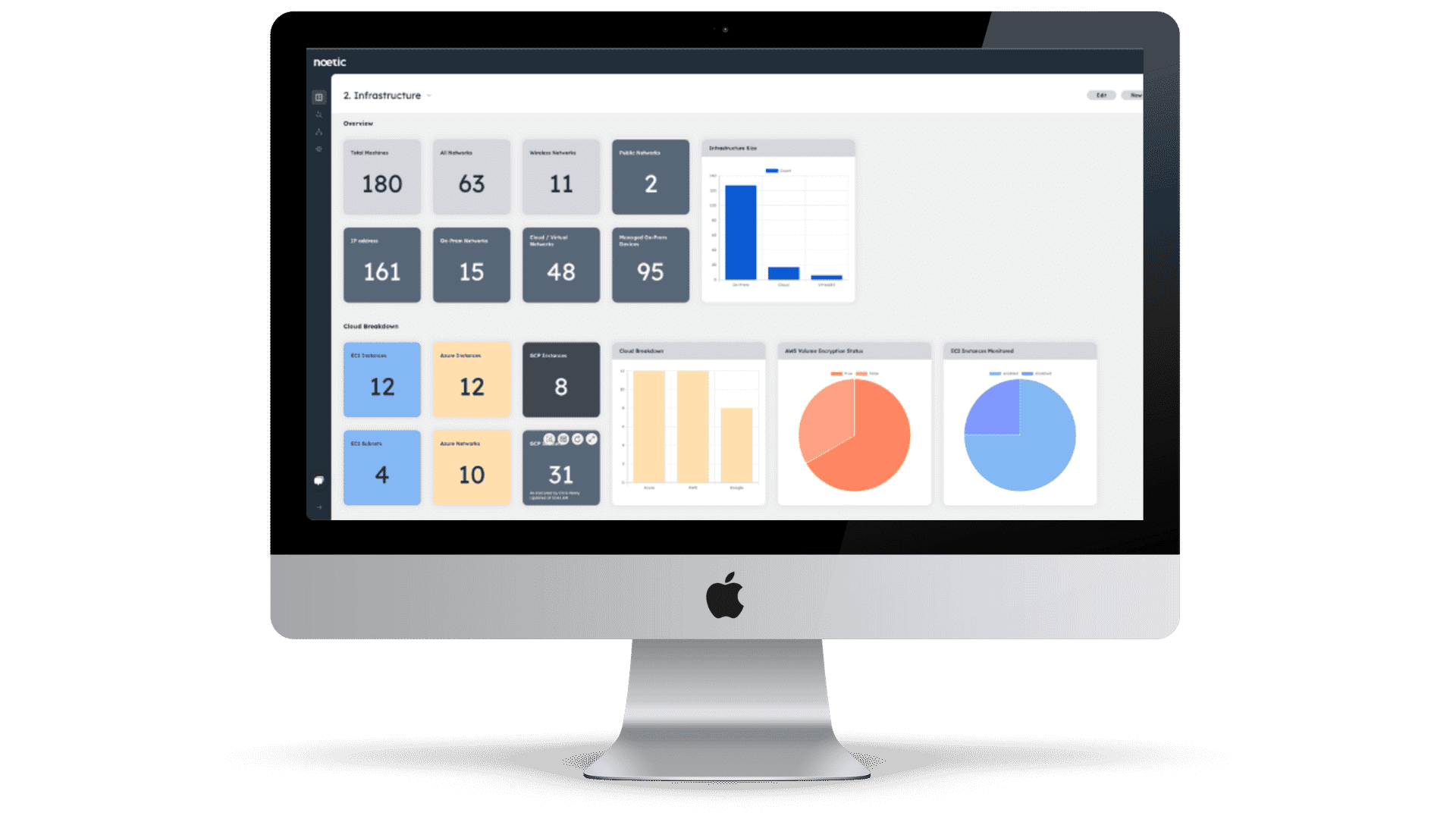
This ensures that security teams always have the latest understanding of their cyber asset landscape, attack surface and potential security gaps that need to be addressed. Automated action is also a key part of the Noetic solution, allowing teams to quickly trigger automated processes across their security infrastructure to address control drift.
Noetic’s approach to Vulnerability Enumeration
In the Noetic platform, vulnerabilities are mapped into the graph along with machines, networks, users and other relevant security assets and data. We ingest vulnerability data from a range of different tools, including EDR, network discovery and Vulnerability Assessment platforms. This correlated data is then enriched from external intelligence sources, such as NIST NVD, CIRCL CVE, First EPSS, the CISA Known Exploitability catalog and more.
What this gives us is a unique ability to put vulnerabilities in their necessary context. Security teams using Noetic can quickly identify and prioritize outstanding vulnerabilities based on a combination of criteria so they can focus remediation where it makes the most sense.
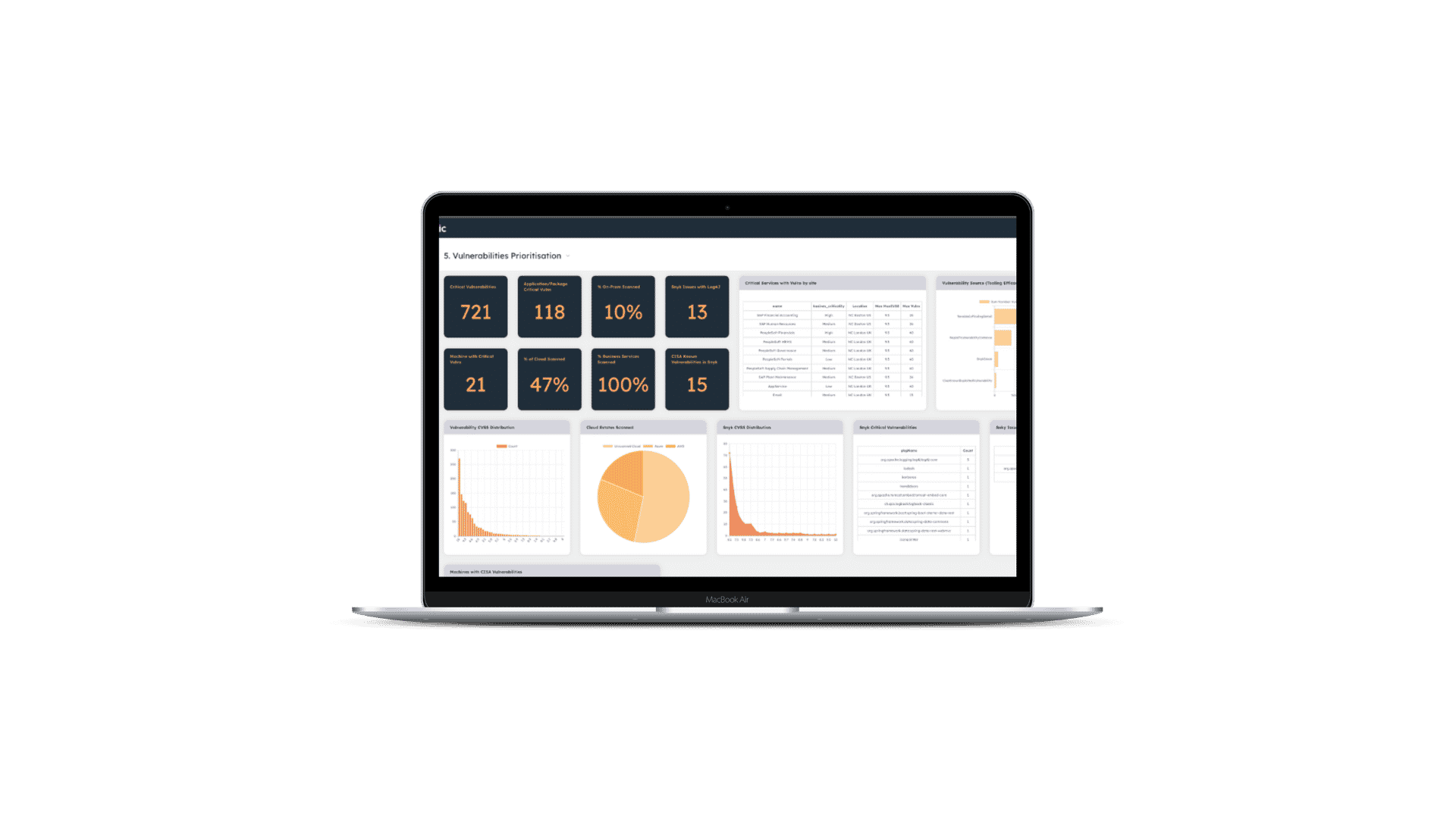
Security teams across Federal agencies and the commercial sector need to prioritize their workload, and by focusing on exploitable vulnerabilities that are impacting on business-critical applications or systems first, they can reduce their potential exposure and cyber risk.
To learn more about how Noetic can help meet CISA’s new requirements in BOD 23-01, you can register for our upcoming live demo, where we will cover off asset visibility and vulnerability prioritization use cases. Alternatively you can request a personalized demo of the Noetic platform here.
