Navigating Zero Trust in the Cloud: Challenges vs. Solutions
Zero Trust is rapidly transitioning from theory to practice, with 51% of enterprises having already implemented some capabilities. Federal government strategy has been a big driver, ever since a 2021 Executive Order mandated agencies “advance towards a Zero Trust Architecture.” However, implementing Zero Trust in cloud environments poses unique challenges, particularly in gaining visibility into distributed third-party systems.
Understanding Zero Trust Principles
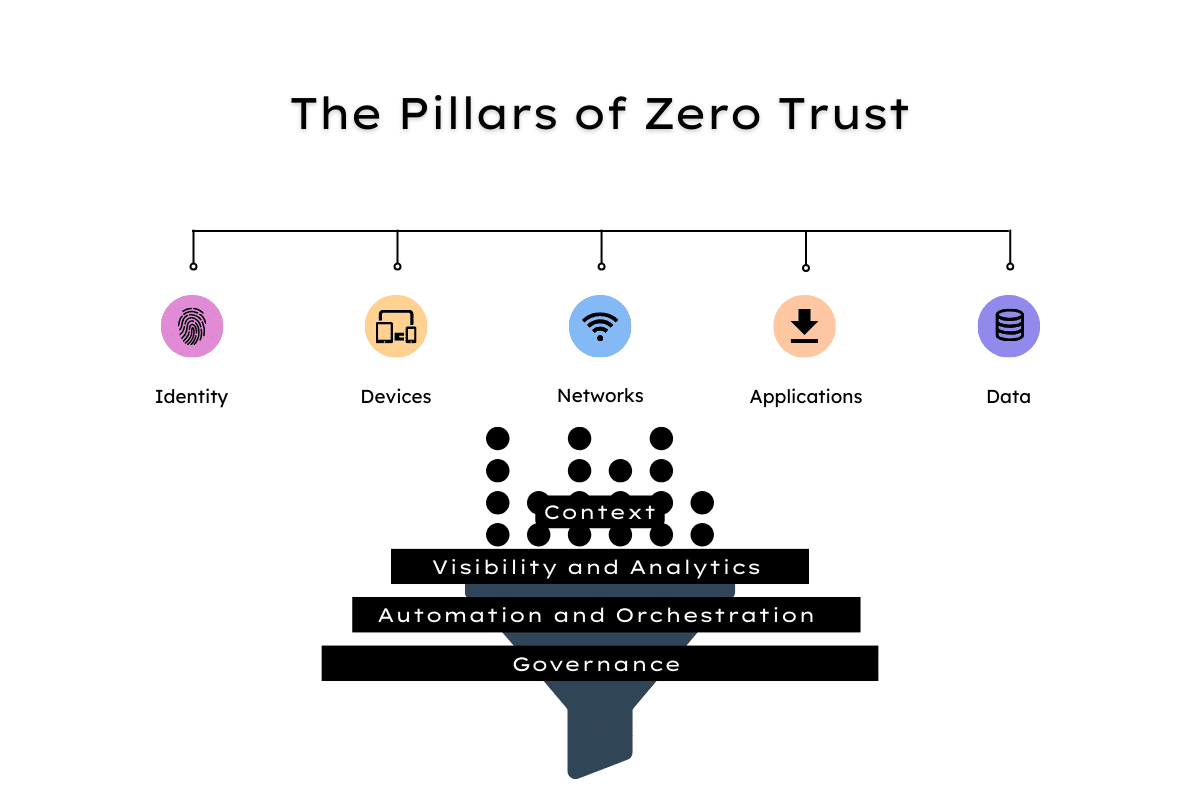
The concept of Zero Trust varies across organizations and security vendors, which tends to create confusion. A 2022 report found that over one-fifth of businesses were unsure how to implement a Zero Trust program. The Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model provides a practical definition, outlining five key pillars:
- Identity: Use of enterprise-wide identity to access applications, with phishing-resistant multi-factor authentication (MFA) protecting employees from sophisticated online attacks.
- Devices: An up-to-date inventory of every device in operation and authorized for official use, and the ability to detect and respond to incidents on those devices.
- Networks: Encryption of all DNS requests and HTTP traffic, segmentation of networks around applications, and encryption of email in transit.
- Applications: All applications should be treated as internet-connected, and routinely subject to rigorous vulnerability testing.
- Data: Data protection should make use of thorough data categorization. Cloud security services monitor access to sensitive data, and there is enterprise-wide logging and information sharing.
The Challenges of Implementing Zero Trust in the Cloud
As data, workloads, and infrastructure migrate to the cloud, there’s an obvious demand for Zero Trust to extend to these environments to mitigate cybersecurity and compliance risk. Some 87% of global enterprises have now embraced multi-cloud and 72% have a hybrid cloud strategy, according to one estimate. Yet, such plans can create challenges for implementing Zero Trust along the classic principles of “never trust always verify.” That demands visibility and control that many organizations simply don’t have in the cloud.
Key Challenges in Implementing Zero Trust in the Cloud:
- Dynamic Cloud Attack Surface: Non-technical users frequently initiate the creation of new assets for ad hoc projects without central IT approval, perpetually altering the cloud attack surface. This dynamic nature introduces uncertainty and heightens the need for constant vigilance.
- Ephemeral Nature of VMs and Containers: Virtual Machines (VMs) and containers contribute to a dynamic and ephemeral environment where assets are generated at scale, disappearing as swiftly as they materialize. This fluid landscape challenges traditional security approaches and demands adaptability.
- Complexity of Multi- and Hybrid Cloud Strategies: Multi- and hybrid cloud strategies introduce a myriad of challenges, encompassing diverse technology platforms, management consoles, and security tools. The varied approaches to securing and managing access—VPN, software-defined perimeter, inbound proxy/virtualized firewall, or a cloud access security broker (CASB)—add complexity, making consistent policy enforcement a challenging endeavor.
- Skills and Resource Shortages: The rapid pace of technological change often outpaces the in-house skills and resources of organizations. Cloud vendors introduce features faster than IT teams can adapt, leading to misconfigurations. IBM identified cloud misconfiguration as an initial access vector in 11% of data breaches last year, underscoring the critical importance of addressing skills and resource gaps.
In navigating these challenges, organizations must strategize, adapt, and invest in solutions that align with the dynamic nature of cloud environments. Overcoming these hurdles is not just a technological feat but a strategic imperative for ensuring the efficacy of Zero Trust implementations in the ever-evolving cloud landscape.
Mitigating Zero Trust Cloud Risk Amidst Constant Change
Zero Trust is predicated on the ability to understand who (or what) is trying to access what, whether they’re authorized to do so, and if there are any vulnerabilities or misconfigurations in assets that could introduce security risk. That demands continuous monitoring across the distributed cloud environment, coupled with proactive attack surface patrolling for swift containment of threats and exposures.
Charting the Course to Zero Trust Cloud Security with CAASM
In this regard, “total context” is key. That is, continuous 360-degree visibility across all cloud assets, users and networks and the relationships between those constituent parts. The Noetic platform continuously harvests data via APIs from key cloud players including AWS, Google, Azure and Kubernetes to build an accurate map of the current cloud estate.
It then cross-checks with data extracted from other systems offering identity and access management (IAM), vulnerability management, CMDB, existing cloud security solutions including Cloud Workload Protection Platforms (CWPP) and Cloud Security Posture Management (CSPM) tools, business applications and much more. This provides the critical context-rich visibility which is the foundation for building automated policies in line with Zero Trust principles.
With the Noetic platform, organizations can:
- Identify potentially high-risk exposed assets and determine the “blast radius” of attacks.
- Deploy adaptive access control policies by comparing the attack surface against IAM data.
- Rapidly remediate misconfigurations and vulnerabilities.
The pathway to Zero Trust in cloud security is not a linear progression but a dynamic journey that demands adaptability and foresight. By unravelling complexity, navigating multi-cloud dynamics, embracing technological evolution, overcoming resource constraints, and leveraging innovative solutions like CAASM, organizations can chart a course towards a robust and secure Zero Trust cloud environment.
Watch our interview with CEO and Co-Founder of Cloud Security Alliance Jim Reavis to discover more ways to address the evolving dynamics of cloud security.
Dive deeper into the dynamic realm of cloud security. Access the full Q&A with Advisory Board Member Jim Reavis to gain exclusive insights on:
- The impact of cloud migration
- Trends shaping the cloud landscape
- More challenges and solutions for navigating multi-cloud security
