Applying Maslow’s Hierarchy of Needs to Exposure Management
When I think about the broad security problems that Noetic is working to solve, they are typically associated with organizational cyber resilience. Security teams are not looking at Cyber Asset Attack Surface Management (CAASM) tools such as the Noetic platform to help firefight security incidents, but rather to focus on improving their overall security posture and hygiene.
Defining the Exposure Management Challenge
This can include identifying potentially high-risk exposures, such as exploitable vulnerabilities or misconfigured cloud systems that can provide attackers with a way of bypassing defenses. Or it could mean reducing the attack surface by eliminating obsolete and unmanaged machines and ensuring that privileged users have the right level of multi-factor authentication (MFA). One of the challenges with a wide domain such as exposure management is that it covers so many potential use cases.
Applying Maslow’s Hierarchy of Needs
A useful way of articulating this challenge that I have been discussing internally is to use the concept of Maslow’s Hierarchy of Needs.
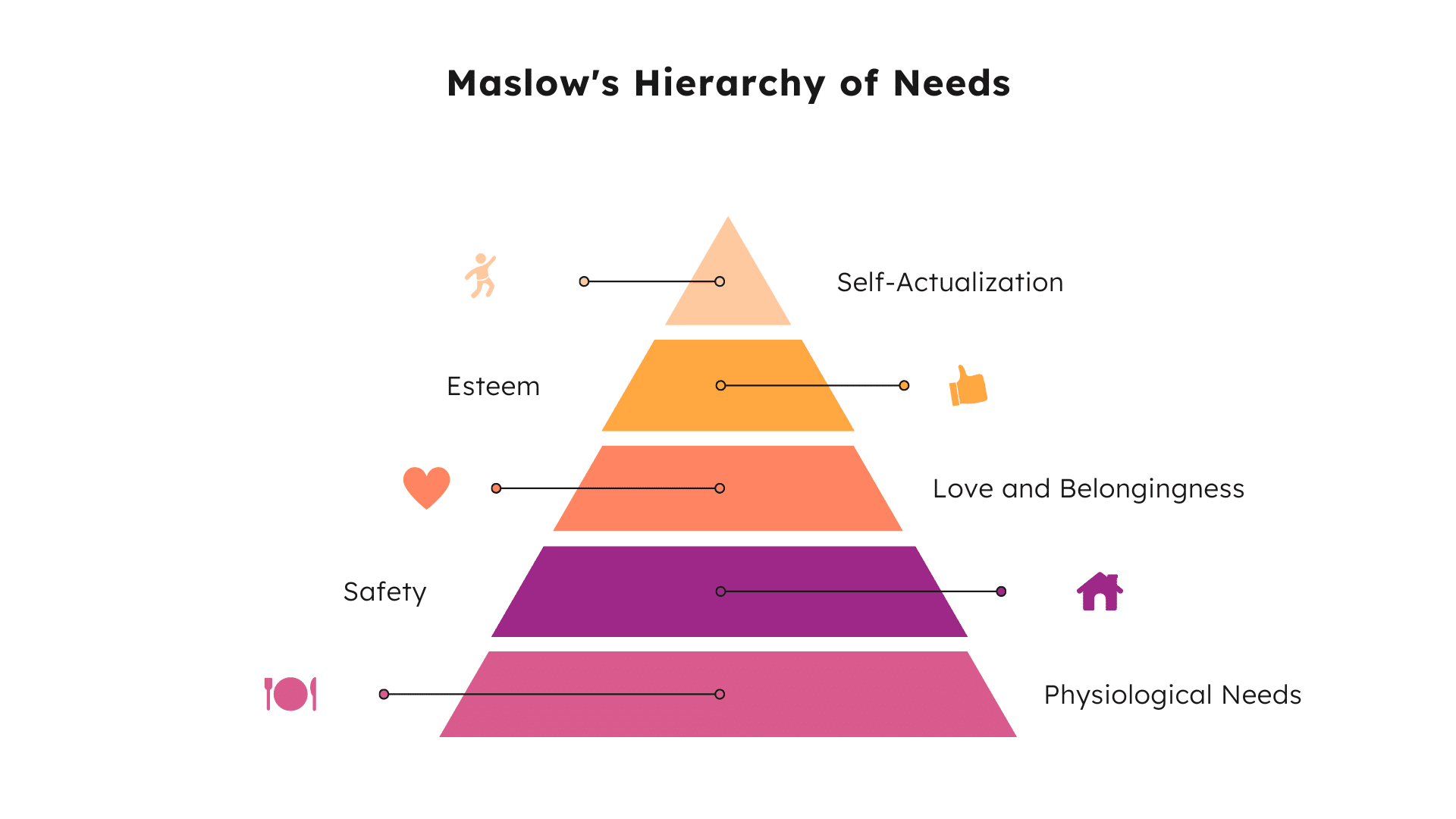
Maslow’s Hierarchy of Needs is a model developed in 1943 by American psychologist Abraham Maslow. Often visualized as a pyramid, the hierarchy of humans needs emphasizes that basic needs (food and water) must come before higher-level needs (belonging, self-actualization).
The core of the idea is that human motivation and well-being is dependent on fulfilling certain needs, Maslow defined these into five categories:
- Physiological (food, water, shelter, sleep, etc.)
- Safety (health, personal & financial security)
- Love & Belonging (Family, friendship, intimacy, trust, etc.)
- Esteem (self-worth, dignity, independence, peer respect, acknowledgement)
- Self-actualization (a realistic perception of reality, an appreciation for life, creativity)
The concept of Maslow’s hierarchy of needs has been adopted in many other domains, particularly in education and healthcare. It has also been adapted previously for cybersecurity use cases, notably by Microsoft’s Trustworthy Computing Group in this 2013 paper, focusing on wider cybersecurity policy and resilience issues.
The Hierarchy of Exposure Management Needs
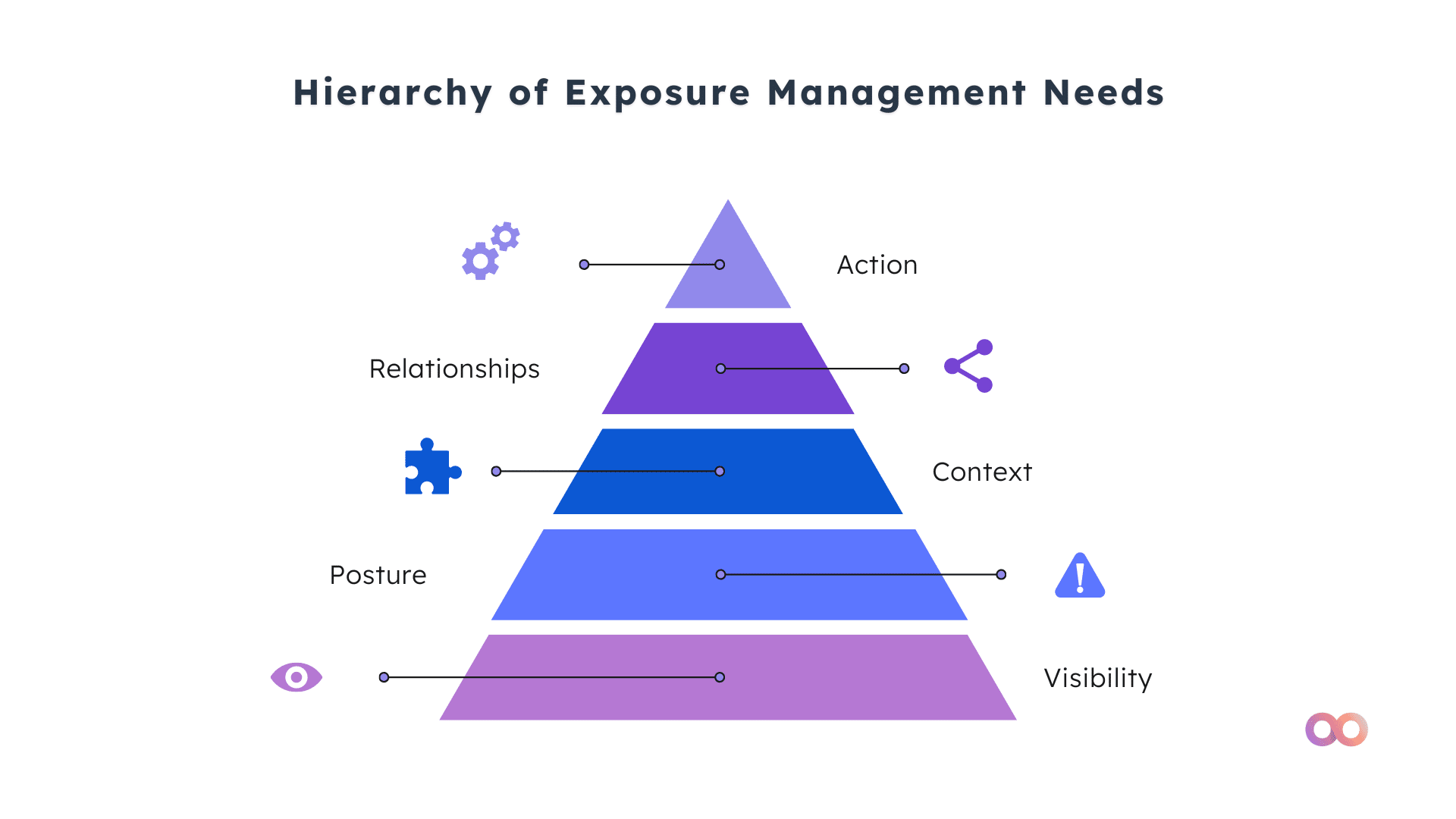
I wanted to look at how we could relate Maslow’s model to exposure and attack surface management challenges and outline the hierarchy of needs for navigating the dynamic cyber threat landscape. Starting with the most basic, foundational elements and working upwards, I have put together a framework for the hierarchy of needs as it applies to threat and exposure management.
- Visibility: Visibility is the foundational element of an exposure management program. You need to understand what you have to protect it. Cyber asset visibility is a significant challenge for security leaders as they have to deal with complex, constantly changing environments. Technology sprawl means that to achieve near-complete visibility, we need insights into public and private cloud, SaaS applications, legacy on-premises environments as well as third-party supply chain.
- Posture: Once we understand what we have, we need to know what its current security posture, or state, is. Good cyber asset management allows us to quickly identify common security coverage gaps: Do all physical and virtual machines have an updated EDR agent deployed? Do all admin accounts have multifactor (MFA) enabled? Are our cloud storage volumes encrypted? The technical posture of assets can degrade over time, so it’s important that we are continuously looking for changes here.
- Context: Context is what allows us to prioritize our workload. It is not possible to patch all vulnerabilities, and not all exposures are not created equal. By mapping assets with other information sources, such as external vulnerability and threat intelligence, we gain vital insights into different levels of exploitability and exposure that enable us to focus on correcting security posture issues that will have the most impact to the business. For example, we may wish to prioritize patching vulnerabilities that a reputable third-party organization like FIRST or CISA has identified as being exploited in the wild, particularly if those assets are internet-facing.
- Relationships: This is closely related to context, but there are differences. No piece of security data exists in a vacuum; for example, machines are on networks that relate to specific business locations or services. By understanding the relationships between assets, we can not only improve the context we have into business criticality, but we can also communicate effectively with the business. Running an effective exposure management program is a cross-functional exercise, so we need to align to our colleagues in IT and the business to be successful.
- Action: Finally, at the top of our Exposure Management pyramid, is action. We’re not just focused on finding security coverage gaps, but we need to fix them too. Workflow and automation needs to be a key part of an exposure management initiative, as part of the coordination with asset and business application owners.
Once an exposure is identified, then it can either be automatically remediated if it is predictable and clearly understood (a missing security agent for example), or a notification process can be initiated. A key tenet of an exposure management program is that it should be continuous in nature, so as new assets and exposures are uncovered, an enrichment, notification and remediation process should be triggered.
Understanding and managing your organizational security posture is fundamentally a data problem. We need to consume and interpret security insights from a wide range of different tools and systems to identify potential exposures and coverage gaps. Managing security data at this scale creates its own challenges, so a model like Maslow’s hierarchy of needs for security data is useful to help us understand where to start, and how to prioritize the development of our exposure management programs.
Discover the essential components of a continuous approach to threat and exposure management based on Gartner® research in our exclusive eBook: How to Implement Continuous Threat Exposure Management (CTEM) with Noetic.