SentinelOne Singularity Connector: Support for Application Risk, Ranger and more
Noetic’s partnership with SentinelOne is an important extension of our market-leading cyber asset attack surface management (CAASM) platform. The Noetic Connector for SentinelOne Singularity was one of the first integrations we developed and is widely deployed with our customers. We were also delighted to be one of the first cybersecurity vendors that SentinelOne invested in through the S Ventures fund which was launched last year.
The Noetic platform combines the high-fidelity endpoint, cloud, network and application risk telemetry and vulnerability data we get from SentinelOne with security data from other sources, such as Identity & Access Management (IAM), Configuration Management Databases (CMDBs), Cloud platforms and more. In turn, our customers receive 360-degree visibility into all cyber assets, their current security posture and critical business and exposure context that helps their security teams to identify high-risk coverage gaps and drive prioritization.
Updates to the Noetic–SentinelOne Singularity Connector
As we continue to drive innovation with the Noetic platform, it’s important that we also build on all the key capabilities of our strategic partners to deliver the insights that security teams need. So with that, I’m excited to share information on our updated SentinelOne Singularity Connector.
The first version of the bi-directional connector focused on getting information and driving action primarily from the core Singularity Platform, particularly around endpoint coverage gaps. We are now taking this further and extending it to support important new use cases:
1. Enrich and prioritize vulnerability findings
We have added support for SentinelOne’s new Application Risk capability – this leverages the installed SentinelOne agent to scan the endpoint for third-party applications, listing them in the application inventory. SentinelOne also enriches this information for ‘application risk’, mapping the application inventory with vulnerability data from NIST NVD many times a day and associating it with the relevant applications and endpoints.
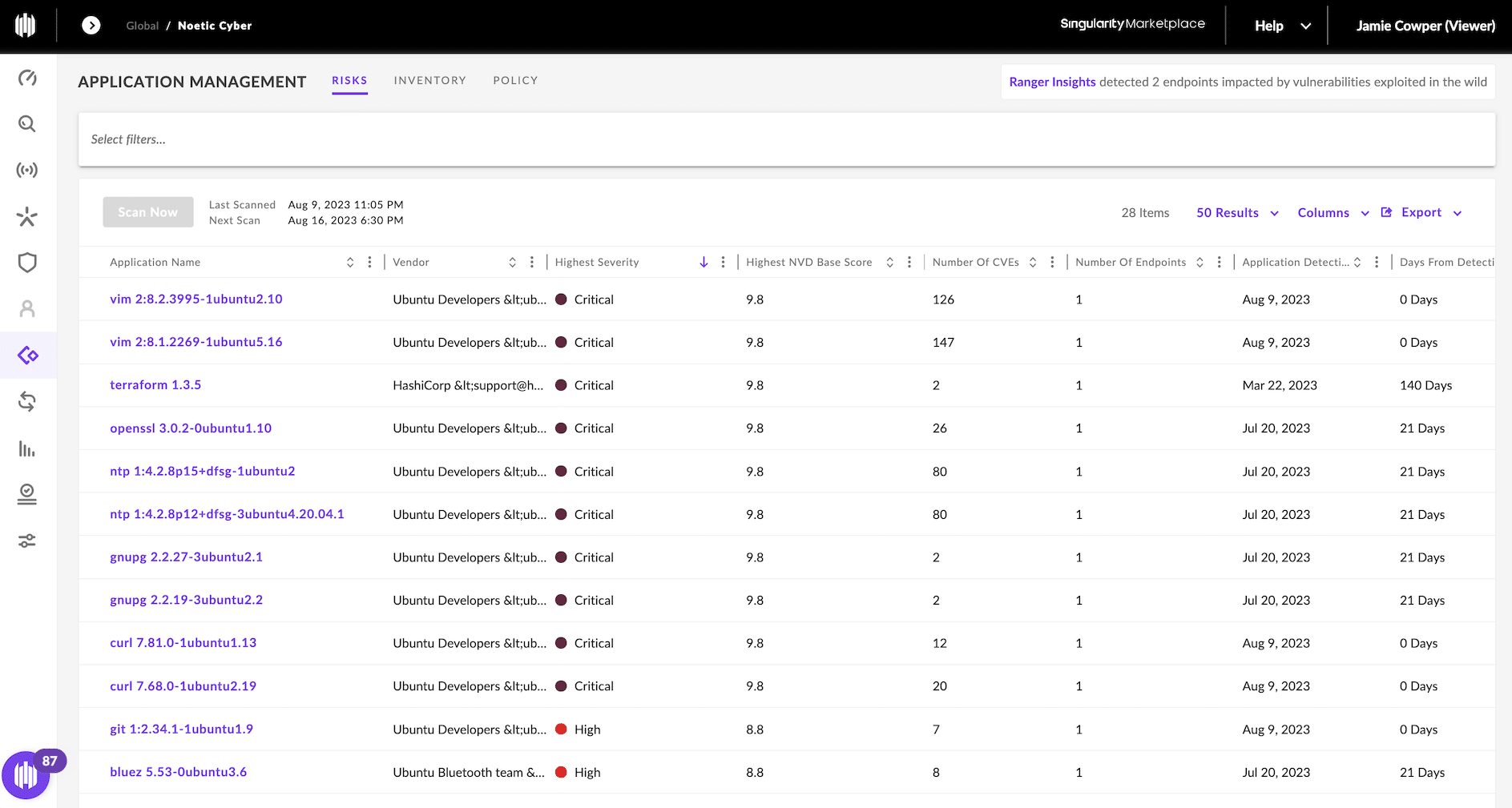
Noetic can now bring this application risk data into the Noetic platform, adding the vulnerability data and findings into our data model. This allows us to correlate it with additional vulnerability data, potentially from traditional vulnerability scanning tools, and enrich it from vulnerability intelligence sources, including CISA’s Known Exploitable Vulnerability (KEV) Catalog, FIRST Exploit Prediction Scoring Systems (EPSS), Microsoft Security Resource Center and more, helping the security team to prioritize vulnerabilities based on exploitability as well as severity.
We can also correlate the SentinelOne vulnerability data with the business data we hold, providing essential context on the criticality of the affected machines, such as what tier-1 business applications they support, or which users or critical business resources might be impacted.
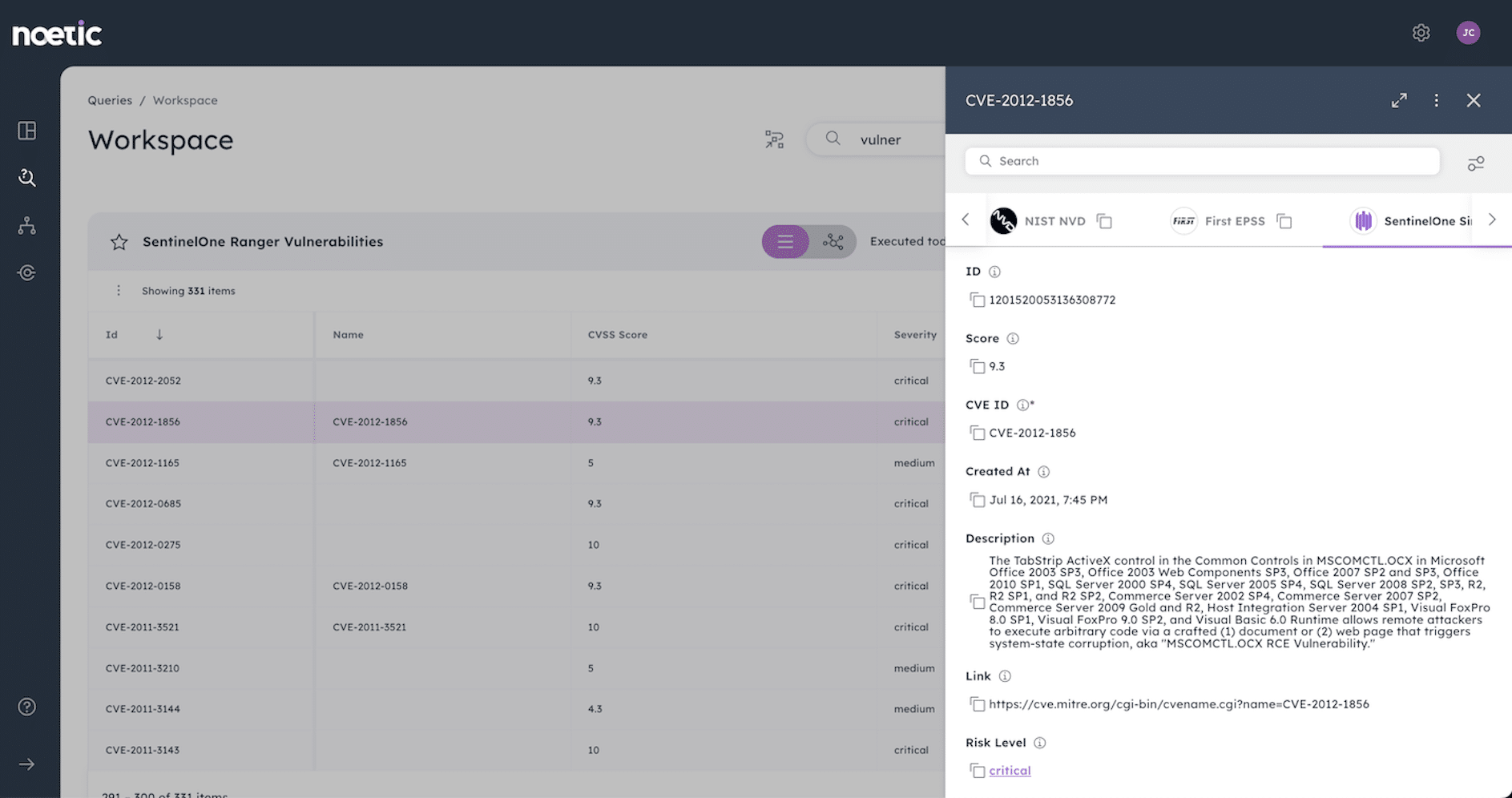
2. New support for network discovery with Singularity® Ranger
Ranger is an important addition to deployed agents in SentinelOne. It allows security analysts to trigger policy-based network scans to fingerprint known and unknown devices, discovering the “unknown unknowns”. This provides them with more granular network visibility and control, as unmanaged machines can be identified, monitored and even blocked if appropriate.
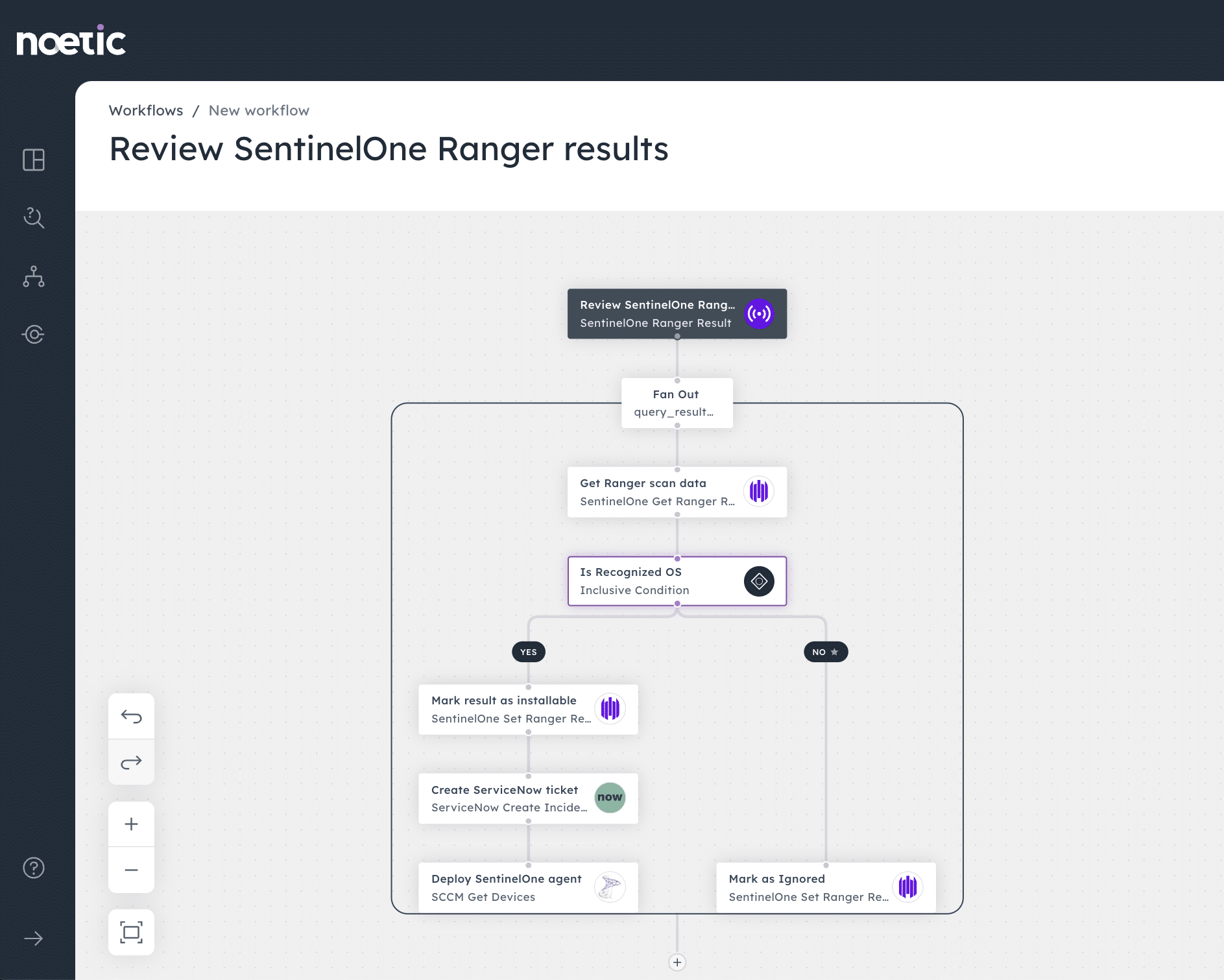
Noetic’s new integration with Singularity Ranger enables us to ingest the results of Ranger scans into the Noetic platform, providing important context into Ranger-discovered devices such as whether they are on a restricted network range, have access to sensitive datasets or which services they support. This considerably reduces the analyst workload by simplifying the review process.
In addition, Noetic can automatically update the Ranger Device Review status based on our findings, for example, that a machine is ‘under analysis’, publishing this data back to the Singularity Management console through our bi-directional connector.
3. Extended support for Cloud and Container use cases
The new release of the Noetic connector has also added support for Singularity Cloud Workload Protection. By aggregating SentinelOne’s data with information we have from AWS, Azure and Google Cloud, we can find security coverage gaps across containers and Kubernetes clusters, notifying the security and cloud operations teams to drive remediation.
With our recently announced simplified enterprise cloud model, we can present this coverage gap data to different business units, groups or even organizations in a way that is relevant for them and simple and easy to consume.
This new release is a significant upgrade to our SentinelOne integration and the initial feedback from our joint customers has been very positive. But we have a lot more to come. I look forward to updating you soon on more innovation to help support Incident Response (IR) investigations and Threat Hunting in SentinelOne, as well as greater depth and breadth in our automation and cloud security use cases.
If you’re a current SentinelOne customer looking to find out more about the joint integration, I would recommend reading our joint eBook, or you can schedule a demo of the platform here.
