How to Overcome the Cyber Asset Visibility Challenge
When it comes to cybersecurity, cyber asset visibility is key. Yet, the fundamentals of cyber asset management seem to have taken the back seat to larger, more complex initiatives amidst this new age of digital transformation. As a result, cyber asset attack surface management (CAASM) has emerged to help security and risk teams remaster the fundamentals.
The Cyber Asset Visibility Challenge
Shadow IT, misconfigurations and unknown exposures to the internet were the root cause of nearly 40% of successful cyberattacks in 2019. While our goal as cybersecurity professionals is to keep history from repeating itself, 75% of organizations expect to experience a cyber attack originating from an unknown, unmanaged, or poorly managed company asset.
Despite asset visibility being the foundation for security and risk, teams face significant challenges when it comes to maintaining an accurate view of their attack surface. It’s especially intimidating for those companies that have hundreds of thousands of continuously changing assets.
3 Cyber Asset Management Tactics to Improve Attack Surface Visibility
Regardless of how large your attack surface may be, you can break down the entire cyber asset management process into the following simple steps:
- Automate your cyber asset inventory process,
- Consolidate your asset inventory tech stack,
- Assess cyber risk according to potential business impact.
Automate your cyber asset inventory process.
Most challenges surrounding IT asset inventory result from conflicting data sources and the laborious, manual process currently required to achieve a point-in-time cyber asset inventory. On average, a full security asset inventory requires 10 inventory systems and nearly 90 person-hours to collect, process and analyze the necessary information.
Given that today’s digital landscapes change by the second, these manual inventories can become outdated before they’re even completed. An outdated asset inventory is a dangerous one, so it’s important that your records keep up with the pace of change.
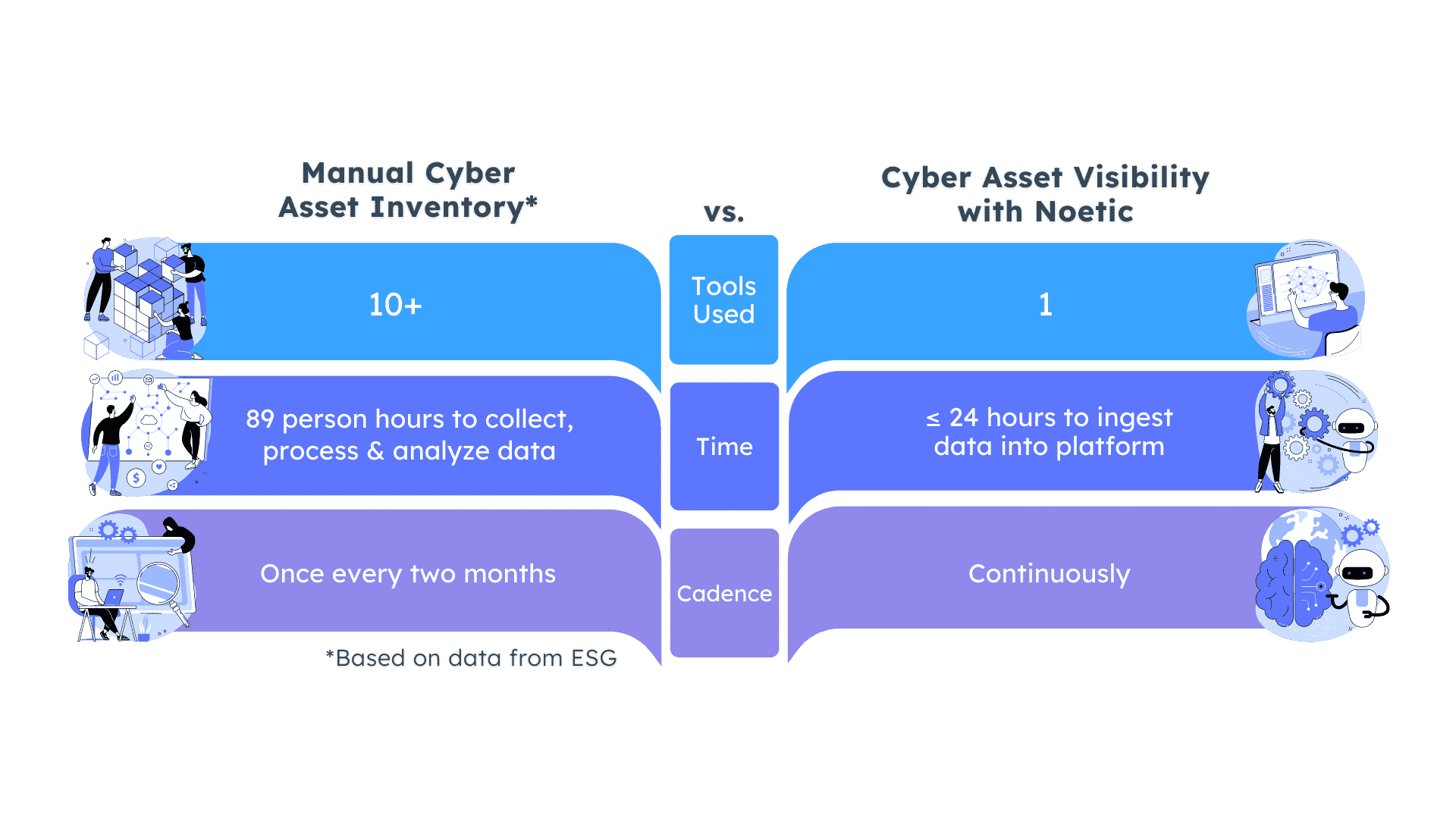
CAASM solutions, however, leverage your existing security, DevOps and IT management tools to automatically identify and track digital assets as they’re added, removed, or changing within the environment. This helps to ensure that the inventory is always current and reflects assets’ current security posture.
If your asset inventory management process only considers the external attack surface alone, then it’s only piecing together a part of the puzzle. Systems, devices, networks, and cloud assets certainly require continuous visibility to keep your organization secure. However, users, security gaps, policies and controls, and other elements are just as important to consider in your asset management program.
Consolidate your asset inventory tech stack.
Although organizations may have internal logs containing related information, conflicting data sources from dozens of asset inventory tools also impacts the accuracy and efficiency of attack surface visibility efforts.
To name a few, the most common data sources used in today’s IT asset inventory process include:
- IT asset management systems
- Endpoint security tools
- Cloud security posture management
- Network scanning
- Vulnerability scanners
- Endpoint management systems
And that’s just to capture the traditional IT estate. With CAASM, teams maintain a single source of truth by automatically leveraging information from any data source via API integrations. CAASM solutions can connect to sources such as CMDB tools, internal network directories, and more to ensure there are no blind spots within your cyber asset management program.
Assess cyber risk accordingly to potential business impact.
It’s impossible to eliminate every cyber risk. That said, it’s crucial to understand what your attack surface looks like through the lens of whom you’re protecting it from: the adversary.
As John Lambert once said: “Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win.”
A sophisticated CAASM solution maps your attack surface not only according to device design and systems management, but also the users, behaviors and relationships that influence it. In turn, it automatically shared risk-based insights enabling teams to understand all assets–physical, virtual, or cloud– from a threat actor’s perspective.
Cyber Asset Visibility: The Core of Your Cybersecurity Strategy
For most organizations, this is only the beginning when it comes to rapid attack surface expansion. New technologies, applications, and third-party relationships will continue to multiply while threats themselves grow more sophisticated. To effectively navigate the growing threat landscape, organizations must revisit the basics.
With CAASM, teams can achieve full visibility of their attack surface, ensure that view is continuously updated, and understand their cyber risk landscape according to how their organization defines it… all without draining their resources.
Want to explore more benefits of becoming an early adopter of CAASM? Download our eBook ‘Making the Case for CAASM’ for exclusive insights from Brad LaPorte, advisor and former Gartner analyst.
Download the eBook

