Using continuous, contextual insight to improve your vulnerability management program
Cybersecurity Asset Management Use Case #2: Vulnerability Prioritization
You can’t protect what you can’t see. It’s a simple concept, but one that gets to the heart of why cybersecurity asset management should be a foundational best practice to any security strategy. Asset management is even mentioned in the guidance from CISA as a key enabler of Zero Trust maturity.
Yet, getting there isn’t easy. Modern IT environments are in constant flux. Existing vulnerability management tools, whilst valuable in their specific domain, provide neither the coverage nor context that IT leaders need to mitigate risk effectively, and on a continuous basis.
Organizations need a more effective way to have full visibility of their attack surface in order to manage it. That means a platform which can provide a comprehensive picture of assets and vulnerabilities, the intelligence to understand where risk is greatest, and automation to drive rapid remediation. This is the value of Noetic.
A losing battle?
If software is eating the world, vulnerabilities are devouring software. The number of publicly disclosed flaws has exploded over recent years, thanks to the proliferation of new solutions and concerted efforts from the security research community to tackle rampant threat activity.
The number of common vulnerabilities and exposures (CVEs) published to the NIST National Vulnerability Database (NVD) continues to break records. It featured a total of 18,103 in 2021—which amounts to 50 new CVEs every single day of the year. To put this in context: there were more high and critical severity vulnerabilities published in 2020 than the total number of all CVEs recorded in 2010. More concerning still is the growth of vulnerabilities which require no user interaction to exploit—they represented 68% of all CVEs recorded in 2020, according to one analysis.
In the meantime, exploits targeted at unpatched bugs continue to have major consequences. They are a top attack vector for ransomware, and have in the past been responsible for some of the biggest breaches on record—including the 2017 compromise of Equifax, which exposed over 140 million people.
Context is necessary in any cyber vulnerability management program
Faced with the sheer volume of new vulnerabilities appearing every day, and the growing business risk associated with a potentially successful exploitation, organizations are turning to automated vulnerability management tools. These are a step in the right direction. They scan a customer environment and map any discovered vulnerabilities to a known CVE list, prioritizing according to severity. But the value they offer is limited.
First, most tools are great at providing results, but only for the parts of your IT environment they know where to scan. Like endpoint detection tools, there’s often a coverage gap. If a cloud instance is created by a team outside of security policy, for example, a scanner wouldn’t check that asset to see if it’s patched.
Second, many of these tools don’t and can’t provide the context of a bug beyond its common vulnerability scoring system (CVSS) score. This leaves organizations with limited means to prioritize their vulnerabilities. A high severity vulnerability on an internet-facing web server may need to take precedence over a critical flaw on a development server, for example. IT teams need more intelligence to be able to support risk-based approaches to security asset and vulnerability management. Otherwise, they’ll waste time, money, and effort in their patching programs, and may even unwittingly leave the organization exposed.
With the growth of vulnerabilities discussed above, it is simply not possible for any business to patch all vulnerabilities; this also becomes a source of conflict between the security and IT teams as it is commonly a shared responsibility. It has become critical to prioritize the vulnerability and patch management workload based on business risk, both to reduce the attack surface but also to reach an achievable goal.
A new approach with Noetic
Noetic offers a different approach: a powerful answer to the challenges of both coverage and context outlined above. We do this in three key ways:
- To provide a comprehensive view of all assets and entities in the organization, we integrate with existing IT and security tools such as public clouds, vulnerability scanners, configuration management databases (CMDB), endpoint detection and response (EDR) tools and other third-party systems.
Using agent-less, API-based connectors, we can build a multi-dimensional map of all assets in the business and the cyber relationship between them in a graph database. This allows security to identify gaps in the current vulnerability scanning regime. - We can mine the data model built using the critical insights provided by these tools for any new assets, any recently disappeared assets, and the relationships between assets. From this, we build temporal graphs which help to define how attackers might move between machines, networks, and applications to discover and exploit vulnerabilities.
It’s effectively the same approach the bad guys use to find weaknesses in targeted environments—we’re simply turning things around to provide an advantage for the defenders. This gives us the crucial context and intelligence to predict which assets and vulnerabilities need patching first. - Finally, by mapping business context with technical data, we can help to prioritize vulnerabilities based on the risk to the business. If we know that an exploitable vulnerability is present on a machine which has access to personal data or is part of a share-price affecting application, then that drives an urgent need to remediate.
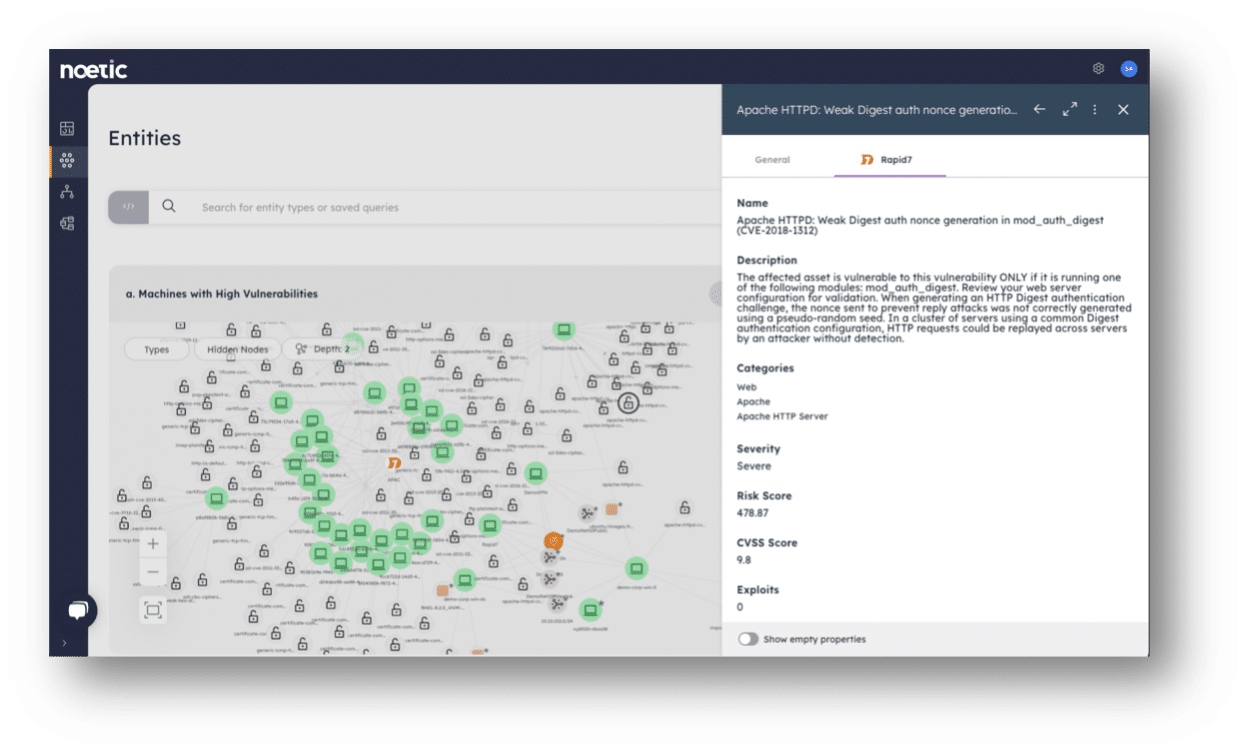
Automating successful outcomes
Once we’ve identified a vulnerability on an asset that requires attention, our powerful automation workflow capabilities can streamline and simplify remediation. This is very customizable and can map to the business’s current patch management process, and example workflow might be:
- Trigger an additional vulnerability scan in case the issue has already been fixed.
- Automatically email the asset owner and notify them of the need to patch the affected system, identified by information extracted from the CMDB or Active Directory. This may be appropriate for a certain level of CVE severity.
- However, if the vulnerability is deemed too high risk, we can instruct existing security tools to isolate the asset from the network and push out a patch via an existing patch management tool like BigFix or Microsoft SCCM. Equally this could be raised as a ticket in a ticketing system such as JIRA or ServiceNow.
- Trigger a rescan to confirm that the problem has been resolved.
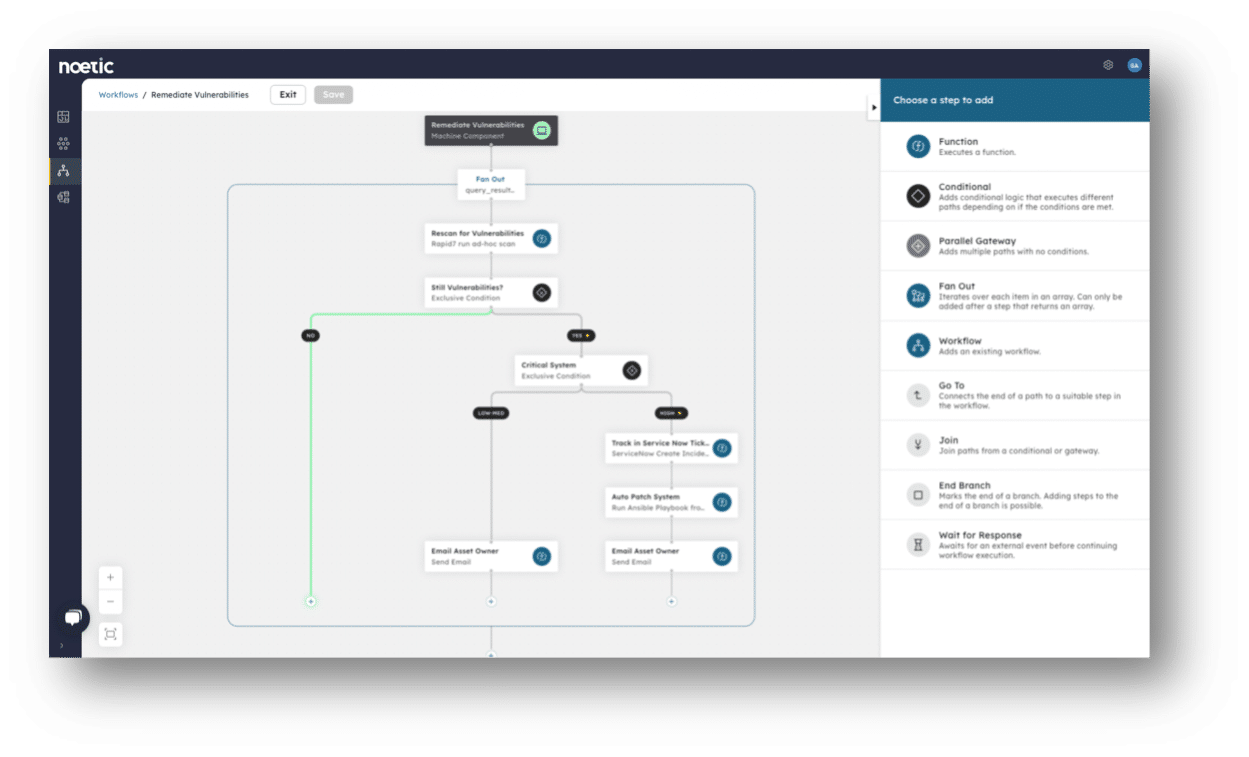
The goal is that these processes can be working away in the background with minimal IT involvement. We are simply returning the affected asset to its desired state, in line with a pre-determined security policy. That’s the way to deliver best practice cybersecurity asset management that maximizes prior investments in security tooling whilst minimizing corporate risk exposure.
To find out more about how Noetic can add value to existing vulnerability and patch management programs, download our exclusive eBook: Making the Case for CAASM.
Our next blog in the cybersecurity asset management use case series looks at common cloud and container security challenges. Read now.

