Zero Trust Starts with Asset Visibility
Last year in the UK, around two-thirds of medium and large-sized organizations admitted suffering a serious breach or cyber-incident. In the US, 2021 saw breach volumes surge 68% year-on-year to reach a record high. Against this backdrop, security teams are increasingly looking for more effective strategies to mitigate cyber risk.
Enter: Zero Trust. It may have been over a decade in the making, but this approach to cyber risk management received a major PR boost when the White House recently mandated its adoption across federal government.
Yet, Zero Trust is not the simple undertaking some vendors may have you believe. It’s often primarily associated with identity and access management (IAM), but this is only one piece of the puzzle. To build a solid Zero Trust strategy, you must go back to basics and start with secure foundations. That means gaining visibility into all IT assets, to ensure they are adequately hardened and aligned with policy.
Why Zero Trust, and why now?
Zero Trust was devised for a world in which the perimeter-based security model is no longer relevant. That’s the world we live in today thanks to pervasive hybrid working and ubiquitous cloud infrastructure. The approach posits that breaches are inevitable today. But they can be better prevented in the first instance and their impact can be greatly reduced, by adopting a mantra of “never trust, always verify.”
In a recent report, Gartner defines Zero Trust as ‘a security paradigm that replaces implicit trust with continuously assessed explicit risk and trust levels based on identity and context supported by security infrastructure that adapts to risk-optimize the organization’s security posture’. A critical point here is the importance of ‘context’ in driving decision making. A principle of Zero Trust is that security teams need to continuously monitor everything to detect anomalies, but to do that, they need to understand everything they have and why it matters.
The importance of Cybersecurity Asset Visibility & Management
The value of Noetic as a foundational part of a Zero Trust strategy
Guidance from NIST on ‘Migrating to a Zero Trust Architecture’ states that it ‘requires an organization to have a detailed knowledge of assets’ and that ‘Incomplete knowledge will most often lead to a business process failure…’, this is precisely how Noetic can provide value.
Noetic builds a comprehensive map of all assets in the organization, their current cybersecurity posture and the relationships they have with other assets. This full stack visibility provides the foundation necessary for implementing a Zero Trust architecture. Using standardized APIS, we can build on insights from existing vulnerability scanners, CMDBs, EDR tools, cloud management platforms, and business applications to provide comprehensive and continuous visibility.
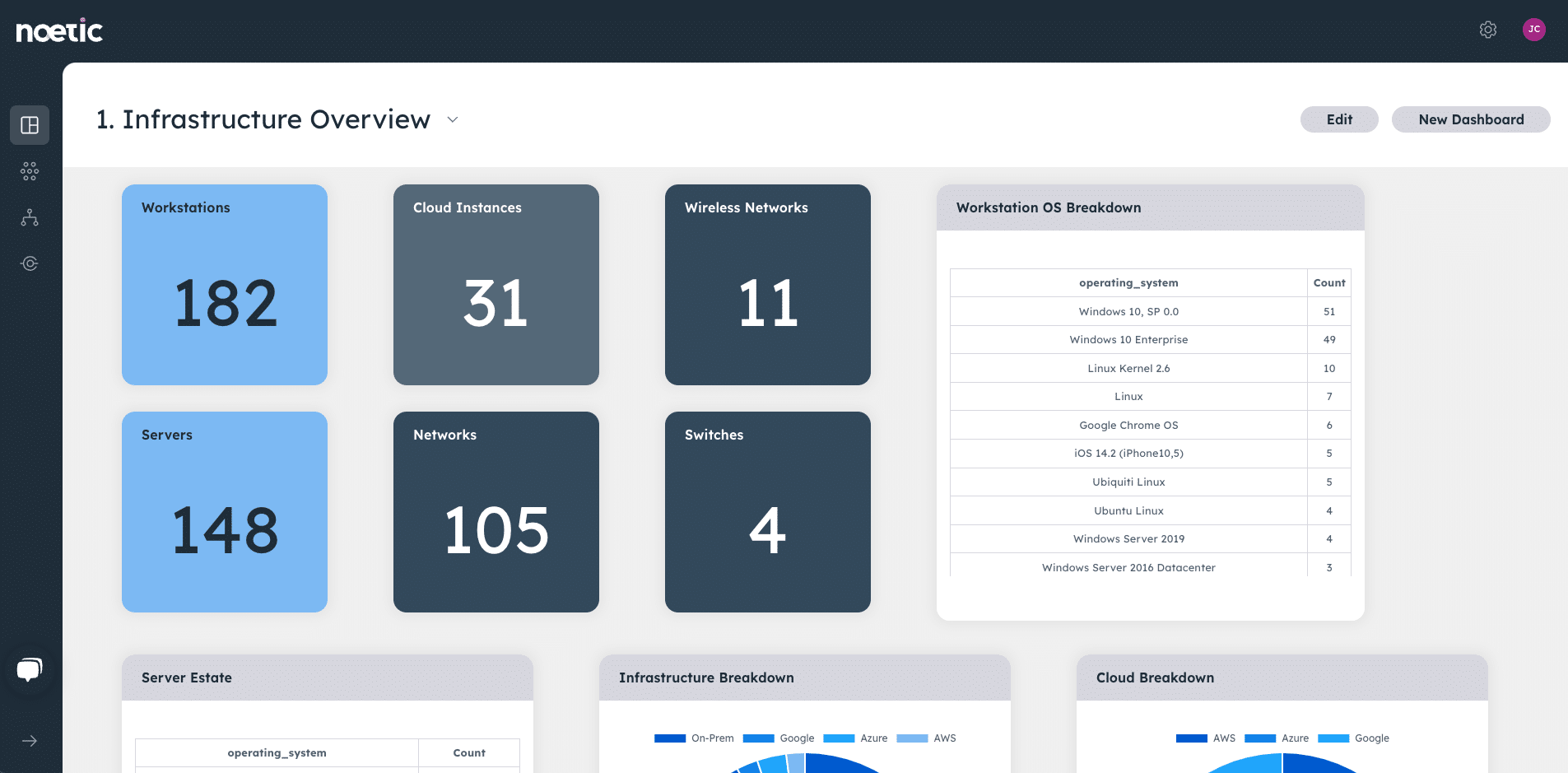
This is a starting point for Zero Trust. It serves as a detailed map to help you understand your critical assets based on the relevant business and security context, how secure they are, where they fit into business processes and what their access requirements are. From there, you can start to automate policy enforcement in line with a rigorous Zero Trust approach, minimizing the blast radius of breaches and reducing cyber risk.
Watch this video to learn more about how the Noetic platform builds out a new kind of ‘full-stack’ visibility for the security team, or you can request a personalized demo to see the platform in action.
