6 Security Incident Response Questions for CISOs
The Incident Management Challenge
Despite the unprecedented number of cyber incidents that occur every day, over half (56%) of companies still do not have a cyber incident response (IR) plan in place today. With attacks becoming more severe and discrete than ever, organizations are putting themselves at significant risk by neglecting to implement proper security policies and procedures.
If the growing prevalence isn’t enough to demand boardroom attention, the associated price tag should raise a red flag. IBM’s Cost of a Data Breach 2022 revealed that those that do have a regularly tested incident response team save an average of $2.66 million compared to those that do not.
Still, the findings do not suggest those with plans in place enter the clear—as the average cost of a data breach reached an all-time high of $4.35 million. Rather, the trends suggest companies focus on adapting their initiatives to match the growing complexities of our interconnected environments.
As such, meaningful contextual insights must take precedence over the key performance indicators (KPIs) traditionally used to measure IR plan success.
What KPIs are incident response teams typically measured on?
While there are many metrics used throughout the incident management process, the following KPIs are usually the most indicative of whether a deeper problem exists:
- Incidents Over Time can visually track progress or indicate areas for improvement by displaying the average number of incidents by day, week, month, year, etc.
- Mean Time to Detect (MTTD) is the average time it takes for the appropriate team member to respond to a system alert. This metric can be a good indicator of what a team’s workload is like—whether it’s too much, or not enough—and shed light on whether everyone is internally aligned on individual responsibilities.
- Mean Time to Respond (MTTR) is the amount of time it takes to diagnose and remediate the issue so that it does not continue happening.
Although the above metrics should still play a role in measuring security response effectiveness, they should not be the sole indicator of how skilled your team is, or how well your plan is working.
How to Evaluate Incident Response Beyond Standard Security KPIs
Traditional metrics are not enough to measure the strength of a plan or team because the numbers fail to provide the context and insight necessary to understand the overall business impact and cyber risk associated with each alert.
Before you can measure your incident response team’s ability to detect, route, and/ or respond to a security incident, you must consider the following:
- Are we aligned on internal roles and responsibilities?
While it may seem like it goes without saying, many security professionals struggle to understand what’s expected from them due to the amount of overlap between security, risk, IT and DevOps teams.
“Because so many groups can be involved, depending on the nature of the incident and the required response, having defined interfaces and assigned roles and responsibilities is a key requirement.” – CISA
- How are we keeping up with the growing attack surface?
Many integral players are kept out of the loop when it comes to significant IT projects and initiatives that can drastically expand the attack surface. As shadow IT continues to create blind spots, the expanding use of SaaS applications, application deployment, and IoT/ OT devices adds to the workloads of a function that’s already experiencing a talent shortage.
- Are the proper tools in place to protect, detect, contain, and resolve incidents?
Seventy percent of organizations are running at least 10 tools for security hygiene and posture management alone, creating a huge obstacle for incident responders that need to act as quickly as possible.
With spreadsheets remaining a key aspect of the entire management lifecycle, point-in-time assessments make it hard for IR teams to stay ahead of the adversary.
- Does my IR plan consider the “ripple effect”?
The average time to identify and contain a breach is 277 days (IBM, Cost of Data Breach 2022). By then, malicious actors can do a lot of damage. Teams need to know and be able to identify the blast radius in the event of an incident to drastically expedite the mean time to respond (MTTR) and, if necessary, notify all necessary properties.
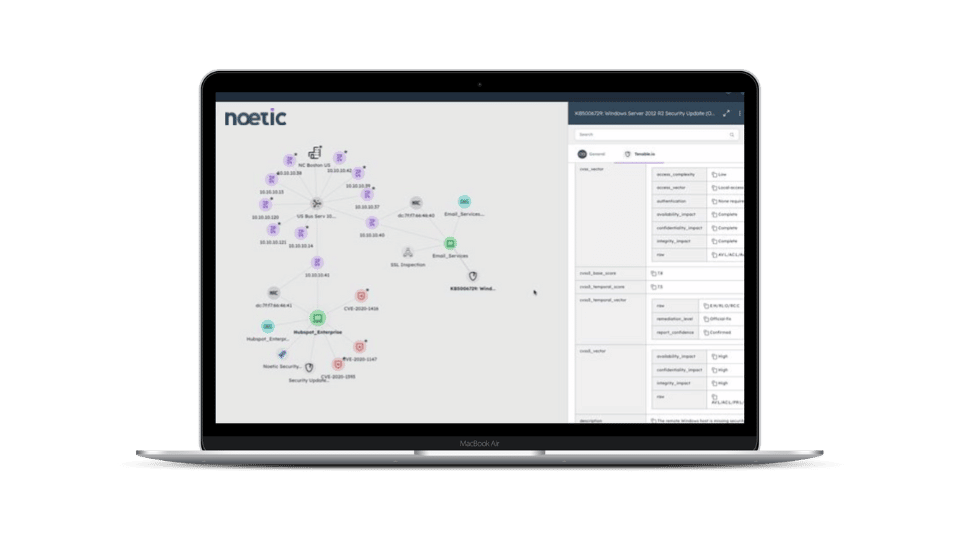
- Does my IR plan include guidelines for vulnerability prioritization?
Fifty-nine percent of cybersecurity professionals feel the demands of their job limit them from keeping up with cybersecurity skills. (ISSA & ESG) While IR teams need to know how to identify and address their most critical vulnerabilities before they can be exploited, organizations need to clearly communicate and train their staff on how to do so.
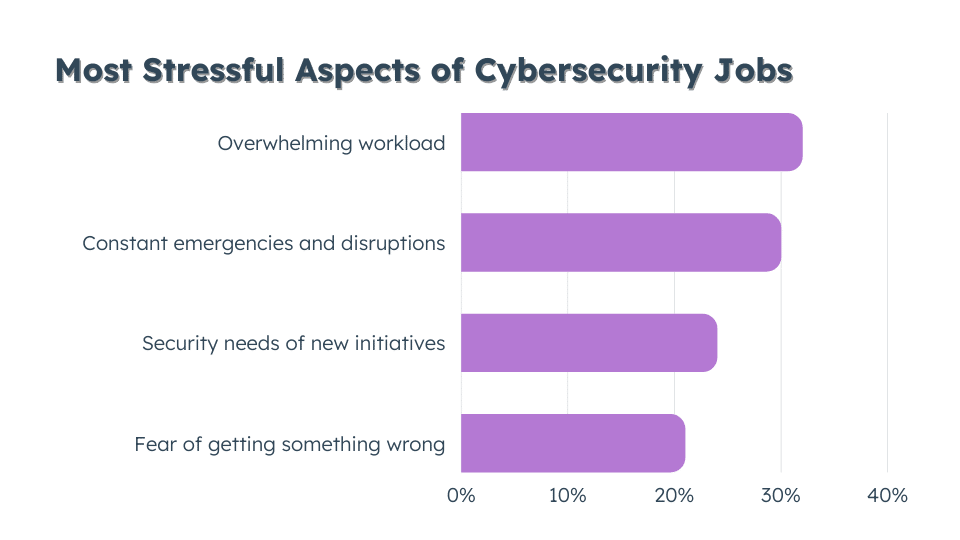
- Am I effectively reporting to the board?
Relatedly, no amount of skill or speed can ever ensure a 100% vulnerability-free attack surface. However, detailing remediation efforts according to risk levels can paint a more detailed picture that quantifiable metrics on their own cannot.
There are a lot of moving parts when it comes to incident management. While traditional incident response metrics are effective at suggesting a closer look, they shouldn’t be the end-all-be-all for evaluating the success of your incident response plan.
Get more insight into what’s really working, what’s not, and how to reach your desired state with a single view of your entire cyber ecosystem. Join Noetic’s next live demo to learn more.
- Noetic’s acquisition by Rapid7: Giving our customers more comprehensive visibility of their attack surface
- The Cybersecurity Investment Blueprint: Insights from Iren Reznikov
- Strength in Unity: The Power of Cybersecurity Partnerships
- How to build cyber resilience by prioritizing the right vulnerabilities
