How to build cyber resilience by prioritizing the right vulnerabilities

Software vulnerabilities are an inevitable consequence of human-made coding errors. Yet their exploitation on a large scale threatens to undermine the digital foundations on which businesses are built. From large-scale supply chain attacks to highly targeted spyware operations, ground zero is increasingly a buggy product. The challenge of patching these CVEs is overwhelming. A record number has been published to the National Vulnerability Database (NVD) for the past seven years.
Security and IT Operations teams can never hope to patch every single vulnerability that appears in their environment. But they can prioritize them according to potential risk. This is where organizations need a continuous stream of high-quality data to provide insight and context for better decision making.
What’s the problem with vulnerability management?
Vulnerability exploitation was behind the infamous MOVEit supply chain campaign of 2023, which is estimated to have compromised nearly 3,000 organizations and 95 million downstream customers. It enables commercial spyware vendors to arm autocratic regimes with zero-click malware to eavesdrop on opponents. And it’s a top initial access vector for high-impact ransomware attacks.
The bad news is that CVE volumes are surging, thanks to the sheer number of software products and open-source components making it to market, poor DevOps practices, highly motivated threat actors and ubiquitous bug bounty programs. In 2023, the number of vulnerabilities posted to the NVD stood at over 29,000. And in 2024, the NIST NVD is no longer keeping up. The challenge for security teams is exacerbated by two adjacent factors:
- Threat actors are getting faster at vulnerability exploitation. When they’re not researching or buying new (zero-day) CVEs themselves, they’re pouncing on newly disclosed bugs. A quarter are exploited on the day of their publication, according to Qualys.
- A proliferation of vulnerability findings. Security teams run multiple security tools across endpoints, cloud systems and other parts of their IT environment. These will often push out overlapping information on the same exploits and assets, making it harder to filter out the noise and gain a clear aggregated view of exposure and risk.
Unfortunately, these challenges have real-world consequences. According to Verizon, the volume of data breaches stemming from vulnerability exploitation in 2023 surged threefold annually. It was an “action” in 10% of all breaches analyzed.
Why context matters
Prompt patching is the best way to mitigate this kind of threat. But it remains elusive. A Verizon analysis of the Cybersecurity Infrastructure and Security Agency (CISA) Known Exploited Vulnerabilities (KEV) catalog indicates that:
- At 30 days 85% of vulnerabilities went unremediated.
- At 55 days, 50% of vulnerabilities went unremediated.
- At 60 days 47% of vulnerabilities went unremediated.
- At 180 days, 20% of vulnerabilities went unremediated.
- At 365 days 8% of vulnerabilities went unremediated.
When it comes to detecting mass exploitation of vulnerabilities listed in the KEV catalog, the median time taken is five days.
So how can organizations bridge the capability gap and prioritize CVEs for patching more effectively? Context is critical. This means collecting information continuously from different data sources to provide insight into:
Environmental factors such as:
- Asset exposure: whether an impacted asset is internet-facing or protected by a firewall or load balancer.
- Business criticality: whether an impacted asset supports a tier-1 application, has access to sensitive corporate data or other factors.
- Where a CVE is present in the IT environment.
- Whether multiple exploits can be prevented with minimal patching.
- Whether there are any relevant compensating controls in place.
Exploitability – I.e. how easily a vulnerability can be exploited by threat actors. Reliable sources of information here might include:
- CISA KEV, which is a curated list of vulnerabilities which have been exploited in the wild.
- The Exploit Prediction Scoring System (EPSS) from the Forum of Incident Response and Security Teams (FIRST).
- Commercial vulnerability threat intelligence providers, such as Recorded Future or Mandiant.
Also important at this stage is to understand if there are even patches currently available for a specific CVE. Priority should be given to mitigating zero-day exploits.
Severity – i.e. how serious an impact an exploit could have on the organization. A common way to assess this is via the Common Vulnerability Scoring System (CVSS). Version 4 considers the impact on confidentiality, integrity, and availability, and a range of other factors. Vulnerability and patch management teams may suffer here from a backlog in processing of new CVEs by NIST, meaning the NVD isn’t the reliable source of information it once was. The emerging CISA vulnerability enrichment program may help.
Existing controls that the organization has in place which may help to mitigate the impact of an exploit. A review of existing controls may be necessary here, to check for relevant firewalls, intrusion detection/protection, access controls, DDoS mitigation etc. This is useful context as if strong mitigating controls are already in place for an exploit, the security team may want to focus their efforts instead on CVEs which could be exploited to cause more immediate damage.
The Noetic difference
With this context to hand, organizations can theoretically start to prioritize more effectively which CVEs to patch first – based on the potential impact of a vulnerability exploit on their specific systems, the likelihood of a CVE being used in the wild, and how well existing defenses could deal with it. But the likelihood of being able to operationalize this information effectively in patching programs may be limited if it is not presented in an intuitive and actionable manner.
Noetic can build a comprehensive picture of security posture for customers by gathering data from a wide variety of sources, including third-party vulnerability and asset management tools, and vulnerability intelligence repositories like FIRST, CISA KEV and NIST NVD. We provide relevant business context such as the criticality of impacted assets and data, and relevant compensating controls. And we consider the relationships between assets to help us map potential attack paths and inform decisions on which patches to prioritize.
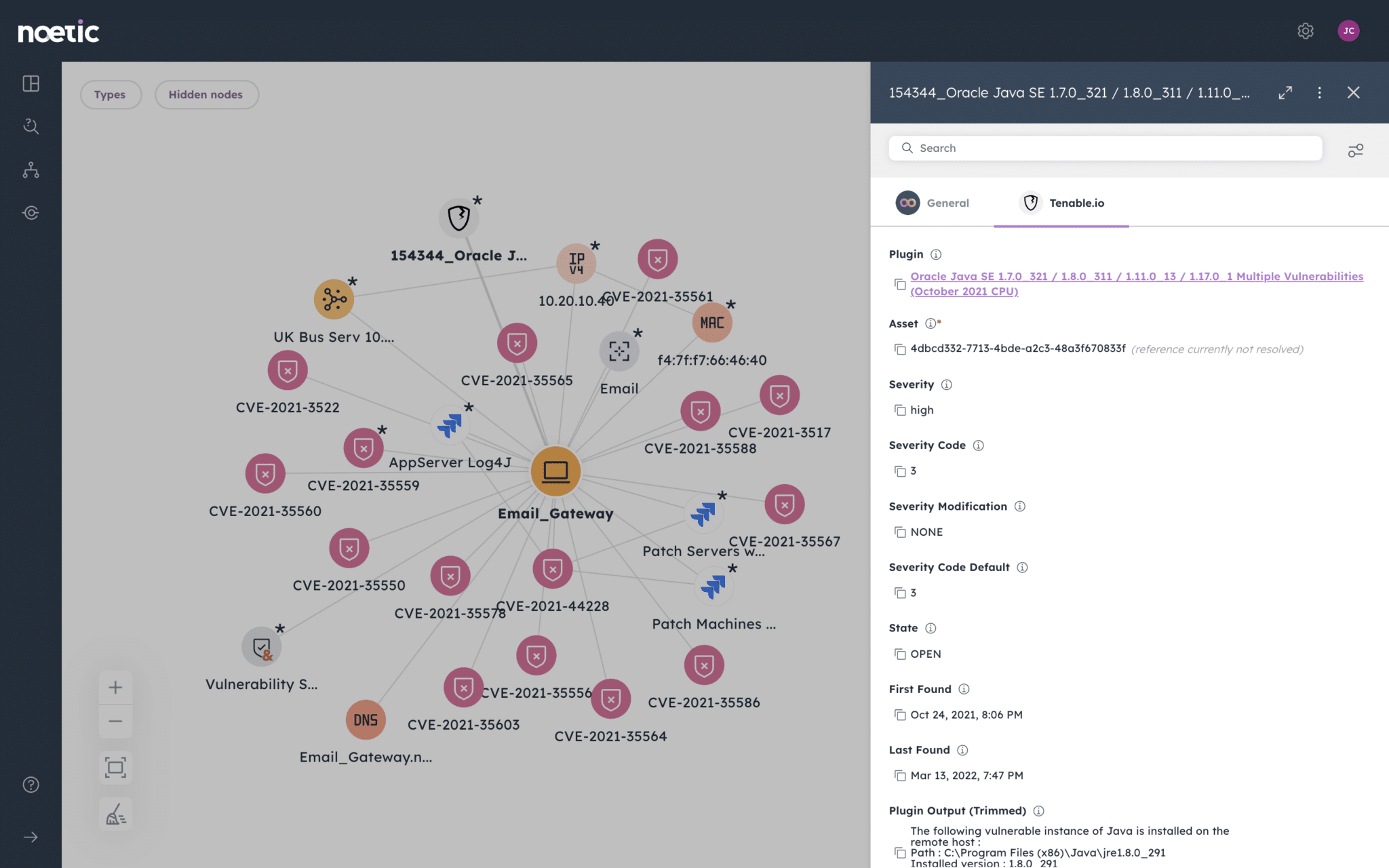
Most importantly, this data can be investigated by business unit, geography, cloud account and other variables for granular context. And there’s the ability to create powerful automated workflows to streamline remediation.
Vulnerability prioritization is just one part of a continuous threat exposure management (CTEM) approach, which Gartner claims will help organizations to reduce their likelihood of experiencing a breach threefold by 2026. Noetic delivers key capabilities to support each of the five pillars of CTEM.
To find out more about how Noetic can help your organization build resilience with better exposure management, download our guide: How to Implement CTEM with Noetic.
