IT Operations – Security Convergence: Best Practices for CMDB Success

In the ever-evolving IT landscape, the Configuration Management Database (CMDB) is a critical foundation for organizations seeking to streamline operations, inform decision-making, and enhance service delivery. However, the path to CMDB success is riddled with challenges that have left many teams frustrated and unable to harness its full potential.
Despite the potential benefits of implementing a CMDB that we previously shared, the startling reality is that only 25% of organizations are deriving meaningful value from their CMDB investments. These disappointments are not without reason, as infrastructure and operations (I&O) leaders have grappled with recurring roadblocks for decades.
By dissecting these common challenges, we can illuminate the path forward, enabling I&O teams to navigate their CMDB efforts with greater efficacy and provide the foundation for any effective cybersecurity initiative.
Most Common CMDB Pitfalls
- Poor, inconsistent data quality limits CMDB effectiveness.
One of the most common CMDB challenges is ensuring data accuracy and quality. Inaccurate or inconsistent data can undermine the effectiveness of the CMDB, leading not only to ill-informed decision making, but also significantly impacting operations. In fact, Gartner® research indicates that through 2024, 99% of organizations using CMDB tooling that do not confront configuration item (CI) data quality gaps will experience visible business disruptions.
- Data ownership gaps and resistance to change present serious concerns.
Many I&O teams lack clear accountability for keeping configuration item (CI) records up to date. This lack of ownership makes it challenging for I&O leaders to maintain current and reliable data, which is crucial for informed decision-making.
Additionally, implementing a CMDB often requires changes to existing processes and workflows. Resistance to change from stakeholders can hinder the implementation process and impact the success of the CMDB. Effective change management and clear communication are crucial to address this challenge and gain buy-in from all stakeholders.
- Outdated practices that are unable to keep up with the surge in cloud service adoption.
CMDB tools have traditionally focused on tracking and controlling component relationships vital for service delivery. This approach falters in cloud environments where visibility into the intricate service stack is limited, let alone the control of rapid changes.
Traditional CMDB tools were designed with a lower velocity and volume of change in mind, which the cloud far exceeds. Consequently, increased cloud adoption jeopardizes I&O’s ability to provide reliable data promptly.
- Unable to support wider use cases across the expanded organization.
In addition to service delivery and change management processes, the CMDB should be a key part of an organization’s cybersecurity and risk management processes. However, security teams are reluctant to rely on ITSM platforms, as their content and focus is mostly aligned with I&O, failing to adequately cater to security-related demands.
Security leaders require accurate information of asset ownership, relationships, and technical characteristics to properly understand their security posture. Data gaps and the inability to leverage this information for security and risk reporting limits their usefulness.
Five Steps to Building a Successful CMDB
A CMDB is a complex undertaking. Service asset and configuration management (SACM) programs were introduced to guide teams through their CMDB initiatives. This multifaceted practice can also provide the foundation for many advanced cybersecurity initiatives. To maximize the efficacy of the CMDB, SACM programs include the following:
- Identify goals and objectives.
The first step in maintaining an accurate CMDB is to determine what you want to achieve with the CMDB and how it aligns with your organization’s overall IT and security strategy. This will serve as a guide and help measure success throughout the entire implementation and maintenance cycle.
To minimize exposure to risks and optimize operational efficiency, leaders of both I&O and security departments must collaborate and establish shared cybersecurity objectives. I&O leaders should initiate this process by assessing their relationship with the security department, potentially requiring consensus-building between the Chief Information Officer (CIO), Chief Information Security Officer (CISO), and Chief Technology Officer (CTO) to lay the foundation for these crucial joint strategy discussions.
- Define clear roles and responsibilities.
The success of CMDB efforts can usually be determined by the clarity of the roles and responsibilities designated during the SACM process. A successful program that maximizes the value of its CI data involves three distinct roles: the executive sponsor, the SACM program lead, and the technology owner(s)/ custodian(s).
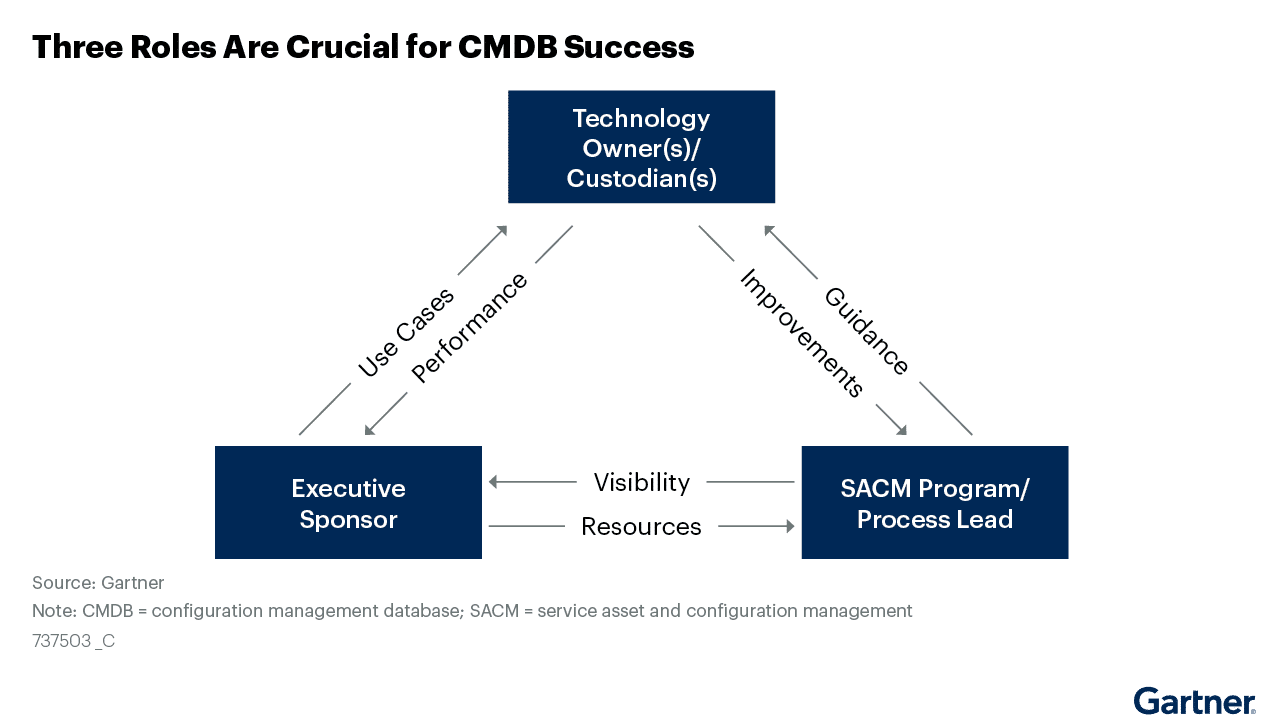
Source: Gartner®, 3 Steps to Improve IT Service View CMDB Data Quality, December 2020
- The executive sponsor is usually assigned to a seasoned IT leader such as a Chief Information Officer, and advocates for initiatives aimed at realizing this significance of technological resources throughout the entire enterprise.
- The focus of the SACM lead is usually on outlining the essential tasks required for technology assets to meet their objectives and advocating for enhanced coordination of these tasks throughout the organization.
- Multiple technology owners/ custodians are recruited to align one or more technology assets with the requirements of their stakeholders. Additionally, it actively supports endeavors aimed at guaranteeing that the technology asset and its related data effectively serve the defined use cases.
Given the expanding threat landscape, it is imperative to seamlessly integrate security throughout tools and processes. To effectively counter these risks, organizations must proactively identify opportunities for aligning goals and addressing cybersecurity considerations across all operational levels.
- Establish a data governance process.
The success of a CMDB relies heavily on the accuracy of the data it contains. Yet, the average CMDB is only about 60% accurate. The solution begins with a meticulous examination of each CI data model attribute.
To maintain optimal CI data quality, every CI record attribute that is tracked must serve a clear use case for decision-making and be maintainable. Document the precise use case for each attribute and define a system of record for the inventory of each technology asset type. This serves as the data source for each CI record data element, minimizing confusion among all parties involved by establishing a standard for all sources.
- Consolidate resources for maintaining CI data.
The CMDB typically contains data that aids I&O personnel in expediting change management and supporting efficient incident resolution. On the security front, SecOps analysts might utilize the CMDB to scrutinize patch levels for vulnerability assessments within the environment. When various I&O and security technologies align with shared objectives, a vital prerequisite is to ensure that each tool aligns with its original purpose.
Tools are undoubtedly essential to optimize CI data quality, particularly at scale. However, here’s a crucial point to consider: many organizations invest in these tools but reap little benefit from their data sources. The reason? Siloed data. Data that resides in isolated pockets often contains errors and conflicts, which hinder the speed and quality of decision-making—something I&O leaders actively seek to improve.
To overcome this challenge, a unified approach is necessary. Each CI attribute should have a clearly defined system of record for its current state, and this system should be consistently utilized by all IT service management (ITSM) stakeholders. This approach bridges the gaps between siloed data and ensures that everyone is working from the same, reliable data source.
- Ensure your CMDB is built to scale.
The dynamic nature of today’s environments cloud introduces complexities that outpace the capabilities of traditional CMDBs, threatening the accuracy and relevance of the data they provide. This involves reshaping dependency tracking and the role of CMDB tools to balance the advantages of high-quality data for decision-making against the costs and risks of managing this information.
While traditionally considered the “single source of truth,” the role of the CMDB should evolve into that of one system of record among many. This evolution entails a refined scope of data stored within the CMDB tool and the delegation of detailed component data to tools better equipped to handle the diverse, voluminous, and rapidly changing data streams inherent in the cloud environment.
The path to maximizing the return on CMDB tooling lies in addressing these common challenges head-on, while also proactively identifying avenues to align goals and address cybersecurity considerations throughout. doing so, organizations can transform their CMDB investments into invaluable assets that drive informed decision-making and operational excellence in the ever-evolving landscape of IT infrastructure and operations and security.
To establish this alignment, enterprises need to adopt a holistic approach that encompasses the implementation of robust security measures across assets, tools, and processes. The Noetic Cyber Asset Attack Surface Management (CAASM) platform was designed to do just that.
The platform not only aggregates critical data from your existing security and IT management tools, it also processes information from catalogs and spreadsheets, as well as external intelligence feeds from NIST, FIRST, and more. Therefore, providing additional layers of business criticality and context, enabling teams to optimize spend and deduplicate efforts.
See for yourself how Noetic can help you turn the tide and reap the rewards of a well-executed CMDB strategy. Register for an upcoming live demonstration of our award-winning CAASM platform.
