The 5 Key Elements of Continuous Threat Exposure Management
The heightened priority security leaders have assigned to attack surface management (ASM) in 2024 is grounded in numerous factors. Given the challenging task faced by teams in comprehending and mapping an intricate digital environment, however, it is essential to contextualize ASM within a broader security initiative that emphasizes a stronger focus on prevention as part of a wider cybersecurity program.
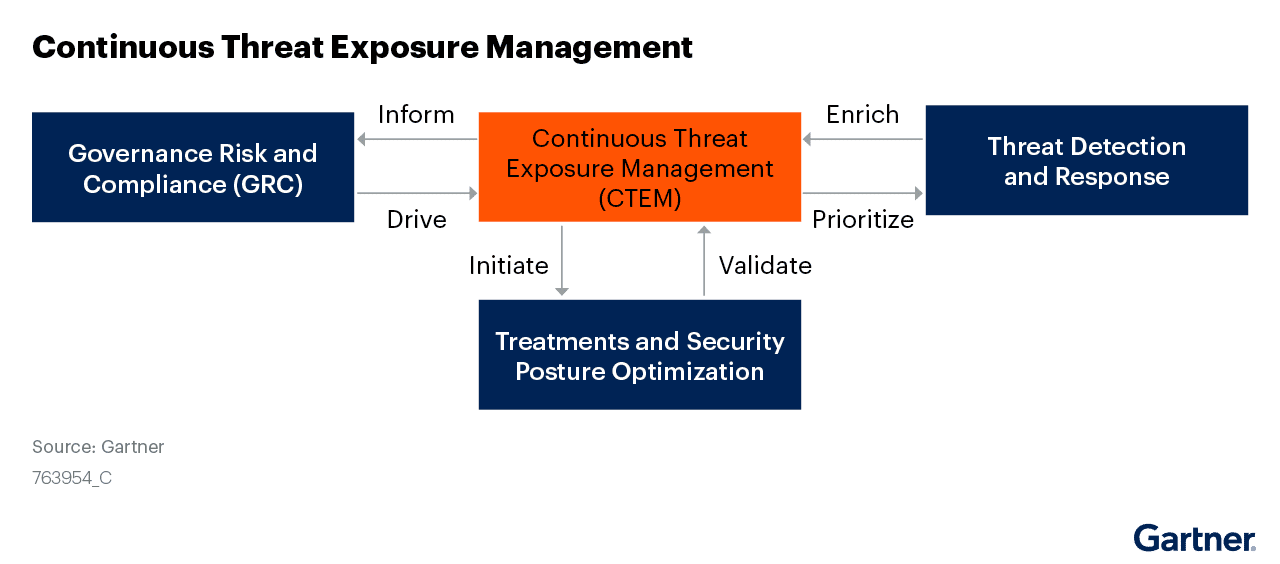
As such, continuous threat exposure management (CTEM) has emerged as a comprehensive, actionable framework for analyzing, acting on and improving organizational security posture. This five-step methodology empowers organizations to gain a deeper understanding and take prompt action based on a thorough, contextual analysis of their cyber estate on an ongoing basis. In turn, facilitating a more proactive approach to addressing cyber risk.
“The objective of CTEM is to get a consistent, actionable security posture remediation and improvement plan that business executives can understand, and architecture teams can act upon.” – Gartner®
At Noetic, we believe that an exposure management program is refined approach to managing the attack surface in a constantly changing digital world. This modern approach considers vulnerability prioritization and remediation, mitigating controls, asset inventory as well as detection and response capabilities as part of a wider initiative.
Exposure management has earned itself a spot among the transformational technologies that are shaping the future of security operations. That’s because the potential benefits of adopting CTEM are significant. According to Gartner®:
“By 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.”
At Noetic, we believe that an exposure management program is the best approach to managing the attack surface in a constantly changing digital world. This modern approach considers vulnerability prioritization and remediation, mitigating controls, asset inventory as well as detection and response capabilities as part of a wider initiative.
How to Implement a Continuous Threat Exposure Management Program
Noetic’s perspectives on the key steps that need to be addressed
Implementing this framework goes beyond the capabilities of a singular tool or platform. Regardless of where organizations are in terms of CTEM maturity, every CTEM cycle must include each of the following steps: scoping, discovery, prioritization, validation, and mobilization.
1. Scoping
The first challenge for any security team is to gain a comprehensive understanding of their environment. While organizations ideally would have defined this as part of their vulnerability management (VM) process, it often remains incomplete. The scope of CTEM adopts the “attacker’s view,” extending well beyond the internal and owned assets and associated common vulnerabilities and exposures (CVEs) that most VM projects are designed around.
This is an area where external attack surface management (EASM), network scanning and digital risk protection services (DRPS) can provide value as they are optimized for mapping the exposed attack surface, as well as potential threats from outside the organization. During this stage, it is especially critical to consider wider business priorities. Having that context around critical applications and services will impact prioritization efforts later in the process.
2. Discovery
Discovery is the second stage in CTEM, whereas the goal is to identify assets and evaluate the risk profiles for everything defined in the project scope. The significance of exposure discovery extends beyond vulnerabilities, and can also include misconfigurations, security coverage gaps and toxic combinations. It is entirely possible that the discovery phase will identify cyber risks which were outside the initial scope. This expansion places an increased emphasis on the subsequent “prioritization” step, where additional measures for “noise cutting” become essential.
3. Prioritization
Prioritization, the natural outcome of scoping and discovery work, is the third and arguably the most critical phase within the CTEM cycle. As security leaders know, it is not practical, or even desirable, to remediate every security issue identified. Security teams need to prioritize based on the risk to the business.
This has evolved beyond traditional vulnerability severity scores, which do not consider exploitability or the potential business impact on the affected assets. Effective prioritization of exposures requires security teams to consider a combination of severity, exploitability, the criticality of the potential impact to the business, as well as any compensating security controls. This is also an area where cross-functional collaboration between security, IT, and the Lines of Business (LOB) are vital.
4. Validation
The fourth step is validation, which typically involves controlled simulation or emulation of attackers’ techniques in production environments. The goal here is for organizations to put themselves in the mind of the adversary to assess the likelihood of success, estimate the highest impact, or “blast radius”, and evaluate the effectiveness of the remediation plan or response procedures.
This validation step should not only cover relevant threat vectors, but also consider pivot and lateral movement possibilities.
This is an area where security teams are increasingly investing in tooling and automation, whether for breach attack simulation (BAS), red teaming, or attack path analysis.
5. Mobilization
The fifth and final phase, mobilization, is focused on organizational readiness and preparation. This can, and should, include automated remediation. However, it is strongly advised that organizations avoid relying solely on the premise of automated remediation. Security teams must instead remain transparent in communicating their role in intervening during instances that extend beyond the capabilities of automation. For example, consider instances where there may be more than one viable fix, and/ or a tool proposes a fix that doesn’t align with stakeholder preferences.
As we have seen, vulnerability management and exposure remediation is a cross-functional task, whereas the requirements and potential impact of different parts of the business need to be considered. Therefore, mobilization needs to be about building a shared understanding of what cyber risk is acceptable and what business impact is not.
Getting Started with CTEM
As security leaders think about how best to reduce their attack surface and improve their security posture, they need to work on how to gain the asset visibility and context that will allow them to effectively scope, discover and prioritize their CTEM program.

Discover how Noetic provides continuous support throughout the CTEM cycle—from scoping, to mobilization.

GARTNER® is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.
