Crawl, Walk, Run: The Evolution of Cyber Asset Management (Pt III)
In this 3-part blog series, Jee Chung, Senior Solutions Architect at Noetic Cyber, applies his vast industry experience to share how organizations are extracting actionable insights throughout their journey with the Noetic platform. Read on to learn how users are leveraging Noetic for continuous controls monitoring (CCM) and automated remediation.
Run: Embracing Security Automation in Attack Surface Management
The opportunity for automation in minimizing threats and exposures is immense. Automating security and risk management (SRM) processes can help organizations detect and respond to threats faster, reduce the risk of human error, and free up valuable resources that can be used for other critical tasks.
As cyber threats continue to evolve and become more complex, the need for automated solutions has become even more-so apparent. However, the associated risks have created some hesitancy around fully embracing automation in security operations centers (SOCs).
Top Challenges of Security Automation
- False positives: Perhaps the biggest concern is that automated systems can generate false positives, which can lead to unnecessary alerts and waste of resources.
- Increased complexity: If not properly configured, automation can introduce new layers of complexity, making it difficult for security teams to effectively manage and maintain their systems.
- Lack of flexibility: Automated security systems may be rigid and inflexible, making it difficult to adapt to new threats and vulnerabilities.
- Pre-mature automation: Automating broken or immature processes may result in uncertain or inaccurate outcomes—especially as it applies to vulnerability remediation.
Despite these potential risks, the benefits of automation in cybersecurity far outweigh the drawbacks. According to the IBM Cost of a Data Breach report, organizations that fully implemented security AI and automation saved $3.05 million, reducing the total cost of a data breach by 65.2%.
To ensure that automation is implemented effectively, organizations need to carefully evaluate the maturity of their existing security data and processes—and implement the appropriate safeguards to ensure they achieve the right benefits with the minimum risk.
The Noetic Approach
As organizations evolve into a proactive approach to attack surface and exposure management, it’s important to keep in mind that every journey is different and will happen at its own pace. Whether you’re just getting started with cyber asset attack surface management (CAASM) or you’re looking to take the next step, Noetic can help you unlock the full potential of automation.
Fuel quick wins with enriched Cyber Asset Intelligence
Today, some security teams spend over half of their workday generating management reports. As discussed in part one of this series, the most obvious and fundamental benefit of leveraging Noetic to automate common cybersecurity processes is that it helps reduce the analyst workload.
Noetic automatically ingests, aggregates, and cross-correlates asset data to provide teams with a comprehensive, accurate, up-to-date view of their environment. In addition to this 360-degree view of assets and their current security posture, Noetic also enriches the data, providing important additional context to drive workload and prioritization.
Data sources for enrichment can include business criticality and dependency from CMDB tools like ServiceNow and Device42, vulnerability and threat intelligence from CISA’s Known Exploitable Vulnerability (KEV) catalog, NIST NVD, Microsoft Security Response Center, and more. We can also layer the MITRE ATT&CK® framework onto the combined asset model to help teams understand gaps in their current security controls.
From a governance, risk, and control (GRC) perspective, this also presents a significant opportunity to increase efficiency, accuracy, and effectiveness in the audit process. By leveraging Noetic, security teams can streamline previously manual audit procedures, reduce the risk of errors and omissions, and gain deeper insights into their control environment. This can ultimately lead to better decision-making, improved compliance, and stronger risk management.
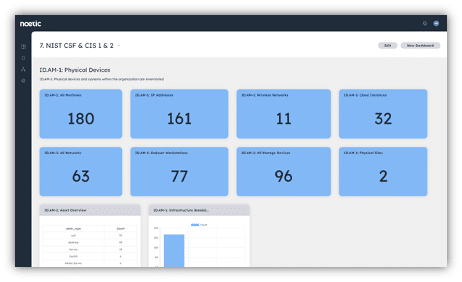
Rev the Noetic Workflow Engine
As you build confidence in the foundational intelligence built within the Noetic platform, you can start to take advantage of the automation capabilities of the Noetic Workflow Engine. A good starting point is to automate the notifications and ticket creations.
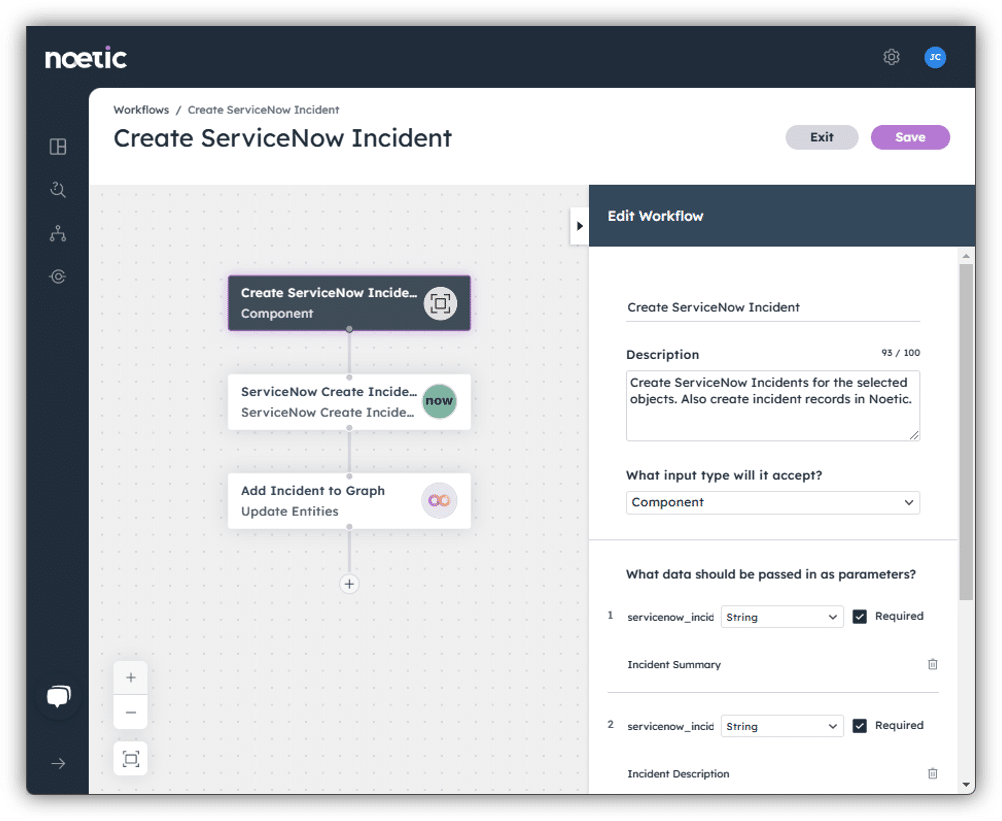
Highly quality data in Noetic that results from intelligent correlation and data enrichment assures minimal false positives and optimal focus in notification. The asset owners can be identified by information extracted from sources such CMDB or Active Directory. This initial phase of automation helps your organization gain confidence in the data and help identify area of internal process that may require adjustments prior to the next level of process automation.
Take action where needed
The powerful workflow engine can also help teams automatically enforce their security policy—returning assets to their “ideal” security posture and continuously correcting control drift. We refer to this to as a Noetic ‘loop’, where the platform is constantly reviewing the current state of assets against the desired level and working to adjust as appropriate.
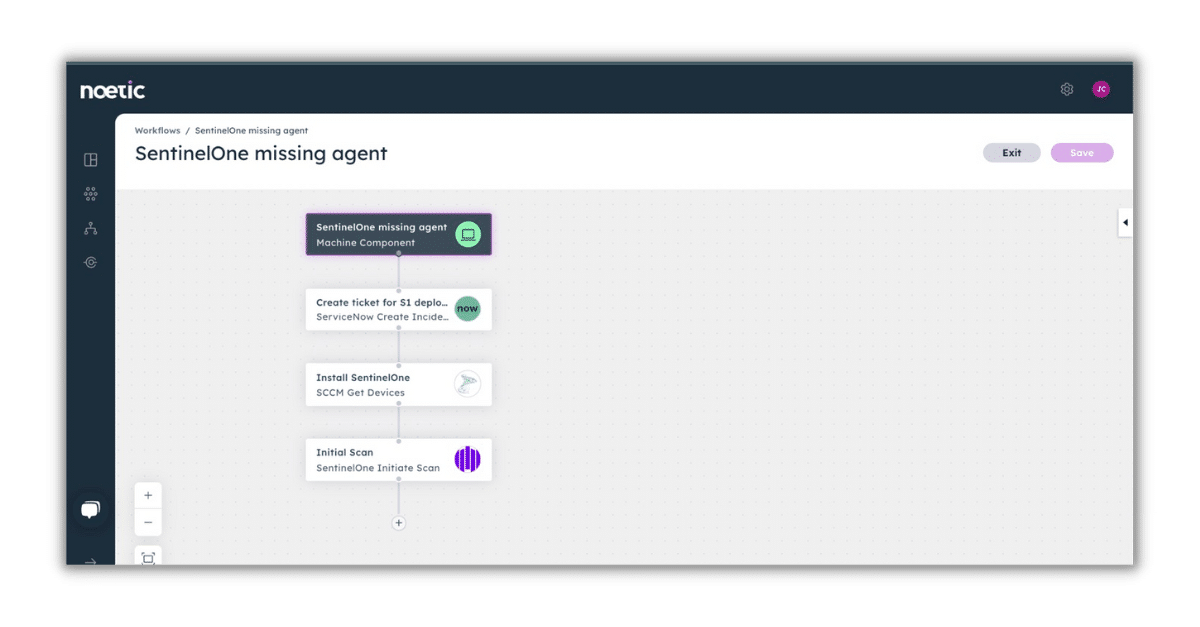
Say, for example, you run an automated query to detect machines missing an endpoint security agent. Earlier on in your journey (during the “crawl” stage) you’d likely use the workflow engine to notify the responsible party of any rogue or orphaned asset.
However, as you reach an advanced level of maturity with the Noetic platform and become increasingly confident in its capabilities, you may instead configure a bidirectional workflow that automatically triggers the deployment of a missing agent, with the appropriate documentation in the ITSM tool:
Taking that concept a bit further, you can automate cycles of remediation and rescan to ensure complete protection for the long-term:
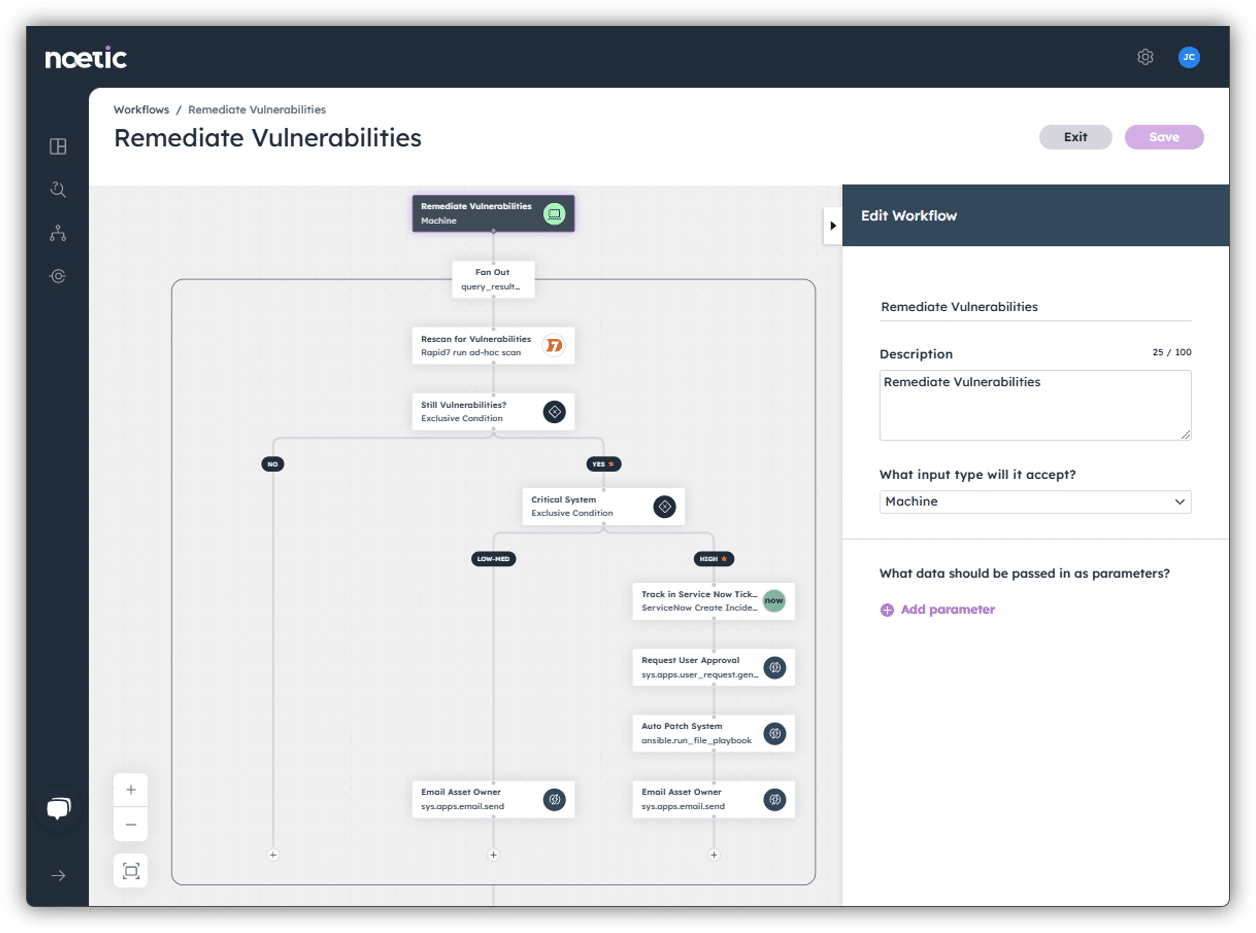
Time to action is critical in vulnerability management. Automating notifications and remediations to minimize the time gap between vulnerability detection and remediation helps minimize exposure. A side benefit of automating such actions is that gathering data to measure Mean Time to Remediation (MTTR) is also automated.
Metadata hygiene—staying ahead of the adversary
Even automated actions are still just reactions. Staying ahead of the adversary means constantly reassessing your cyber asset readiness. As a part of building a comprehensive asset inventory, Noetic can identify data gaps in existing systems of record, such as the CMDB, vulnerability management tools, or IT asset management systems.
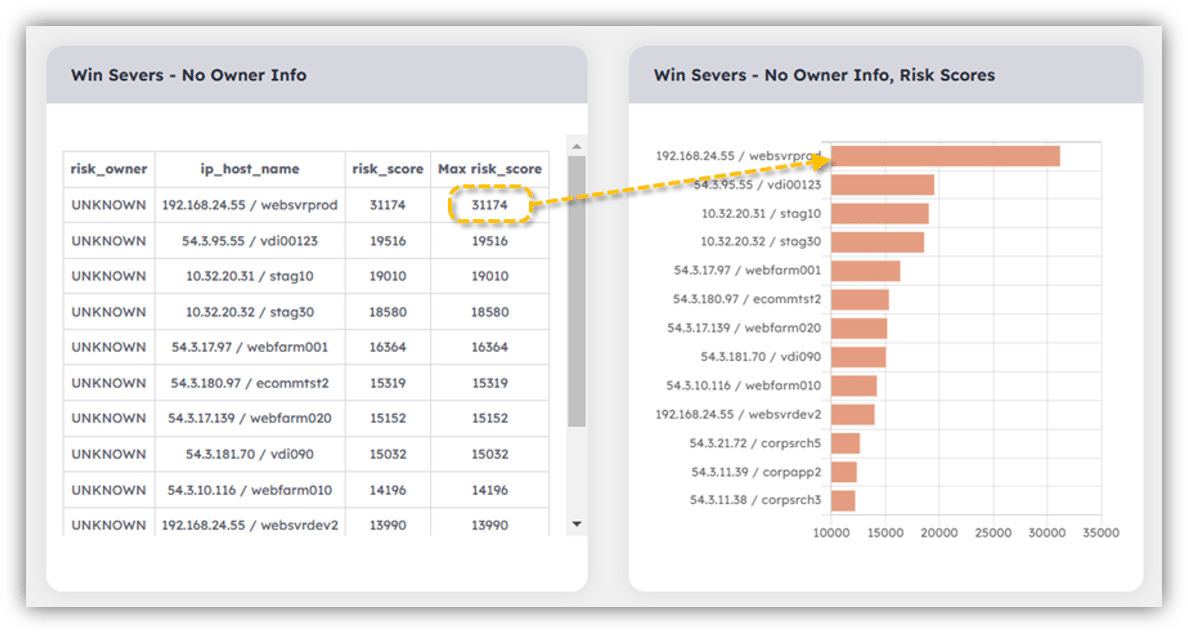
Noetic can then send notifications of such gaps or update the source systems with ownership information inferred from other correlated data sources, or tag them based on asset class, confidentiality, and other factors. The result: More complete data can then be fed back into Noetic in a continuous feedback “loop”—otherwise known as a cycle of continuous monitoring and improvements to the metadata.
Having a more complete metadata for your cyber security program ensures automated actions are targeted and actionable, thereby maximizing the productivity and efficiency of the risk owners, whose time is extremely valuable.
Used effectively, automation can be a force multiplier for your exposure management program. The key is to identify and start with low risk/high value use cases and scale your program in sync with the context and certainty you achieve from the Noetic platform.
As your data and organizational processes improve, the opportunities for automation increase. The ultimate, end goal is to maintain a 360º security hygiene and posture management mechanism that enables your organization to stay ahead of cyber threats.
Register for an upcoming live demo learn more about how Noetic can enable security and risk teams to embrace automation.
More in this series:
Crawl: How to Build and Maintain Dynamic Asset Intelligence
How to build and maintain dynamic asset intelligence with CAASM

Walk: Risk-Driven Vulnerability Prioritization
How to better prioritize threat and exposures with cyber asset attack surface management

