Navigating the Future: What’s next for Attack Surface Management?
Attack surface management (ASM)—the process of identifying, assessing, and managing vulnerabilities, misconfigurations and other potential entry points into an organization—has become a critical component of any cybersecurity program. Yet most ASM programs are structured to run periodically and focus on discrete assessments that provided a snapshot of their cybersecurity posture at a given point in time.
However, as the nature of cyber threats have become more sophisticated and dynamic, a more proactive and comprehensive approach to attack surface management is required.
What’s causing this shift in attack surface management?
- Advanced Persistent Threats (APTs): Most (78%) companies have experienced downtime as a result of an APT attack. APTs are sophisticated, targeted attacks that can bypass traditional security defenses. Proactive measures such as threat hunting, continuous monitoring, and leveraging threat intelligence are necessary to detect and respond to APTs.
- Remote work and BYOD: There are three times the number of remote jobs today than in 2020. With this shift in recent years to a more remote workforce and the growth of bring your own device (BYOD) policies has expanded the attack surface for organizations. Managing and securing remote endpoints and employee-owned devices is crucial to prevent unauthorized access and data breaches.
- Increased adoption of cloud computing: When upgrading or purchasing new technologies, 72% of organizations are defaulting to cloud-based services. As more organizations move their infrastructure and applications to the cloud, the attack surface inevitably expands. Attackers target cloud-based systems and misconfigurations, making it essential to proactively manage and secure these environments.
- Insider threats: Insider threats–whether intentional or accidental–continue to pose significant risks, and more than half of organizations have experienced an insider threat in the last year. Proactively managing user access rights, monitoring user activities, and implementing security awareness training can help mitigate these risks.
- Third-party risk: Organizations rely on third-party vendors, partners, and contractors to meet their business needs, which introduces additional security risks. According to a September 2022 Gartner® survey, 84% of executive risk committee members indicated third-party risk “misses” resulted in at least operations disruption within the past 12 months. A proactive approach to managing third-party risk involves regular assessments, contractual obligations, and ongoing monitoring to ensure the security of the extended network.
Attack Surface Management Tools
Organizations continue to respond to the increasing complexity of today’s threat landscape by adding more technologies, services, and personnel to assist in their attack surface reduction strategy. At a high level, most of today’s ASM programs are supported by three main capabilities: cyber asset attack surface management (CAASM), digital risk protection services (DRPS), and external attack surface management (EASM).
- The primary use case for any basic-level cyber asset attack surface management (CAASM) platform is to continuously enhance visibility by aggregating asset and vulnerability information within a single, comprehensive source.
- DRPS technologies, as the name suggests, monitor for threats and unusual activity across the open, deep, and dark web. In doing so, these solutions help security teams detect and thwart sophisticated threats such as social engineering attacks.
- Like CAASM tools, external attack surface management (EASM) solutions are designed to equip teams with the intelligence they need to assess their attack surface from the adversary’s perspective. The difference with EASM, however, is that these services prioritize mapping the digital footprint of internet-discoverable and third-party facing assets.
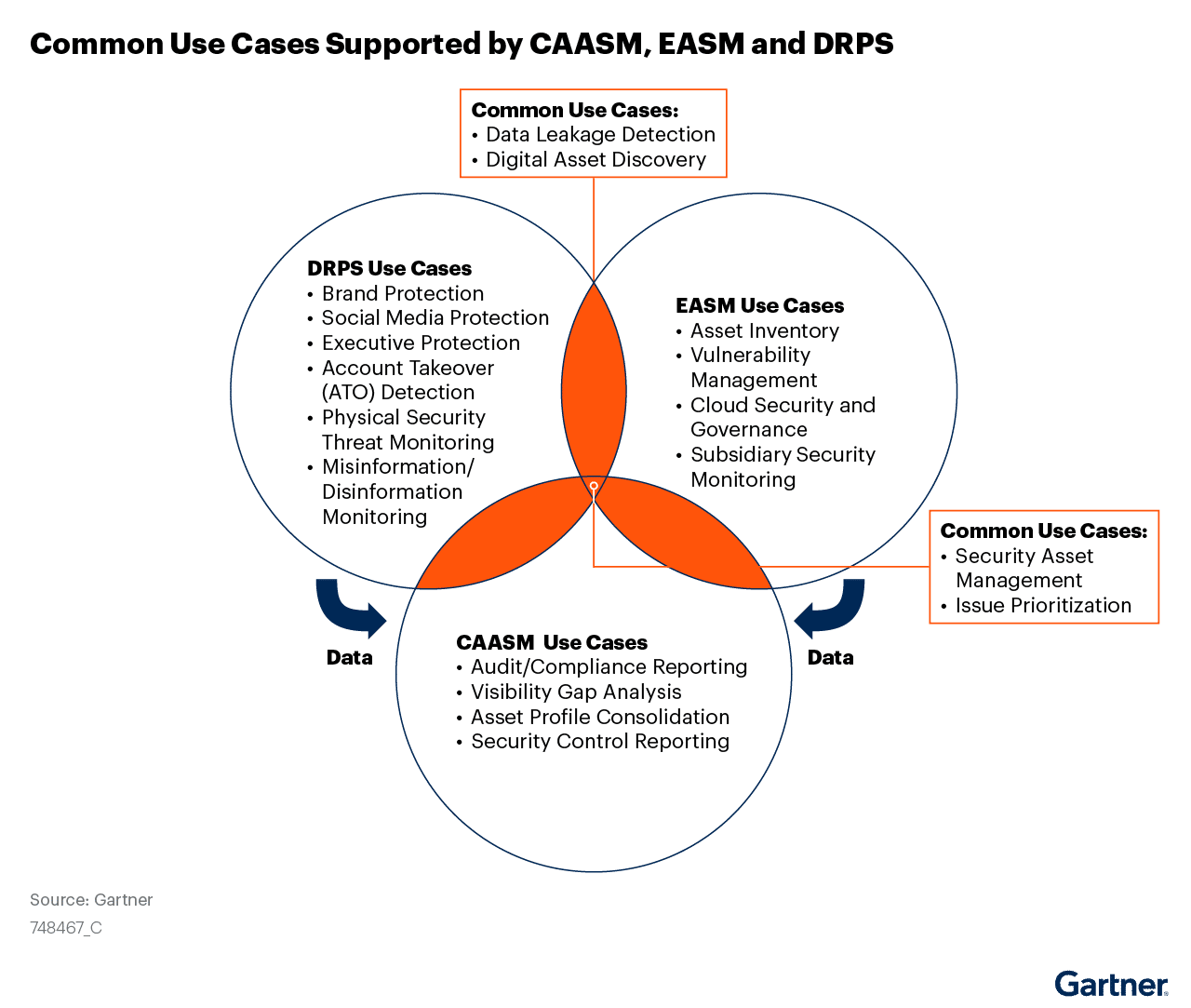
As a result, security teams are becoming more aware of their attack surface and how it can be exploited by the adversary. However, a major problem still exists, as the application of ASM remains siloed and tool centric. Although these technologies play a pivotal role in reducing the attack surface, security and risk leaders cannot confidently rely on a single source to continuously assess, prioritize, remediate, and improve their security posture.
Although common, technology-driven approaches to attack surface management are no longer adequate—an integrated approach, iterative approach has emerged. Embracing continuous threat exposure management is crucial for organizations to proactively defend against the ever-present and ever-evolving cyber threats.
Stay tuned for our upcoming blog posts, where we will explore various aspects of this evolving discipline, including best practices and strategies for effective continuous threat exposure management. Join us as we navigate the future of attack surface management together, protecting our enterprise ecosystems from the threats that lie ahead.
To learn more about the evolution of attack surface management into continuous threat exposure management, download the Gartner® report.
