Security Asset Management Statistics to Know in 2023
As IT and security leaders work to implement robust cyber asset management strategies, it is essential to have a clear understanding of the current state of cybersecurity. By examining some of the latest trends and figures in security asset management, organizations can better equip themselves to develop an effective strategy that safeguards against potential threats and ensures the integrity of their assets.
The Current State of Security Asset Management
From the increasing sophistication of cyber threats to the challenges of managing a decentralized workforce, the statistics on the current state of security asset management show that there remains a lot of work to be done.
*Unless otherwise cited, these statistics were derived from the 2023 Security Hygiene and Posture Management report by the Enterprise Strategy Group.
Cyber asset visibility remains incomplete.
- According to recent research by the Enterprise Strategy Group, the majority (73%) of organizations admit to only having a ‘strong awareness’ of less than 80% of their assets.
- The average time to identify and contain a data breach is 277 days (about 9 months). —IBM
Although organizations continue to invest in security hygiene and posture management (SHPM) practices, these figures prove just how challenging it is to keep up with the dynamic, interconnected nature of today’s environments.
Visibility is critical in security asset management because it provides insight into the assets that need protection and the risks associated with them. Without cyber asset visibility, it is challenging to track and manage assets effectively, leading to blind spots in security coverage.
Cyber threats increase in frequency (again).
- The total number of annual cyber-attacks increased 38% in 2022, compared to 2021.
- Recently, the number of weekly cyber-attacks increased 7% in Q1 2023 compared to the same period last year. — Check Point
The reasons behind this increase are multifaceted, ranging from advancements in technology to the growing reliance on digital systems in our daily lives. With the proliferation of connected devices and the rapid growth of data storage and processing capabilities, cybercriminals have become more sophisticated and better equipped to exploit vulnerabilities.
It is crucial for IT and security leaders to keep up with the evolving threat landscape and adapt their security strategies to effectively mitigate risks. This includes implementing robust security measures, investing in innovative technologies, and continuously educating employees about best practices and emerging threats. Failure to do so can leave an organization vulnerable to significant financial losses, reputational damage, and legal consequences.
Security asset management remains decentralized.
- Less than half–42%–of organizations claim they have completely centralized their personnel approach. Therefore, most organizations’ SHPM policies still rely on a combination of SecOps, IT operations, DevOps, and vulnerability management teams.
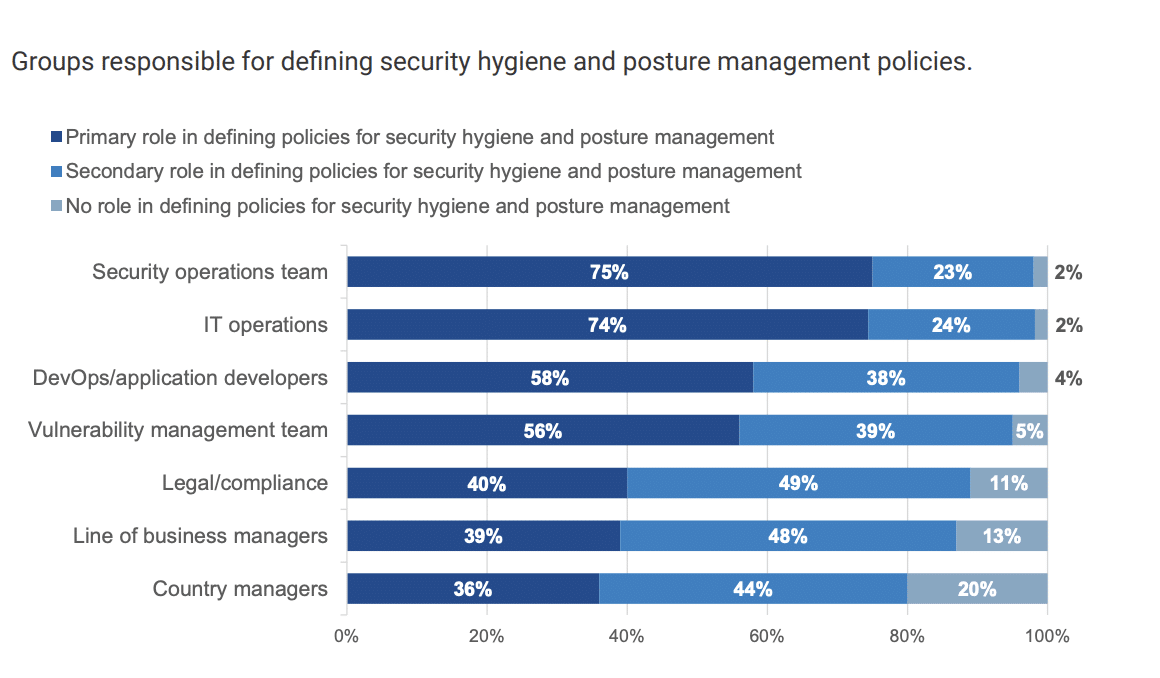
- Nearly 7 out of 10 (68%) IT and cybersecurity professionals agree that while their organization understands the importance of SHPM, it is difficult to prioritize the actions that can have the biggest impact on risk reduction.
- More than half (56%) agree it can be difficult to determine asset ownership when a vulnerability or misconfiguration is discovered.
Decentralization can often result in conflicting agendas, priorities, and information. Managing security across multiple locations and devices can create inconsistencies and gaps in security coverage, leaving the company vulnerable to potential threats. Security leaders need to develop a comprehensive security strategy that includes policies and procedures for managing assets across a decentralized workforce, ensuring consistent enforcement of security protocols, and safeguarding against potential security breaches.
“CISOs must take an active role here to ensure that collective efforts align with organizational goals of mitigating cyber-risk and maintaining resilience of business applications.”
– Jon Oltsik, Enterprise Strategy Group
AI and automation are reducing the burden on security teams.
- Most (91%) organizations are automating SHPM processes,
- Still, many teams are left to manually complete time-consuming tasks including generating reports (64%) and scanning for assets (67%).
- According to IBM, organizations that have fully deployed security AI and automation experienced a 65.2% reduction in the total cost of a data breach, saving them a staggering $3.05 million, compared to those organizations without—the largest cost savings in the study.
In today’s rapidly evolving threat landscape, AI and automation have become critical components for effective cybersecurity programs. These technologies offer powerful tools for incident response, enabling security teams to detect and respond to threats quickly and efficiently. But perhaps even more importantly, AI and automation can help prevent breaches from occurring in the first place. By analyzing vast amounts of data and identifying patterns and anomalies, these technologies can proactively identify potential threats and take action to mitigate them before they can cause harm.
AI and automation can also help reduce the burden on security teams by automating routine tasks such as vulnerability scanning, allowing them to focus on more complex security issues. Despite some growing pains, security AI and automation can offer an effective, scalable, and proactive approach to cybersecurity that is critical in today’s ever-evolving threat landscape.
Cybersecurity is a constantly evolving field, and security leaders cannot afford to be complacent. It is crucial to embrace a proactive mindset, prioritize security initiatives, and invest in cutting-edge technologies and talent. In the realm of cybersecurity, knowledge is power, and staying informed is the key to ensuring the resilience and security of your organization.
As a sponsor of the 2023 ESG Security Hygiene and Posture Management research, Noetic is proud to offer complimentary access to the full report. Download using the form below.
