Using CAASM to Enrich IT Asset Management
Cyber asset attack surface management (CAASM) may be an important emerging cybersecurity market, but one of its most promising applications is actually improving one of the oldest disciplines in IT: IT asset management.
The modern IT environment has become infinitely more complex in the last decade. Centralized procurement with defined gating processes has shifted to a growing democratization of IT purchasing and the associated rise of shadow IT. The balance of an organization’s ‘assets’ has shifted decisively from hardware to software, as well as from on-premises to the cloud. The discipline of IT asset management itself, however, has not evolved to align at the same pace of today’s environments.
A key use case for cyber asset attack surface management (CAASM) has emerged to bolster and improve the relevance of existing IT asset management systems by acting as a source of ‘clean’ data from existing security tools.
Traditional IT Asset Management, explained.
The roots of IT asset management are in tagging computer hardware with unique identifiers, registering key details such as the operating system (OS) it is running on, inputting a target refresh date as part of managing that physical asset’s depreciation cycle, and then issuing it to a named individual or business unit. Many organizations will also run agents on these devices to keep closer tabs on their whereabouts, perform some basic monitoring of the device’s health, raise relevant asset management alerts and the like.
Despite being one of the oldest IT disciplines, effective IT asset management is still a critical requirement for multiple stakeholders in any organization. especially midsized and large enterprises. Most obviously, it’s important for IT departments themselves. In addition, governance, risk, and compliance (GRC), security and individual line of business (LOB) teams also have a vested interest in enduring that IT asset management is done comprehensively.
As well providing inputs into the process, these stakeholders need access to an up-to-date view of all the assets in their environment, including the relevant associations and dependencies between them. For that reason, it’s common for these teams to support IT in the asset management process.
The role of your CMDB
Configuration management databases (CMDBs) have been the method of choice for IT asset management for many years. And they continue to remain core to how IT asset management is done in today’s software-driven context. As well as covering traditional IT asset management use cases, they are often a critical source of information on the respective business criticality of different applications. They can also provide key insights into application dependency, which is important when prioritizing vulnerability remediation.
CMDBs nevertheless suffer from fundamental limitations when meeting the needs of modern IT and cyber asset management. The data they hold is often incomplete, or out of date, and therefore practically useless. CMDBs are also heavily reliant on direct data inputs. They typically have limited discovery capabilities of their own, limiting their ability to look for and find things that they haven’t been told about.
CAASM: Helping to modernize IT Asset Management
A modern approach to IT asset management needs to take full account of software assets in the same way that it takes account of laptops and servers. Thanks to agile development processes and CI/CD software engineering, that software environment is increasingly dynamic and ephemeral. This presents its own acute tracking challenges.
A new way to improve the effectiveness of your CMDB is to integrate it closely with a CAASM platform. The two platforms are highly complementary; one is a dedicated dataset, the other is a discoverer and aggregator of disparate datasets throughout the environment, typically using API connections. As well as the CAASM tool ingesting CMDB data for cybersecurity use cases, bi-directional connectors can also publish newly discovered, and validated data back into the CMDB, improving the completeness and accuracy of that dataset.
For example, automated rules can be configured so that when CAASM discovers data about the environment that reaches a high enough threshold of reliability, that data can then be published back into the CMDB. By increasing trust in the CMDB, different stakeholders in IT asset management can concentrate on agreeing next steps around one trusted dataset rather than waste time arguing about the merits of their own dataset versus someone else’s.
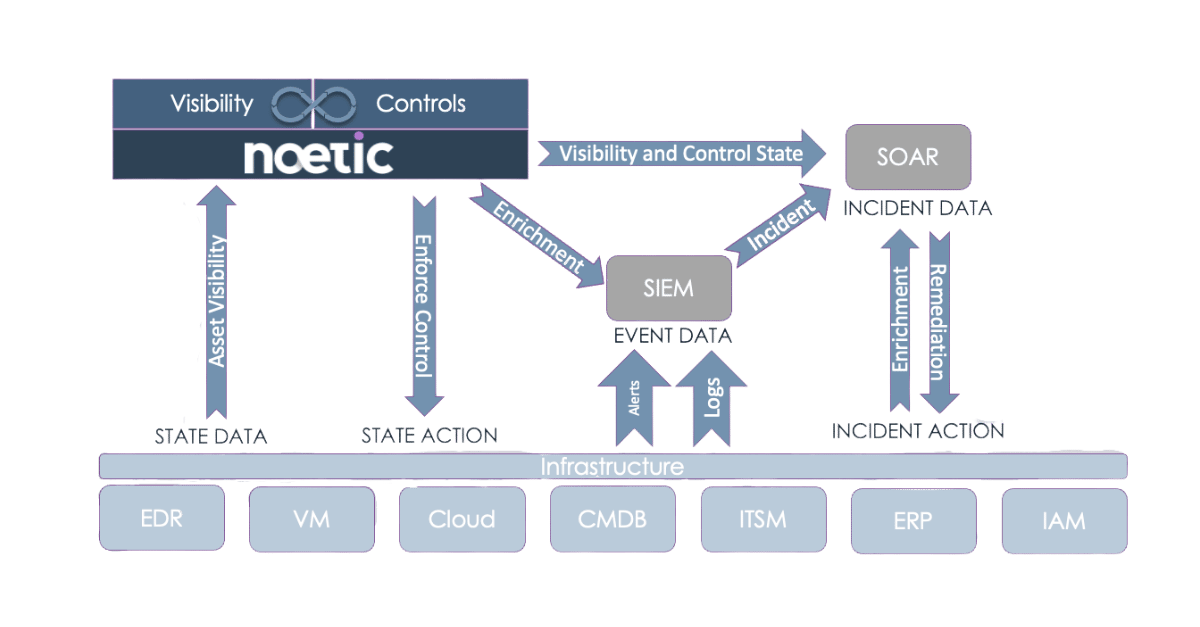
As more security teams adopt CAASM solutions to drive core security use cases such as eliminating security coverage gaps, or driving vulnerability prioritization, the opportunity exists for security and IT teams to collaborate on improving data hygiene and efficacy across both domains.
Customers have deployed the Noetic platform alongside market leading CMDB solutions from vendors including ServiceNow, Device 42 and more. To understand more about how these integrations can drive productivity, register for an upcoming live demo.
