Crawl, Walk, Run: The Evolution of Cyber Asset Management (Part I)
In this 3-part blog series, Jee Chung, Senior Solutions Architect at Noetic Cyber, applies his vast industry experience to share how organizations can not only maximize the operationalization of their existing security tools, but also mature into a proactive approach to cyber asset and vulnerability management.
Crawl: How to Build and Maintain Dynamic Asset Intelligence
One of the biggest challenges organizations still face today is also one of the most fundamental in cybersecurity, understanding what exists within their environments, and what they are responsible for. As more compute layers get introduced, cyber asset visibility becomes harder to achieve.
It is well understood that the attack surface has become more complex to manage. As more assets are added—both known and unknown—the adversary now has more opportunity than ever before, and the gap between offense and defense continues to widen.
The Current State of Attack Surface Visibility
The way in which we inventory and monitor assets must evolve alongside our attack surface. However, statistics show that little progress has been made in our ability to understand our digital infrastructure.
- Less than 1% of organizations have visibility of at least 95% of their assets.
- Only 45% of organizations have advanced asset intelligence with visibility and insight for over 75% of their assets.
- 80% of organizations are pursuing a hybrid or multi-cloud strategy, and many organizations are experiencing qualified staff, infrastructure and misconfiguration visibility, and control automation cloud protection challenges.
- An average cyber asset inventory takes 90 hours to complete.
- Difficulty coordinating activities among hybrid environments is the No. 1 challenge in understanding IT asset inventory.
Rather than continuing to throw money at the problem, security leaders need to recognize that despite significant investments, something isn’t working. It’s now up to them to create a sense of urgency around evolving their Attack Surface Management (ASM) processes beyond legacy asset inventories.
“New ways of visualizing and prioritizing management of an organization’s attack surface are required as enterprise IT becomes more dispersed, owing to the expansion of public-facing digital assets and increased use of cloud infrastructure and applications. Security and risk management leaders can start by aggregating asset and risk context into a platform for visualization of their attack surface.”
—Gartner, Innovation Insight for Attack Surface Management
The Problem with Traditional IT Asset Management
According to guidance from the Cybersecurity & Infrastructure Security Organization (CISA), a structured asset management process considers all internal and external assets, including but not limited to its people, information, technology, and facilities. So, this needs to consider:
- People, including your employees, contractors, vendors, and visitors
- Customers, including contact and purchase information
- Technology, including IT systems, networks, and communications
- Information. Including employee PII, business sensitive or proprietary
- Facilities and equipment, including buildings, vehicles, and machinery
- Systems, including alarm, SCADA
- Processes, including the supply chain
Most legacy inventory systems weren’t designed for the modern attack surface, and are primarily focused on technical information. As well as this, the pace at which new assets are being created, changed, and deleted makes it impossible to effectively manage this within a Configuration Management Database (CMDB) or related asset inventory tool.
Therefore, security analysts are often storing tens of thousands of records in spreadsheets with no efficient or foolproof way to combine the data. It then becomes impossible for organizations to keep up to date on what’s going on with all its known devices—never mind the unknown, cloud, or on-premises assets.
How to Maintain Dynamic Asset Intelligence with Noetic
Most of what organizations need to achieve the right level of visibility to combat the growing threat landscape is already in front of them. They don’t need another siloed dashboard of incomplete data, but a better way to compile information from their existing databases.
Noetic’s Cyber Asset Attack Surface Management (CAASM) platform was designed to meet that need by providing teams with actionable intelligence to highlight critical areas of risk, and to accelerate resolution.
How it Works:
Noetic’s agentless API connectors ingest data from virtually any source. The platform gathers asset data from existing security and IT management tools, and it also processes information from existing catalogs and spreadsheets, as well as external intelligence feeds such as NIST NVD, CIRCL CVE, FIRST EPSS to add important context on business criticality and context. If a connector doesn’t already exist, then the Noetic team will work with you to build it.
Some examples of pre-built connectors include:
- SentinelOne
- Rapid7
- runZero
- Tenable
- AWS
- Azure
- Okta
- Microsoft SCCM
- ServiceNow
Once data is ingested, Noetic automatically deduplicates and cross-correlates records to eliminate blind spots, significantly reducing the workload involved with manually sifting through and analyzing data in spreadsheets.
Finally, Noetic presents a cleansed, curated set of data that enables teams to maintain visibility into the current state of their assets, and continuously monitor for changes.
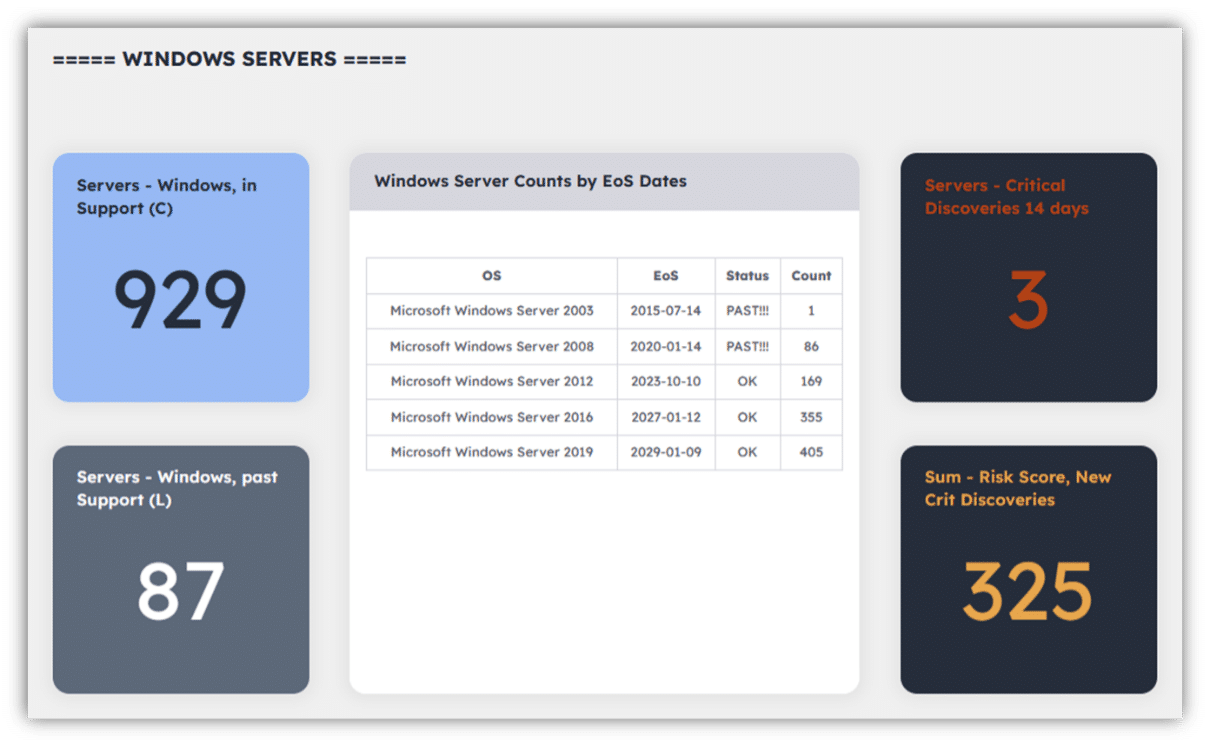
The Benefits of Automated Asset Discovery
- Provides actionable insights
Security teams don’t need more tools to fix their problems. Rather, they’re missing the actionable insights that highlight critical issues—causing them to get lost in the noise. Noetic enables teams to experience immediate time to value and eliminate the burden of disparate, siloed tools with simple setup and agentless API connectors.
- Significantly reduces workload
The average IT asset inventory requires about 90 hours and dozens of tools to complete. According to research, security teams spend over half of their time generating reports. Noetic gives teams back the time they need to focus on value-added tasks, while also ensuring they stay up to date on their security hygiene.
- Reduces the financial impact of individual security incidents
According to Gartner, organizations that adopt a cybersecurity mesh architecture to integrate security tools, so that they work together as an ecosystem, will reduce the financial impact of individual security incidents by 90%, on average. That’s significant savings, considering the average cost of a data breach in the U.S. is over $5 million.
- Optimizes SaaS spend
Intelligence is the core of any modern ASM program, but conflicting sources makes it difficult to identify the quality of data for any given tool. By compiling and comparing data from multiple sources, Noetic enables organizations to gauge, reassess, and optimize their SaaS spend.
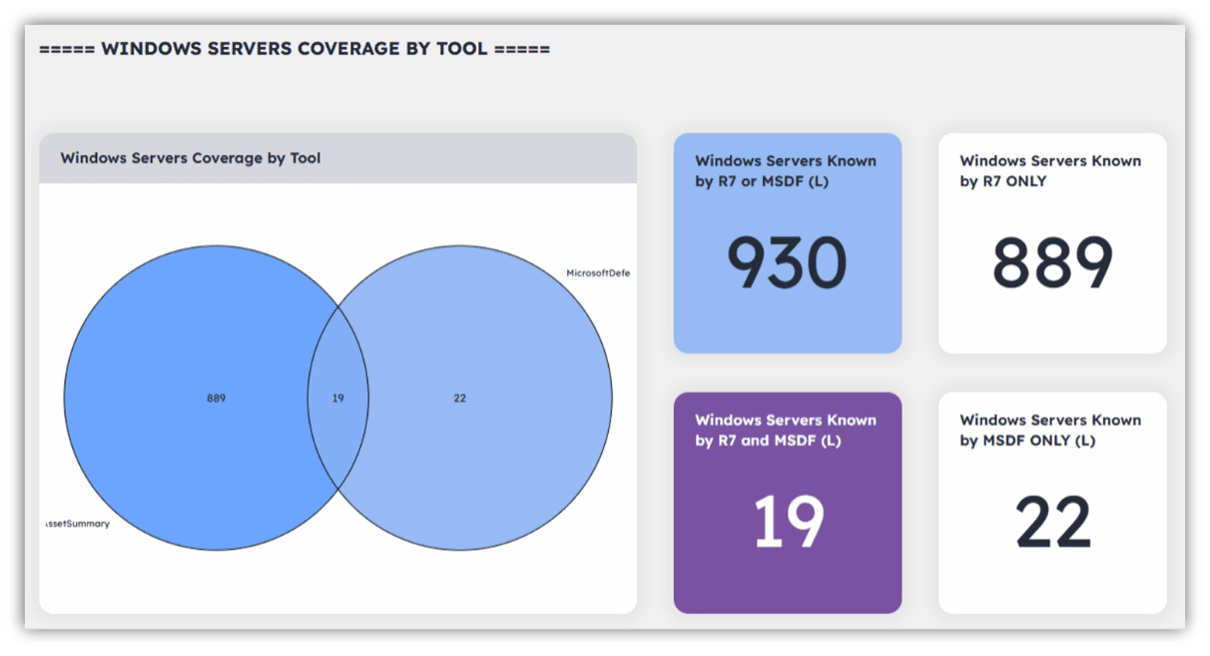
The level of understanding an organization has of its attack surface determines how effective it will be in defending itself from attackers. Ultimately, visibility is necessary for organizations to maintain a secure environment, ensure the safety of their data and systems, and keep business running as usual.
Want to see the Noetic platform in action? Register here for an upcoming live demonstration.
More in this series:
Walk: Risk-Driven Vulnerability Prioritization
How context and intra-asset relationships effectively enables vulnerability prioritization.

Walk: Risk-Driven Vulnerability Prioritization
Run: Embracing Security Automation
How users are leveraging Noetic for continuous controls monitoring (CCM) and automated remediation.

