What’s New in the 2024 Gartner® Innovation Insight: Attack Surface Management
Despite many advancements made over the past few years, we believe that many challenges around attack surface and exposure management remain true: “Organizations have to manage a growing attack surface as their technological environments become increasingly complex and dispersed, both on-premises and in the cloud. SaaS applications and supply chain touch points are expanding the attack surface. Containers and cyber-physical systems, such as the Internet of Things, are also presenting new attack surfaces.”
According to the 2024 Gartner® Innovation Insight for Attack Surface Management report, “Traditionally, attack surface solutions have focused primarily on identifying deficiencies in the security hygiene of externally visible assets. These solutions are quickly expanding beyond those traditional assessments of externally facing client-owned technologies to focus on brand risks, reputational risks, and risks from SaaS and third-party systems.”
“ASA technologies and capabilities are gaining momentum across emerging markets, such as CAASM, and consolidating markets, such as VA. These technologies help organizations assess more of their attack surface efficiently and prioritize risks affecting both controlled and uncontrolled digital assets.”
A key recommendation from the report states that, “Security and risk management leaders responsible for managing their organization’s attack surface as part of the security operations function should: Invest in attack surface solutions in line with objectives for broader exposure management processes and programs, such as continuous threat exposure management (CTEM).”
Attack Surface Management vs. Attack Surface Assessment?
The Gartner perspective is “although commonly understood, “attack surface management” (ASM) is an inaccurate term to describe technologies and services that continuously discover, inventory and contextualize an organization’s assets. Assets can be both physical and digital, both internal and external, and either owned or part of a subscription. Discovering, inventorying and contextualizing is an assessment process, rather than a management one. Thus, “attack surface assessment” (ASA) is a more accurate term.” Despite this clarification, for the sake of consistency, we’ll continue to use the widely recognized acronym ASM throughout this blog.
The Core Elements of Attack Surface Management
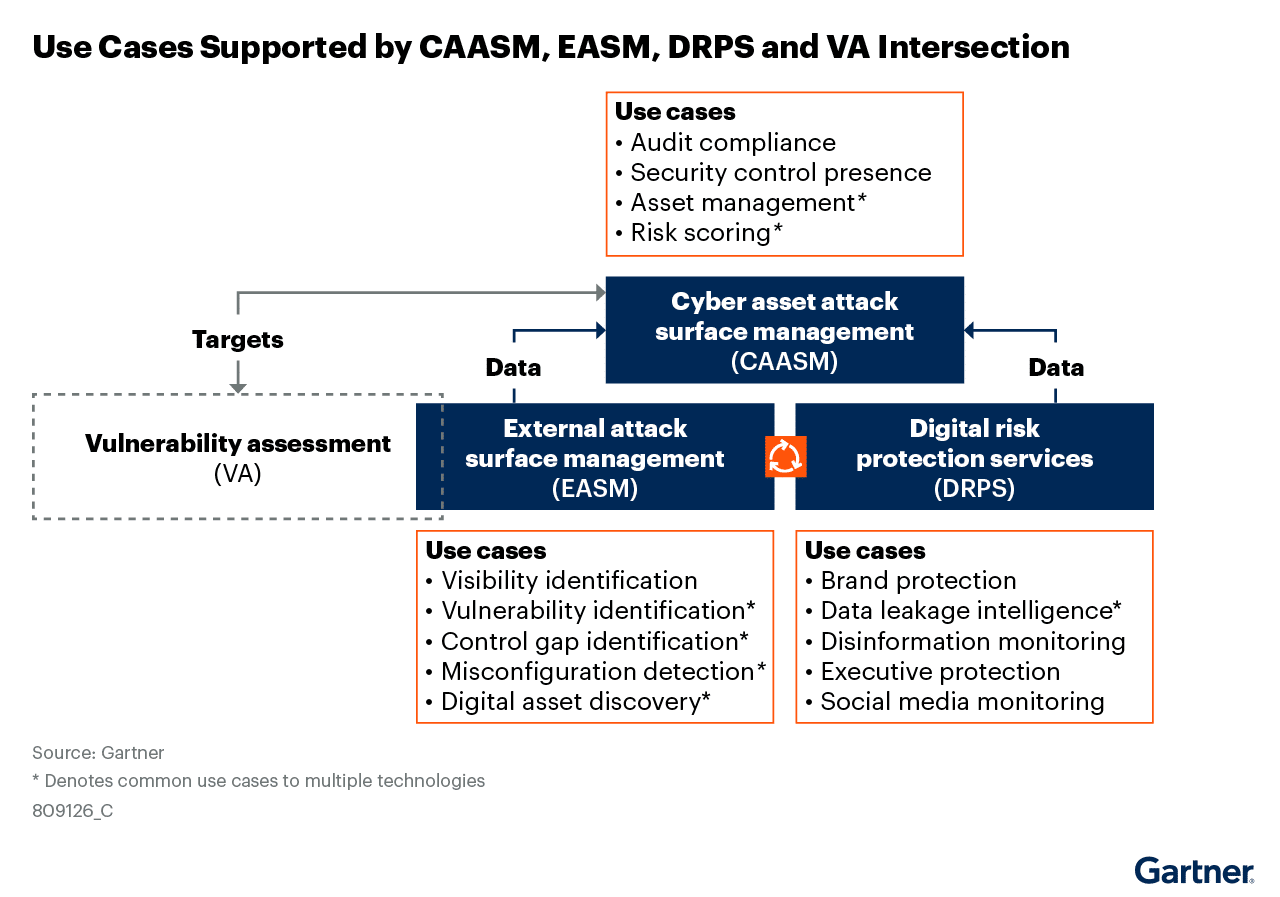
We think attack surface solutions continue to serve as one the foundational pillars within a broader exposure management landscape. These ASA tools are delineated into three primary technology areas, including cyber asset attack surface management (CAASM), digital risk protection services (DRPS) and external attack surface management (DRPS).
“Most ASA technologies provide two categories of capability”:
- “Visibility: Broadening the scope of assets covered and creating awareness of the cyber risks that increased attacker visibility may place on those assets.”
- “Attractiveness: Assessing the appeal of a particular asset and the possibility that it may be targeted by a third party.”
“Some confusion about these three persists, however, owing to the overlap in some of the use cases they support:
- EASM has a more technical and operational focus. It supports security operations professionals engaged in activities such as VA, penetration testing and threat hunting. Some EASM providers are also consolidating with breach and attack simulation (BAS), VA technology, and other security technology providers through acquisitions.
- DRPS, in contrast to EASM, primarily supports more business-centric activities, such as enterprise digital risk assessment, compliance, and brand and executive protection. Another important distinction between EASM and DRPS is that the latter typically provides a service overlay to execute functions such as takedowns.
- CAASM operates differently. Its discovery function works mainly by integrating with existing IT tools through APIs, as opposed to scanning or probing systems anonymously. Because CAASM has greater access to internal environments, it generally provides richer, more reliable data. However, the completeness of the asset inventory populated by CAASM is dependent on the quality of the organization’s existing data sources.”
Key Benefits & Uses for Attack Surface Assessment Solutions
“A secondary aim of CAASM is to provide a holistic view of an organization’s asset inventory (CMDB), reconcile duplicate or inconsistent data, and enable some automated steps to update data.” Additionally, Gartner underscores several other benefits in their report, such as:
- “Improving asset visibility enables organizations to avoid blind spots and unmanaged technology (such as “shadow IT”), thus strengthening their security posture and supporting more comprehensive risk management.”
- “Actionable intelligence and meaningful metrics are gained from ASA technologies and can be tracked over time. These help demonstrate the value of making CTEM a part of the cybersecurity program.”
- “Quicker audit compliance reporting is enabled by more accurate, current, and complete asset and security control reports.”
- “Better prioritize exposure risks in vulnerability management and exposure validation processes.”
” ASA reduces resistance to data collection and enables a broader understanding of shadow IT organizations, installed third-party systems and line-of-business applications where IT lacks governance and control.” In our experience, this 360-degree visibility is a huger benefit to security teams who can only protect what they know about.
How Noetic Cyber™ helps organizations assess and manage their Attack Surface.
“Gartner estimates that less than 25% of organizations have adopted one or more ASA technologies to address their attack surface. Many rely on partial or manual ASM processes to assess their assets and any associated exposure.” We believe this means that a significant number of organizations are still relying on manual approaches for attack surface visibility and exposure management.
We think Noetic Cyber, named as a Representative Provider in the ‘Pure-Play CAASM vendor category, is well positioned to help security teams adopt a programmatic approach to attack surface management. We help customers to better understand their security posture and cyber risk with our data centric focus on CAASM. We help organizations to:
- Be confident in the accuracy and relevance of their security data.
- Prioritize their exposure workload based on risk-based insights driven by their data.
- Act on the most important security findings in their data.
Our innovative approach to attack surface and exposure management allows customers to achieve the benefits highlighted by Gartner in this new research. To learn more, access your complimentary copy of the report below.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner, Innovation Insight for Attack Surface Management, Mitchell Schneider, John Watts, Pete Shoard, April 2024
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
