Oil, Gas & Utilities: Fueling the Future of Cybersecurity
The 2023 State of Security Hygiene and Posture Management for Oil, Gas & Utilities
With its increasing interconnectedness and reliance on OT/IoT devices, growth in adoption of cloud computing, and remote access solutions, the oil, gas, and energy sector has seen a significant expansion of its attack surface—necessitating robust security hygiene and posture management (SHPM) practices.
To better understand the current state of SHPM and where the industry’s cybersecurity professionals can adjust, we dissected the results from ESG’s latest comprehensive survey sponsored by Noetic Cyber.
Cybersecurity Best Practices for the Energy Sector
The oil, gas, and utility sector has witnessed a huge surge in cyberattacks in recent years, driven by its economic importance and role in critical infrastructure. High-profile incidents, such as the Colonial Pipeline ransomware attack in 2021, also clearly illustrate the real-world impacts of a major cyber incident in this sector. Recent reports indicate that oil assets have become the biggest targets for hackers, accounting for one-third of all incidents since 2017. To combat the evolving threat landscape, we’ve identified a few of areas of immediate opportunity for IT and cybersecurity professionals in oil, gas, and utilities.
Identify your organization’s most critical assets.
By identifying business-critical assets, security teams within oil, gas and utility organizations can focus their efforts on safeguarding and protecting them. This understanding enables proactive threat detection and effective vulnerability prioritization to build organizational resilience that ensures continuous delivery of essential services.
Despite it being especially important for critical infrastructure organizations to understand their most business-critical assets, these companies are more likely to struggle to do so. Nearly one-third (32%) of respondents from oil, gas, and utility organizations “strongly agree” their organization sometimes struggles to understand which assets are business-critical. Although they’re joined by 18% of their fellow respondents, 10% of those from other industries strongly disagreed with the statement.
Leverage the full potential of security automation.
According to the survey, nearly every oil, gas and utility company has introduced automation to some extent. While this is promising, there’s a clear difference in the rate of adoption between the Energy sector and other respondents. While 43% of other organizations have extensively automated SHPM activities, only 23% of the oil, gas and utilities had the same response.
It is understandable that security leaders want to avoid relying too heavily on automated tools and processes that could accelerate broken processes and increase the potential for malicious exploitation. These concerns are valid, as automation can sometimes lead to false positives, false negatives, or oversights that human analysts might catch.
However, it is crucial to acknowledge that the benefits of automation outweigh the risks. Automation can significantly enhance efficiency, accuracy, and response times in identifying and mitigating threats. It allows security teams to focus on strategic and complex tasks, while repetitive and time-consuming activities are handled by automated systems. To strike a balance, security leaders should consider adopting automation at a comfortable pace, ensuring proper oversight, regular assessments, and human involvement in critical decision-making processes.

Ensure resources are allocated properly.
Because these organizations are less mature in their security hygiene automation processes, they spend more time on data discovery and classification. As a result, this leaves less time for key activities such as security testing or attack surface scanning. While more than half of all other industries are conducting comprehensive security testing at least weekly, most (62%) oil, gas and utility companies are operating on a monthly cadence.
Therefore, oil, gas, and utilities should consider security testing as the next step on their automation journey. In addition to saving time and effort by executing repetitive tests and tasks, automation facilitates the testing of complex scenarios and edge cases that are often challenging to replicate manually. By simulating attacks and vulnerabilities at scale, automation eliminates the likelihood of human and uncovers security weaknesses that may otherwise go undetected.
Consolidate as much as possible.
Every second counts—especially when it comes to safeguarding the world’s critical infrastructure. The less time teams spend on manual data extraction and aggregation, the more time they can spend on detecting and mitigating exposures as they come up.
Despite other industries having landed on automation as the primary driver, more than half (51%) of professionals from oil, gas and utilities agree the No. 1 action that would improve SHPM would be to consolidate all related data into one repository as a single source of truth. Inherently, this would increase the ability to keep tabs on an ever-changing and expanding attack surface—which is more of a challenge for this sector than its counterparts (see table below).
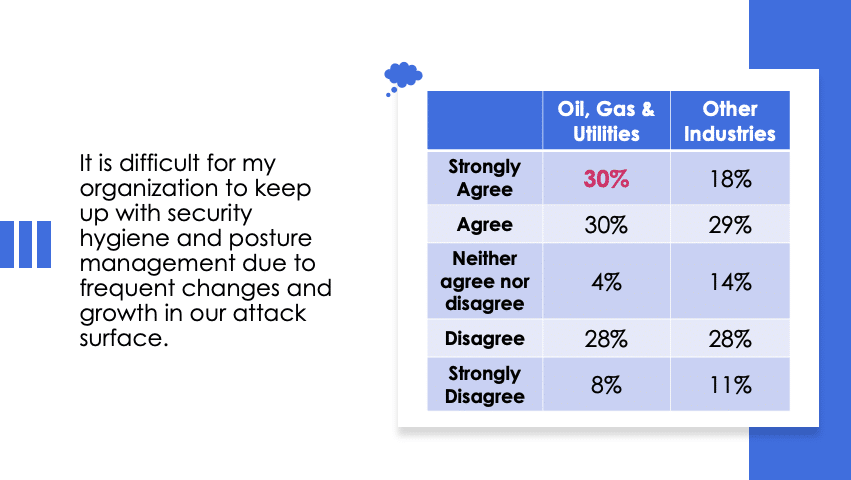
By aggregating and consolidating data from different security sources, organizations break down existing data siloes to enhance accessibility, collaboration, and analysis. A “single source of truth” that is continuously updated and always accessible by the security team will significantly reduce the workload associated with today’s data disbursement challenge, and facilitate better decision-making by using the most up-to-date, comprehensive view of your attack surface.
The modern threat landscape demands an adaptive and proactive approach to security to ensure the protection of assets, maintain operational continuity, and safeguard the world’s most critical infrastructure. More responsibility falls under security and risk professionals within the oil and gas sector, requiring them to adapt security hygiene and posture management activities to effectively combat the evolving threat landscape.
Discover more key findings from ESG’s latest security hygiene and posture management survey in the full report: Security Hygiene and Posture Management Remains Decentralized and Complex.
About the Research: The original survey collected responses from 383 IT and cybersecurity professionals representing organizations within North America. We compared the 53 responses from the oil and gas and utilities sector to the 330 that represented all other industries.
