Crawl, Walk, Run: The Evolution of Cyber Asset Management (Pt II)
In this 3-part blog series, Jee Chung, Senior Solutions Architect at Noetic Cyber, applies his vast industry experience to share how organizations can leverage the Noetic platform to maximize visibility, better prioritize threats and exposures, and maximize the efficacy of their existing resources.
Walk: Risk-Driven Vulnerability Prioritization
Threat and vulnerability management (TVM) is a vicious cycle. By the time teams get through their current backlog of exploitable vulnerabilities, they now need to detect, prioritize, and remediate the hundreds more that have since been added. That’s why despite throwing more money into staffing and tooling existing programs, organizations have made little progress in truly reducing risk because of their inability to prioritize effectively.
Rather than continuing to invest in a broken system, security and risk leaders are starting to replace technology-driven TVM with continuous threat exposure management (CTEM). These programs are intended to keep the business aligned as one operating unit with the shared goal of keeping tabs on the current state, while working towards a desired state.
The Current State of Threat and Vulnerability Management
Today, most organizations have a backlog of more than 100,000 vulnerabilities, and most professionals agree their immense vulnerability backlog is caused by the inability to effectively prioritize what needs to be fixed. Before we explore how Noetic is solving the vulnerability prioritization problem, let’s explore why it’s such a challenge for teams to begin with.
- The overwhelming volume of critical vulnerabilities
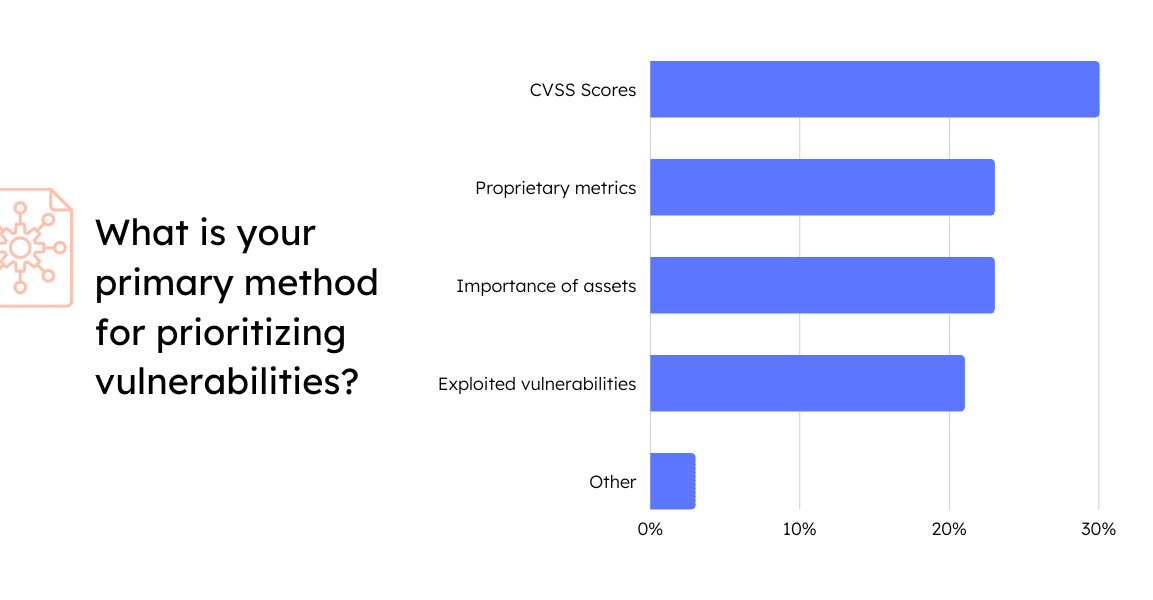
As attack surfaces expand, the threat landscape continues to grow. The number of critical vulnerabilities (those with a CVSS score ≥9.0) increased nearly 50% in 1H 2022 compared to 1H 2021. But just because a vulnerability is critical, doesn’t automatically mean it’s exploitable by attackers. Yet, despite the lack of business context CVSS scores provide, they’re still the No. 1 method used for vulnerability prioritization efforts.
- Error-prone, manual tracking systems
Ad-hoc spreadsheet systems, commonly used by many organizations to track vulnerabilities and remediations, lack efficiency and accuracy. Environments are ever-changing, and new critical vulnerabilities are constantly introduced. In the time it takes to investigate and document your remediation efforts, the initial inventory could be completely outdated. So, despite the tireless efforts of security and risk teams, it still takes an average of 215 days to patch a reported vulnerability.
- Miscommunication and turf issues
Most professionals indicate not having an efficient way to track whether vulnerabilities are being patched in a timely manner. Although Vulnerability Management (VM) and Attack Surface Management (ASM) initiatives are top-of-mind for organizations, teams are still struggling to get on the same page. In turn, 60% of data breaches are successful due to the inability to apply a known, available patch prior to exploitation.
- Delayed incident response caused by data siloes
As discussed in our ebook with SentinelOne, 30% of enterprises are now using more than 50 tools and technologies for security. However, with no efficient way to combine and correlate that data, even just two sources of vulnerability data can become unmanageable.
Nearly half of DevSecOps professionals agree that not having a common view of applications and assets across security and IT teams causes major delays in the vulnerability patching process.
How to Streamline Vulnerability Prioritization with Noetic
Although dozens of security tools are already running across the average enterprise, most DevSecOps professionals agree the lack of effective security tools is the biggest obstacle when it comes to maturing their program. The problem then isn’t lack of data. Rather, it’s the lack of correlation between your existing data sources.
As discussed in part one of this series, there are many benefits to using the Noetic platform to achieve dynamic asset intelligence. The cleansed, curated asset inventory serves as a foundation for all cybersecurity efforts. The platform’s ability to aggregate and correlate data across disparate systems and data sets provides immediately value to TVM professionals.
This empowers users to prioritize vulnerabilities by:
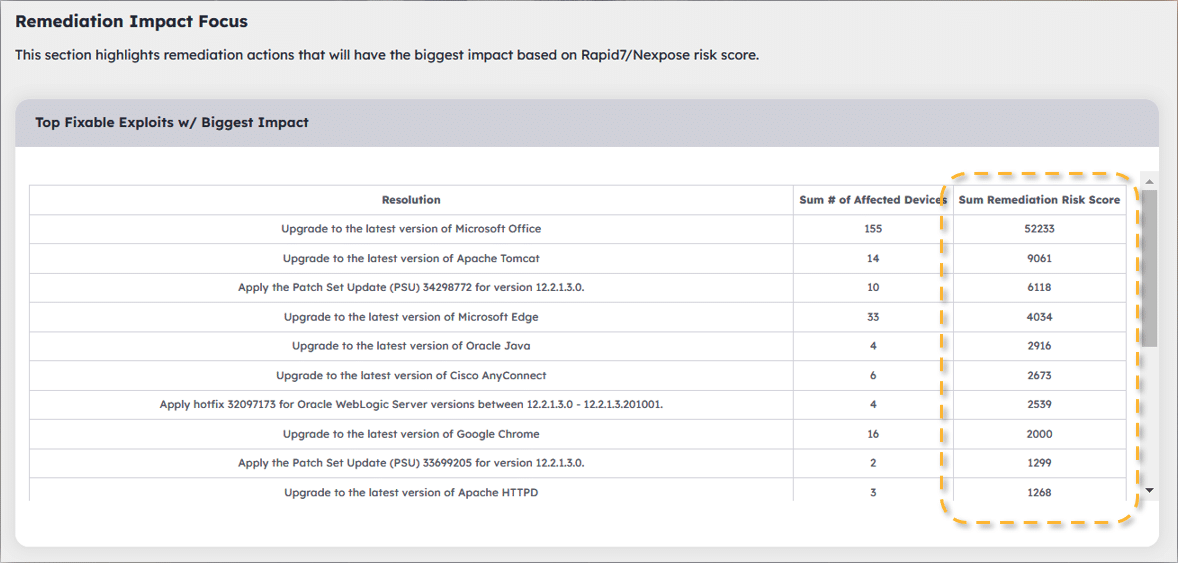
- Displaying the aggregate risk score for each fixable exploit across their entire attack surface to help teams identify the actions that will drive the most positive impact based on the product of the proprietary risk score for each fixable exploit (gathered from your existing VM tools), and the number of machines impacted.
- Automatically assigning remediation actions to owners, assigning vulnerable business units to the appropriate responsible party by cross-correlating data across disparate datasets. This ensures teams know exactly what they’re responsible for, eliminating the delays in patching caused by miscommunication or missing ownership information.
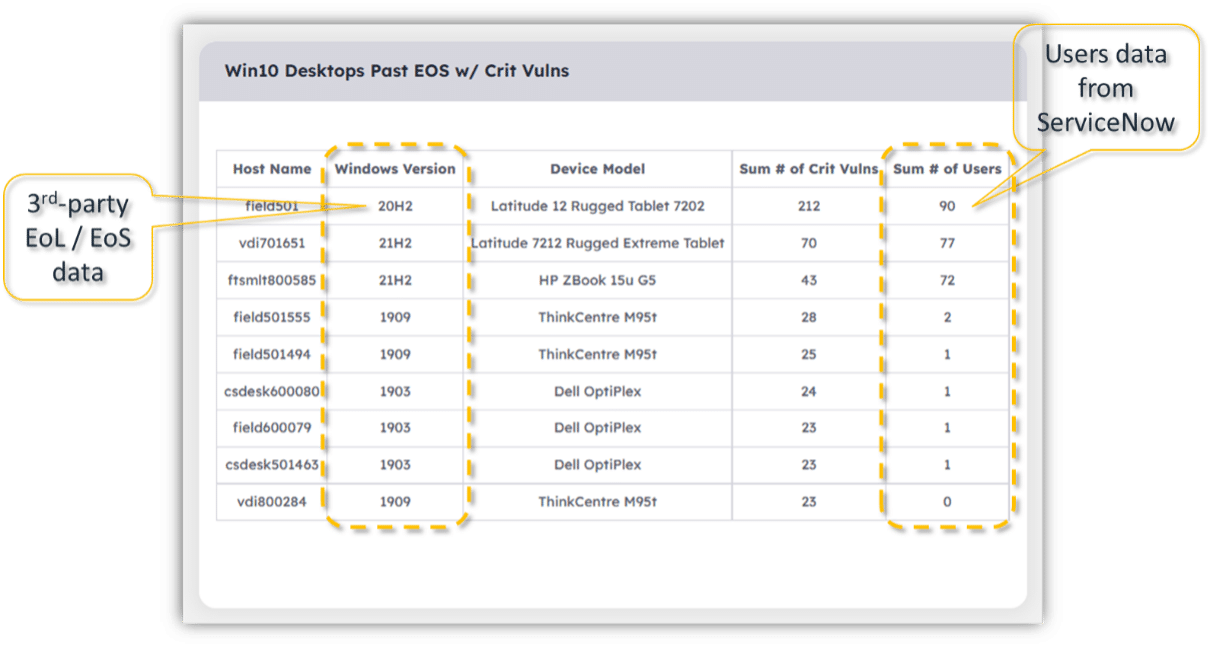
- Connecting with existing databases and/or IT Service Management (ITSM) tools to indicate the number of users accessing a vulnerable device, enabling teams to understand the potential magnitude of a security incident.
Vulnerability scanners on their own do a good job of highlighting high-risk areas amongst known assets with proprietary risk scores. External intelligence feeds such as CISA can offer additional guidance based on actual observations in the wild. Nonetheless, the problem with today’s vulnerability intelligence is that it tends to only assess risk from two dimensions: severity and exploitability.
As insightful as CISA’s Known Exploitable Vulnerabilities (KEV) catalog and FIRST’s Exploit Prediction Scoring System (EPSS) are, severity and exploitability evaluate vulnerabilities from a theoretical, universal perspective. By combining layers of insights from disparate tools and datasets, Noetic empowers teams to shift to the other side of the “boom” with an understanding of risk beyond a proprietary score.
These use cases demonstrate how Noetic does the leg work to get your asset and vulnerability intelligence sources working together to expedite the discovery and response process. Now, let’s explore how customers are taking leveraging Noetic to mature their VM efforts even further.
The Importance of Cyber Cartography in CTEM
The goal of threat and exposure management is to know more about your environment than the adversary. However, most security and risk management platforms take a list-based approach to attack surface management.
Attackers, on the other hand, make the most of their time by going after not only your most accessible pathways, but also those that are the most interconnected. In other words, how can they cause the most damage, with the least amount of effort?
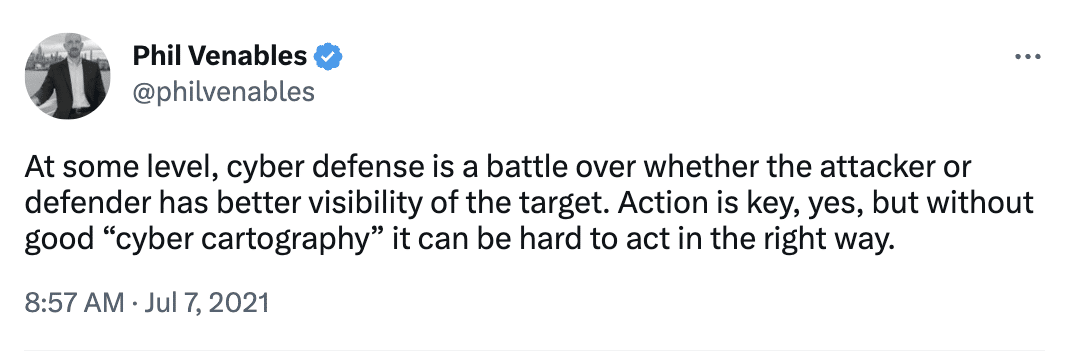
Until now, teams haven’t had an efficient way to continuously keep a pulse on their attack surface—never mind understand how assets interact with each other as well as the overall business.
How it Works:
Noetic’s graph-based architecture provides natural relationships between devices, networks, data, users, business applications, business owners, physical locations, security controls, vulnerability findings, and ITSM tickets, making it possible to ask questions and provide reporting on business and operational issues that are difficult to do in rigid relational databases.
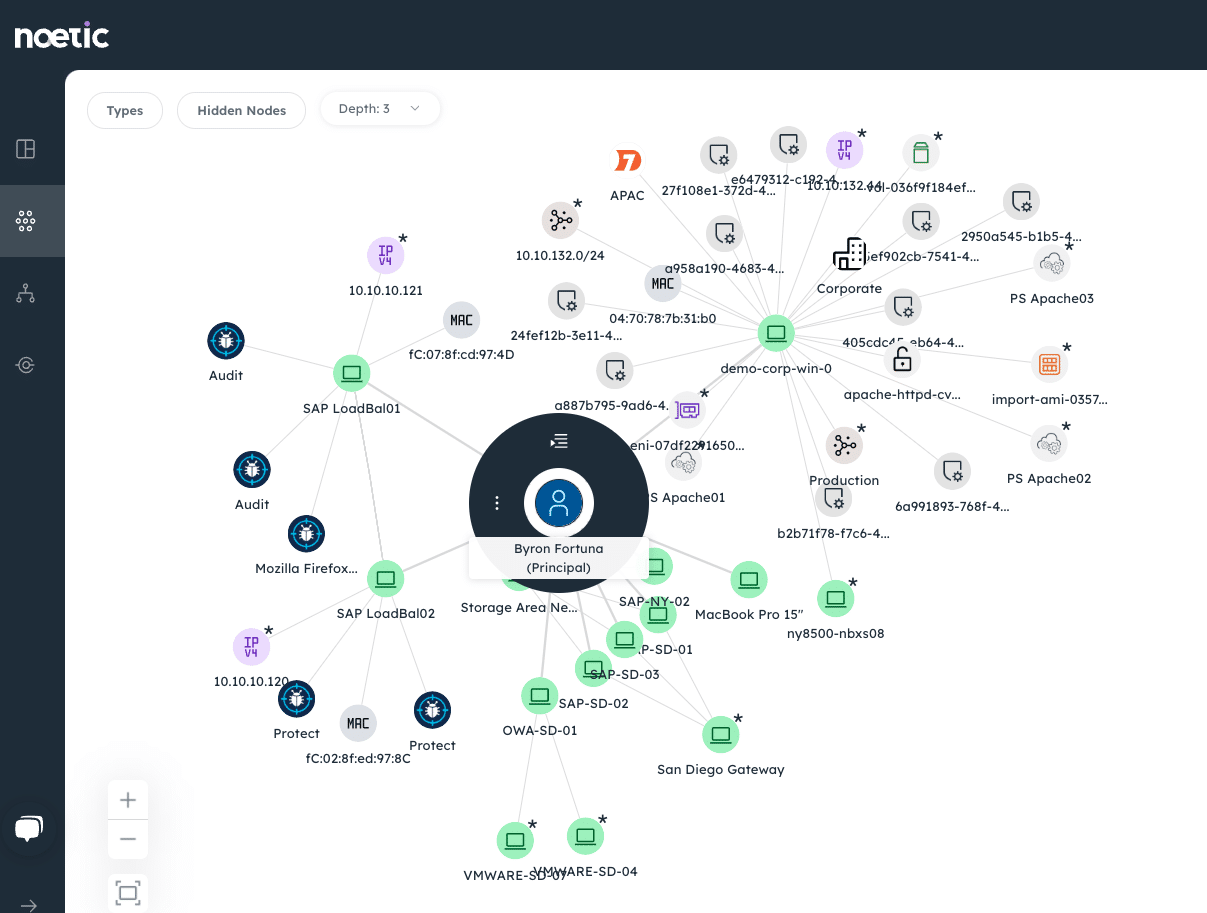
In providing continuous visibility into the security posture and relationships associated with each asset, Noetic enables teams to quickly decide which areas of risk require their immediate attention. This includes severity and exploitability, as well as a variety of other key contextual factors including:
- Blast radius to understand the highest potential impact based on the interconnectivity of each asset
- Location to determine how accessible it is to threat actors
- Access privileges to raise a red flag for could expose sensitive internal and/or external datasets
- Controls to help determine whether the vulnerability falls underneath at least one later of security
Similarly, custom reference data can be used enrich existing datasets with valuable business and operational data by layering ad-hoc datasets into the Noetic Unified Model. For example, a spreadsheet of network names will often follow a naming convention (e.g., dev/qa/prod, security zones, etc.). This can provide valuable context to assets provided by other sources, significantly expediting the time it takes to investigate and respond to an event.
The more data you ingest into the platform, the better your cyber cartography becomes, and the better your ability to effectively prioritize threats and exposures. Effective vulnerability prioritization then encourages security and risk teams to mature out of “reactive” cybersecurity. Organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.
To learn more about relationships and risk-driven vulnerability prioritization, register for our upcoming webinar with TAG Cyber.
More in this series:
Crawl: How to Build and Maintain Dynamic Asset Intelligence
How to build and maintain dynamic asset intelligence with CAASM

Run: Embracing Security Automation
How users are leveraging Noetic for continuous controls monitoring (CCM) and automated remediation.

